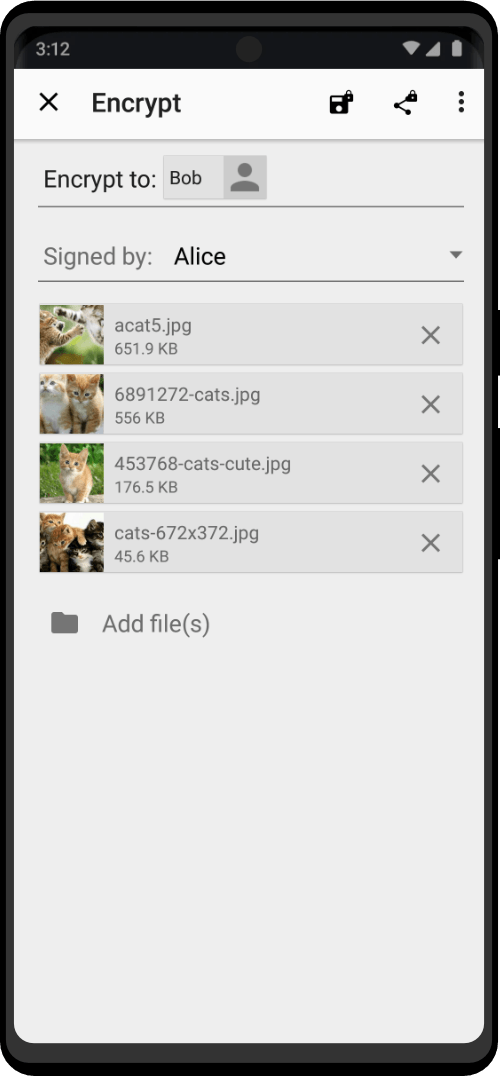
THE MOST SECURE PLUG & PLAY DEVICES FOR REMAINING ANONYMOUS
Zero Technical or Programming Skills Needed Stay Completely Anonymous - At Home Or On The Go
THE MOST SECURE PLUG & PLAY DEVICES FOR REMAINING ANONYMOUS
Zero Technical or Programming Skills Needed Stay Completely Anonymous - At Home Or On The Go
Industry Accolades
Zero Trace is the frequent recipient of industry awards and recognized as a leader in cybersecurity by independent testing organizations and industry analyst firms.

New Technological Advancement
Cybersecurity Experts Have Finally Found A Solution To Tor’s Vulnerabilities
Are You still using Tor Browser and a VPN? STOP! You already know you could expose yourself with one wrong click. Why leave it to chance?
Cybersecurity experts are redefining what achieving true anonymity really requires.
No longer are the days where you can easily expose your IP address with activities performed outside of the Tor Browser, or expose your identity by downloading and opening files. These vulnerabilities have finally been patched, as well as several other flaws.
You can now stop worrying about Windows & macOS logging your activities for “development purposes.” As well as 3rd parties from recovering your deleted data.
Cease the paranoia and start focusing on the task at hand!
Devices Powered By Decentralized Networks.
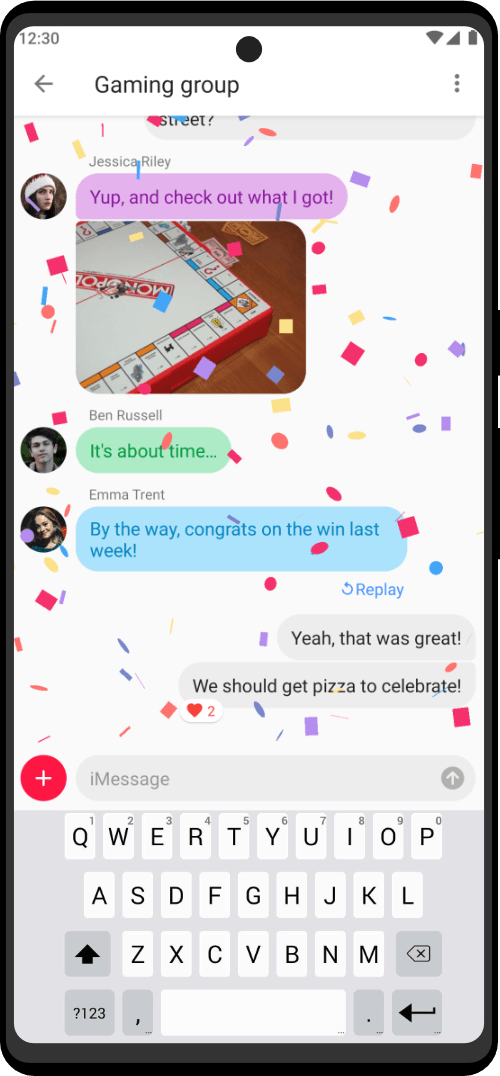
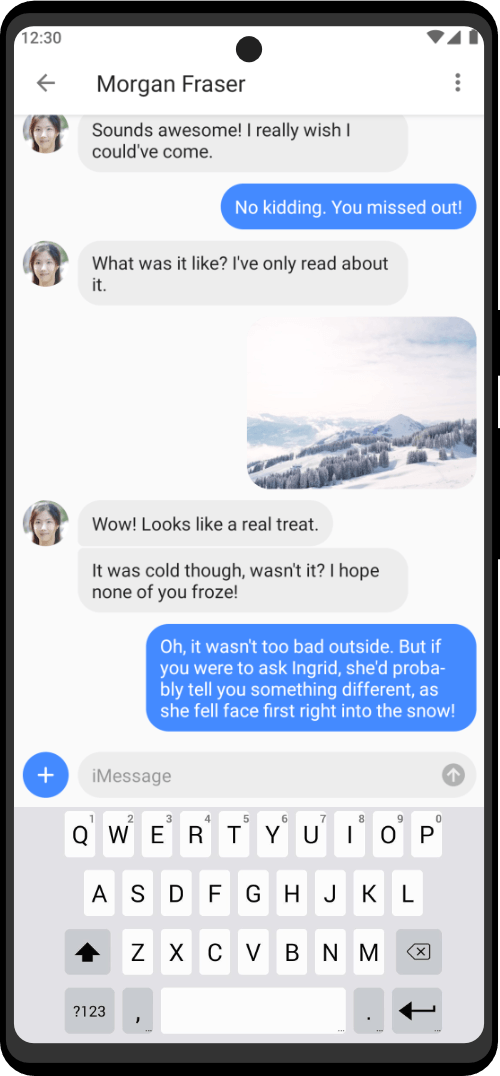
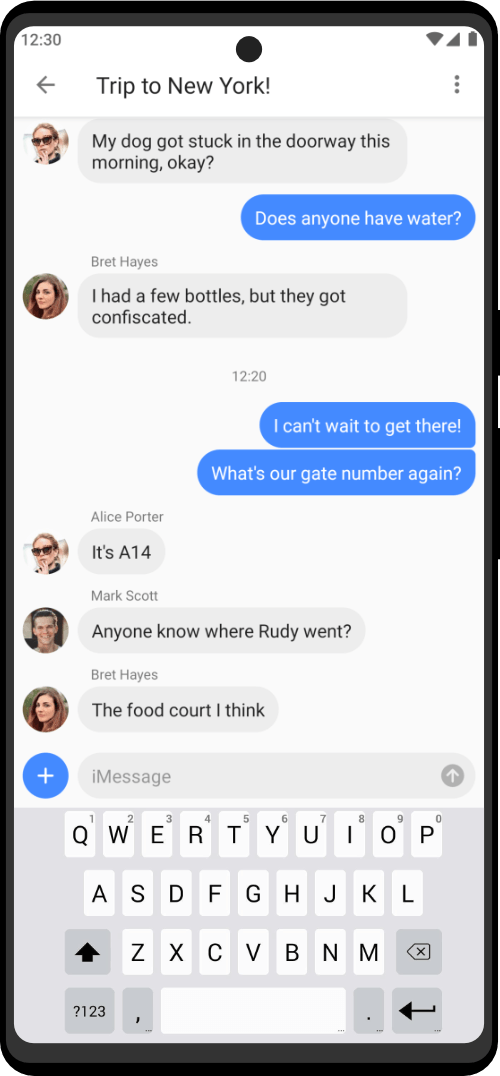
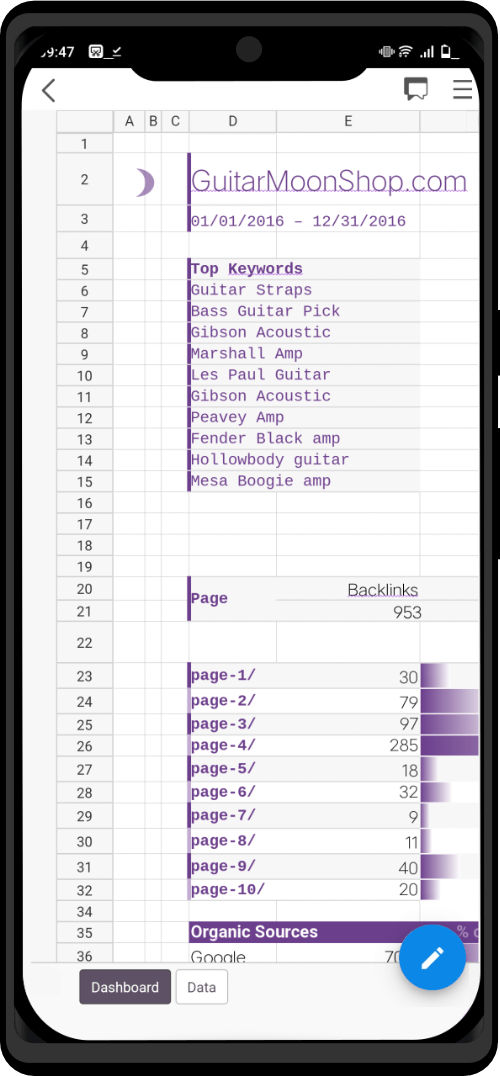
Choose between 40+ tools for every kind of white and black hat operation. Zero Trace devices provide a huge arsenal of protection against the multitude of cybersecurity attacks that occur everyday. Professionals can use to keep their privacy and anonymity by using Zero Trace devices. Zero Trace devices encrypt all your internet connections through 3 decentralized relays – making all of your activities anonymous and protected by default.
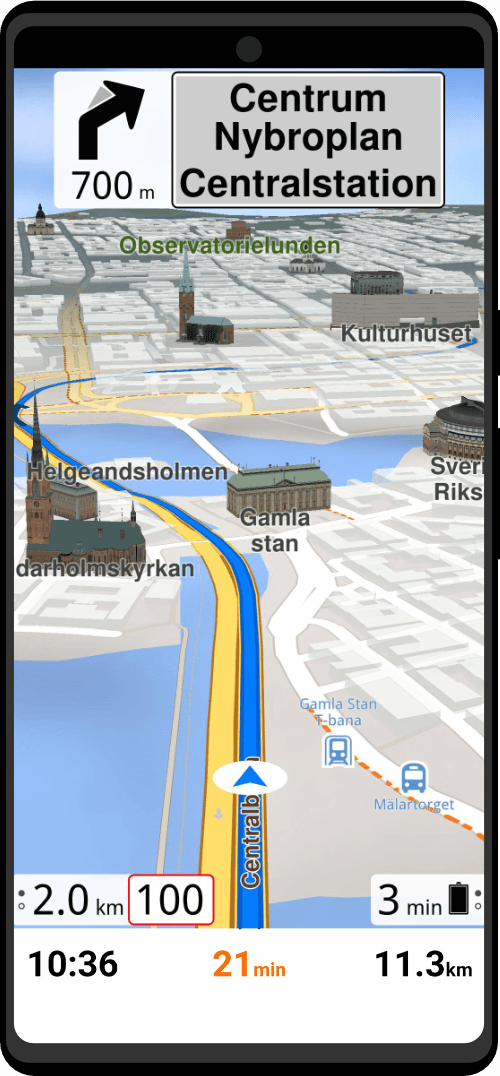
Zero Trace Pen®
All-in-One Tor Network Anonymous Flash Drive + Cold Storage Cryptocurrency Wallet
- Encrypted
- Secure
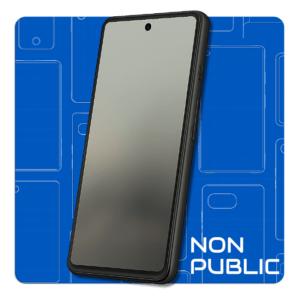
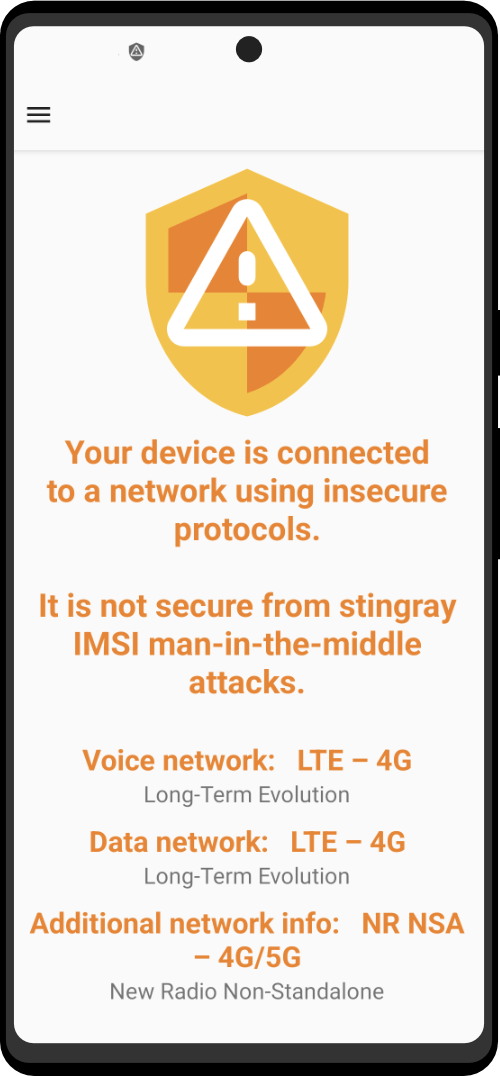
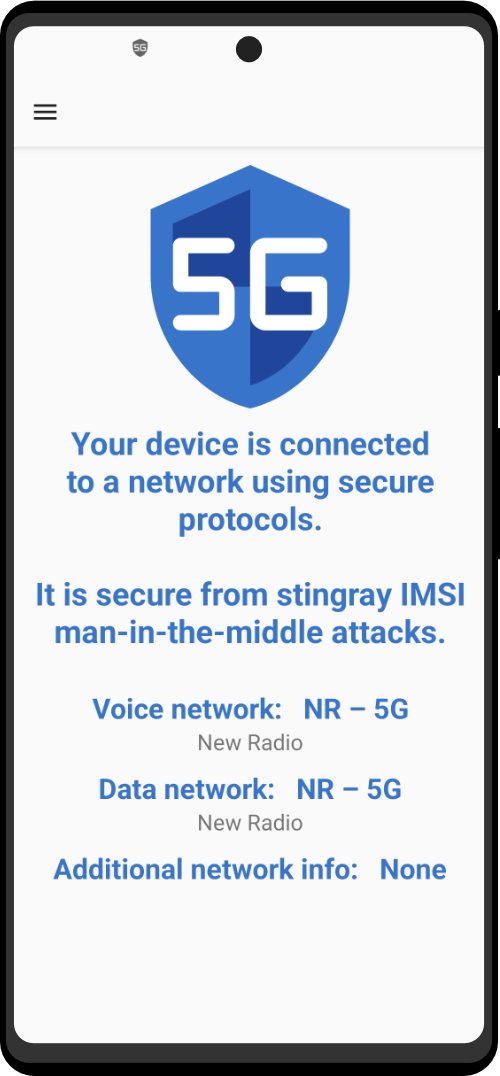
Zero Trace Phone®
All-in-One Tor Network Anonymous Phone
+ Anti-Surveillance Toolkit
- Encrypted
- Secure
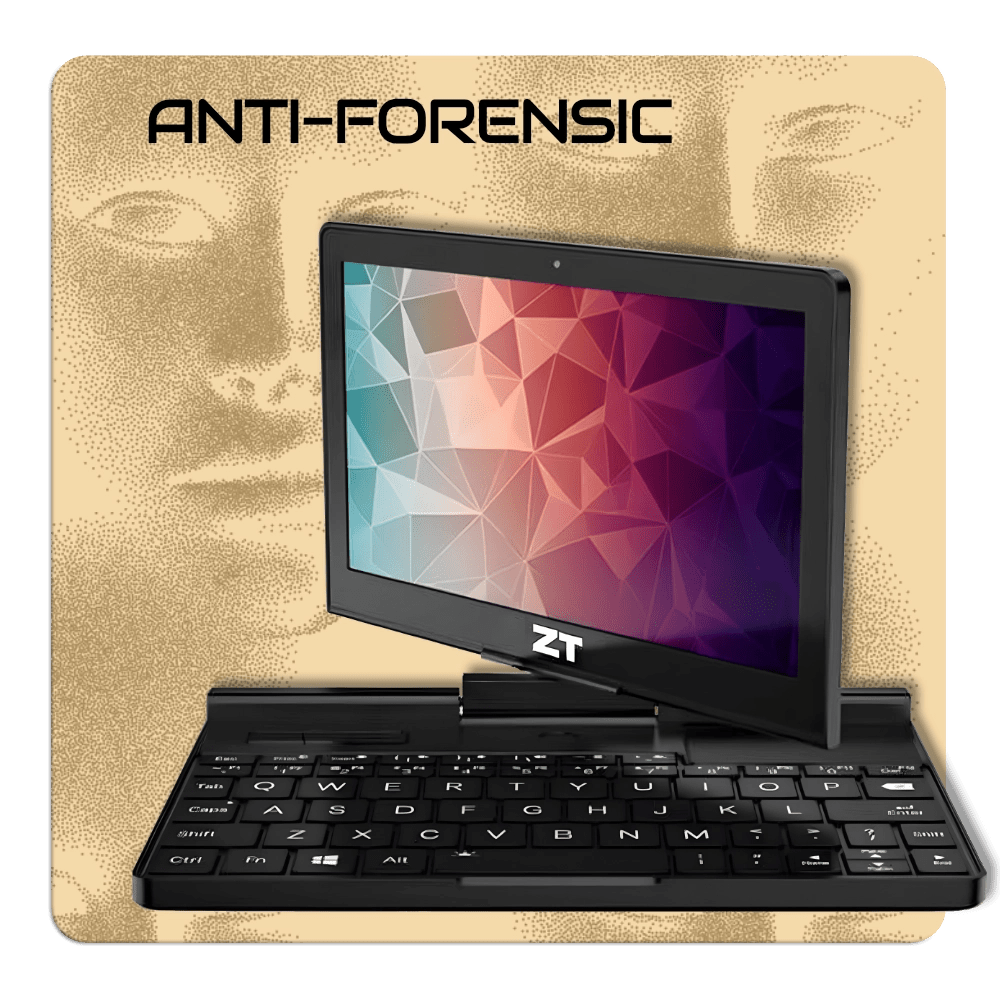
Zero Trace Laptop®
All-in-One Privacy Workstation +
Emergency Go Kit
- Encrypted
- Secure
Zero Trace Charms®
Jewelry For Those Who Need Luck On Their Side
- Future Benefits
- Support The Project
Who Is This For?
Zero Trace devices are used by people from all walks of life. Anonymity and privacy is must in several industries across the world. Whether you are working in construction or cybersecurity, privacy between you and your clients should not be compromised.

Gun Store Owners

Private Investigators

Construction Management

Cybersecurity Audits
In Partnership With

System Security
The system is designed from the ground up to be secure. Native support for full disk encryption, blazing fast security updates and a hardened core makes the system the perfect place to store sensitive data.
Powered by VeraCrypt
Privacy
Don't leave your sensitive data floating around unprotected. Our devices support full disk encryption, and the system lets you handle data in the most secure and reliable way. Zero Trace devices are free from trackers and telemetry "features", and it provides many privacy tools like a
double kill switch, Tor Firewall, MAC address spoofer, easy cryptographic tools and much more.
Portability
Zero Trace devices are based on top of OST, the most advanced and recognized universal operating systems that can run anywhere. From your laptop to your phone, the device core can be used in a huge range of environments.
Equipped with a cold storage cryptocurrency wallet, you can access your assets safely and anonymously.
Customizability
Perfect default settings and great customizability are key to the success of the project. You can either fall in love with the minimalistic style of the Zero Trace system, or use it as a framework to build your custom system tailored around your very own needs and style. Install any application you require and take full advantage of the Tor powered ecosystem.
Performance
We care about speed, and the system has been engineered to be as lightweight as possible. You can run it on very old hardware, or perform very intensive tasks without performance drops.
Your applications will be free to use all your hardware resources.
Freedom
The source code is accessible to all members , and all the code that powers the system is made available either through our APT software repository or our GIT servers for you to read and customize. Exclusive access to the code that runs on your devices is a fundamental freedom, and we do our best to fight for your rights.
Privacy tools at your fingertips
You can install your favorite tools on top of any Linux/Android system, but it is time-comsuming, prone to errors and hard to keep updated over time. Zero Trace devices give you the convenience of a familiar desktop/mobile environment with all the tools you will ever need. We regularly update, test and pack them for you.
Having a bunch of .zip and .rar and .zip files thrown at your desktop/phone is something of the past. We do the hard work, not you.
Hide. Protect. Secure.
Messages are end-to-end encrypted with AES-256 and Private Key. The information transfer is peer-to-peer.

Maintain effective professional communication while ensuring the security of you and your business partners.

Secure video call service that facilitates talking face-to-face for improved communication.

Our developed suite of apps enable files transfer and utilizes AES-256 and Private Key to provide encryption and security.

Secure video conferencing service for a more effective interdepartmental communication within the organization or with external partners.

Decentralized cloud storage that utilizes Private Key and AES-256 for encrypting user files and providing access anywhere, anytime and from any device.

Securely communicate with your partners without the risk of being intercepted.

Utilizes VOBP protocol in order to generate a unique group key, based on members’ individual encryption keys in order to ensure a permanent and stable connection, regardless of their network reception.

Private encryption keys exchange between every member in order to ensure group information’s security and integrity.

VOBP integrates AES-256 and Private Key in order to safely store data in the user’s device.

Featured Products
Our Customers Say
Excellent

based on hundreds of reviews!
100% SATISFACTION
30- DAY MONEY BACK GURANTEE

Your order today is protected by our iron-clad 30-day 100% money-back guarantee. If you are not satisfied in how your operational security has improved or acquired a new privacy-oriented skillset, then at any time in the next 30 days let us know and we’ll refund you every single penny of your investment. No questions asked. Exclusions Apply
See Zero Trace in action...
“I created a darknet market using the Zero Trace Pen in about 5 minutes.”
“I didn’t realize how much location data was stored in my photos.”
“I was able to use sites anonymously, without leaving a trace.”
“The Zero Trace Phone pays for itself from day 1. I will never have to pay for an app again.”
Frequently Asked Questions
Zero Trace gives you access to more than 7,000 relays. Organizations running relays include universities like the MIT, activist groups like Riseup, nonprofits like Derechos Digitales, Internet hosting companies like Private Internet Access, etc. The huge diversity of people and organizations running relays makes it more secure and more sustainable.
You will have no problems passing TSA with a Zero Trace device. No one will even consider the fact that it’s nothing but a regular gadget. We here at Zero Trace, travel with our personal devices constantly and have never faced any issue.
The Zero Trace Phone works with any carrier and is fully functional internationally in any country. We ship anywhere, so no matter where you are, you can get a Zero Trace Phone. If you want to take your anonymity up a notch and don’t want to use your usual carrier like AT&T, Verizon, or the one from your old phone, you can sign up for a carrier that allows anonymous registration, keeping your identity separate from your phone plan. To learn how to set up a Zero Trace Phone plan that isn’t tied to your personal identity: check out this guide.
eBooks & Guides
Our Customers Say
Excellent

based on hundreds of reviews!
Reccomended By:





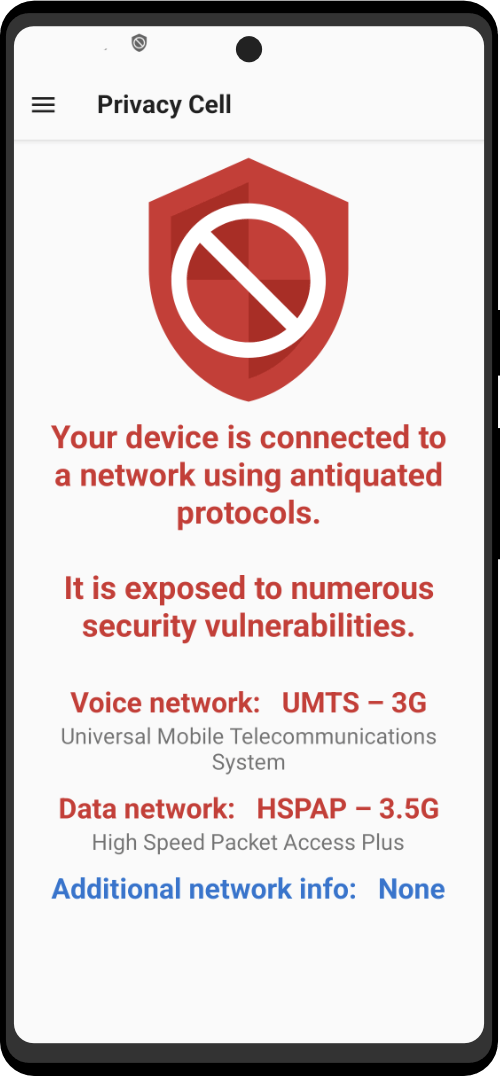
Ditch Your Unreliable VPN
8801 W Atlantic Blvd #770784
Coral Springs, Florida 33077
USA
support@zerotrace.org
+1 (954) 982-6661
Internet freedom is one of our core values. So we decided to put our money where our mouth is and got working on numerous digital rights projects. We help people fight surveillance and censorship, giving emergency privacy access to freedom fighters and journalists who work in dangerous conditions. We support other non-profit organizations and conferences focused on human and digital rights. And we work hard to educate the public about the importance of cybersecurity every single day.