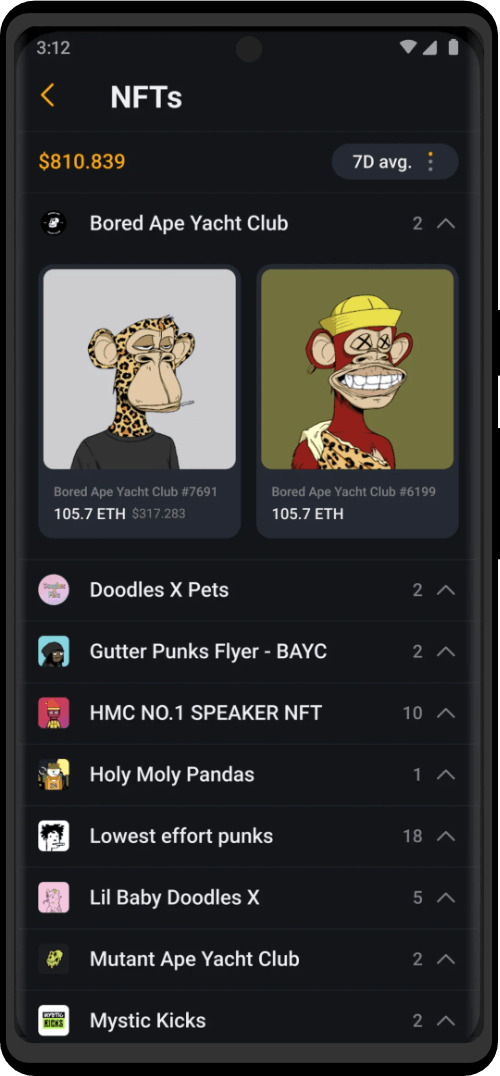
Power-Ups
Essential App Bundle
Your personal cloak of invisibility, allowing you to explore the internet free from prying eyes. The sense of security you experience is unparalleled as you browse with complete anonymity, knowing that your privacy is fully protected at an operating system level – powered by Zero Trace.
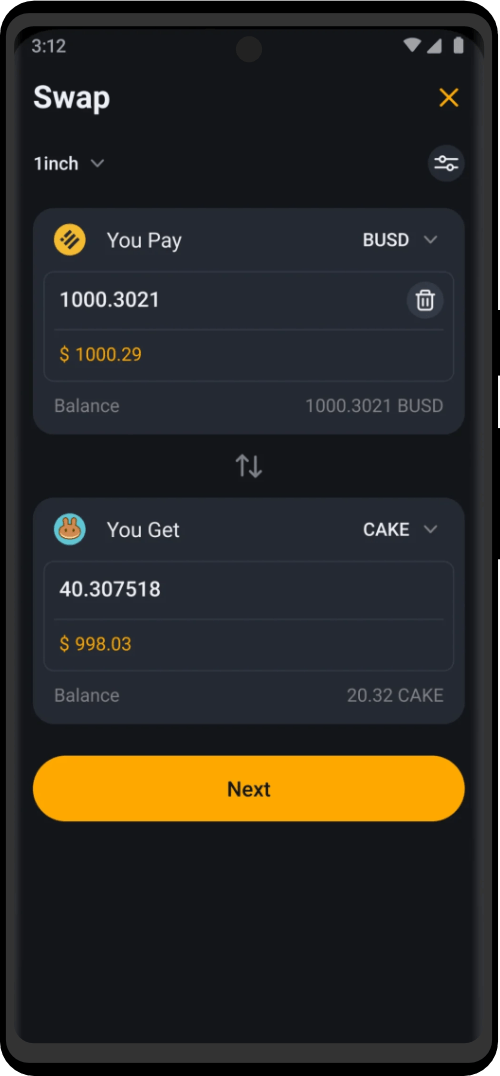
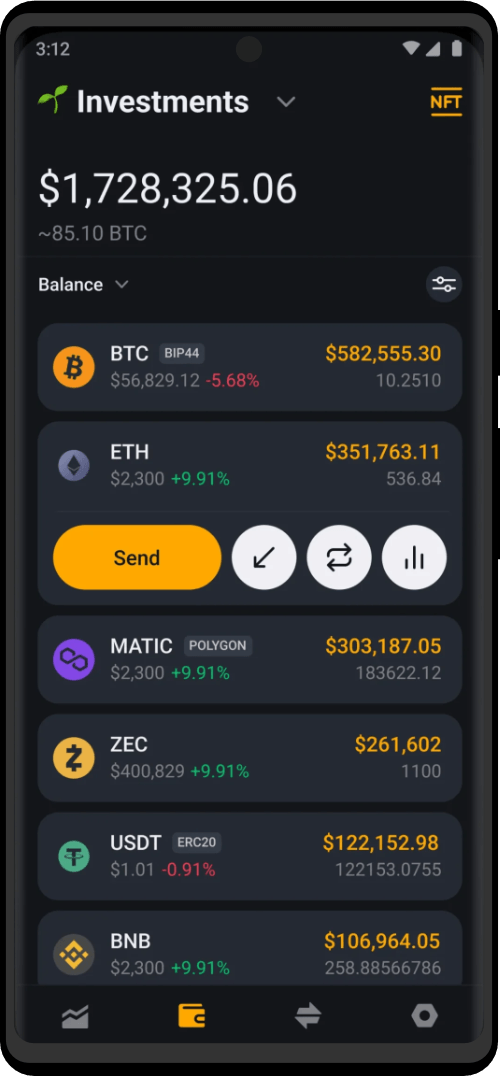
Securely manage your cryptocurrency, and access the limitless possibilities that await you in the world of decentralized finance. Complete privacy and specially created for maximum compatibility with the Tor network.
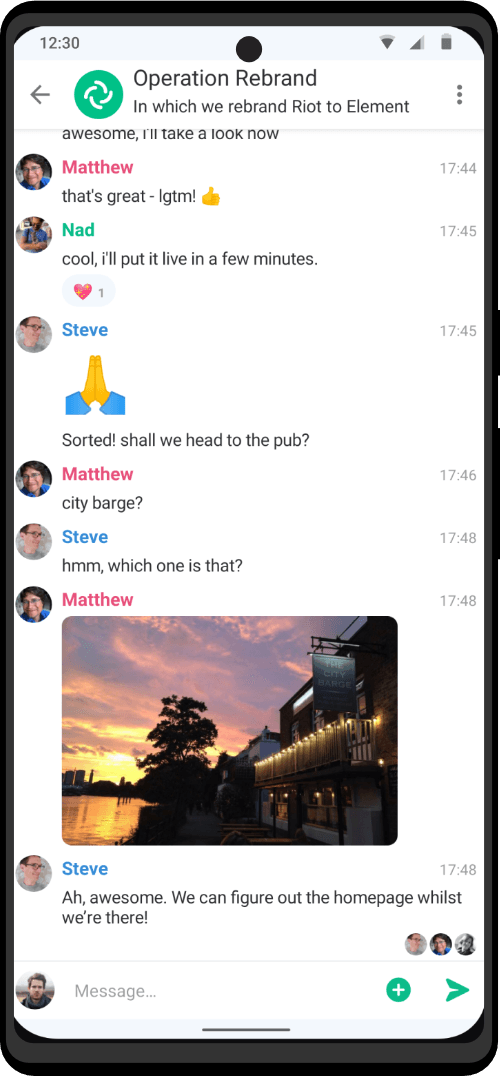
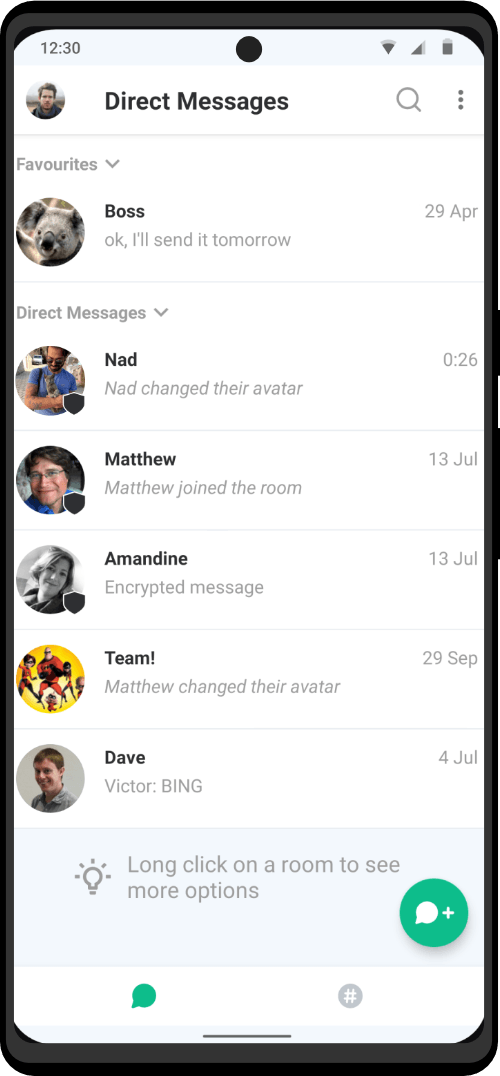
Communicate through voice calls with high clarity and absolute privacy. Send messages and files knowing that your personal information is protected. Powered by Matrix – you will have complete control over your conversations and data.
Effortlessly manage multiple email accounts, with the ability to add PGP encryption, streamlining your productivity and privacy. We’ve combined the power of e-mail and PGP, so that it is convenient as well as effective.
Access the freedom and flexibility of effortlessly opening and editing various document types you download/share from the internet. This specially configured tool combines privacy, security, and seamless collaboration. Read and edit files from various document formats, knowing that your sensitive information remains secure and confidential.
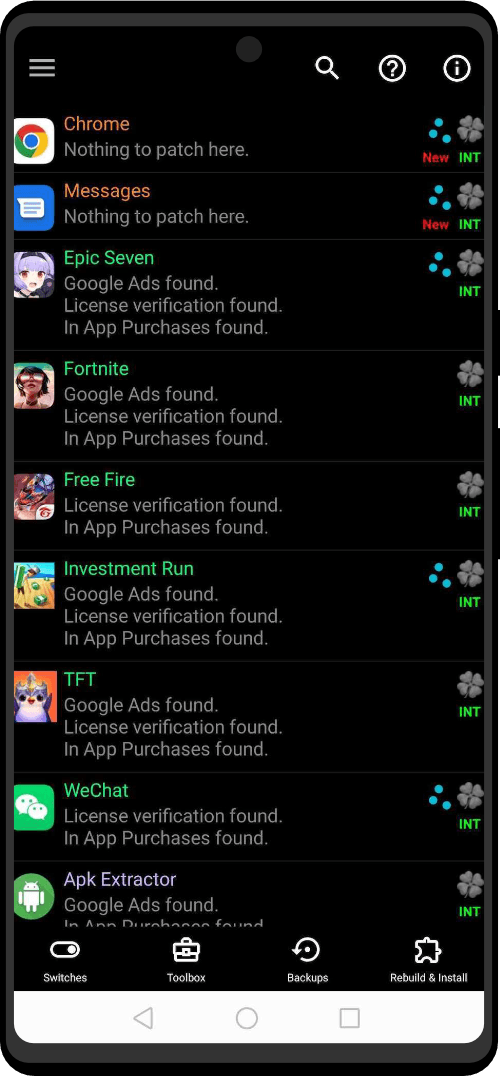
Access premium app features without spending a dime, all thanks to the APK Unlocker. Our innovative app bypasses payment barriers, granting you access to those exclusive features that usually require a subscription or one-time payment. You will no longer need to tie your identity to the Google Play Store via credit card just to access paid applications.
Anonymous Social App Bundle
ZeroPlayer is an intuitive, feature-rich, and privacy-focused app that brings you the best of YouTube, SoundCloud, and BandCamp without annoying ads or questionable permissions. Enjoy seamless downloading, customizable playlists, offline storage, background play, and a user-friendly interface. Access all the tutorials and information you need from these platforms without compromising your operational security.
Nitter is a sandboxed version of X. Browse Twitter free from JavaScript, and tracking while enjoying a lightweight, sleek interface with faster load times. Keep up to date with all the latest news, without compromising your privacy.
Do all your Reddit research with unparalleled privacy and control. This innovative app allows you to explore Reddit’s information gems without an account, customizing your experience through subscriptions, sorting, and personalized profiles. With features like search functionality, save options, and content control, Stealth offers a unique and secure way to stay informed while protecting your identity and data.
Security Hardening App Bundle
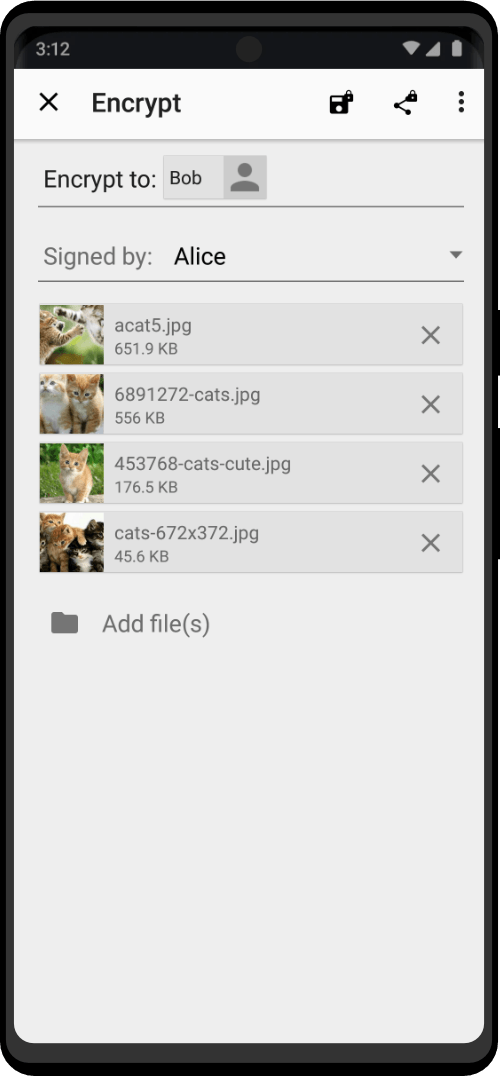
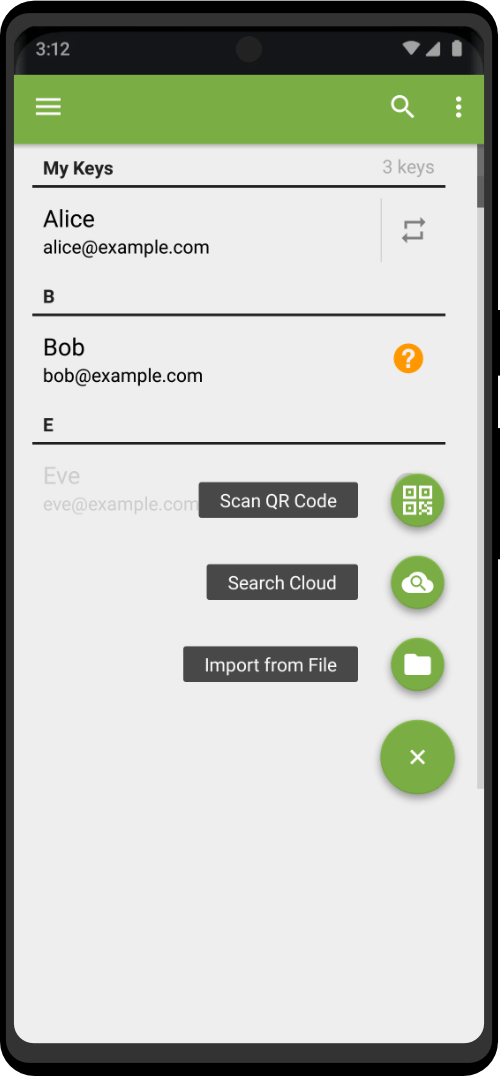
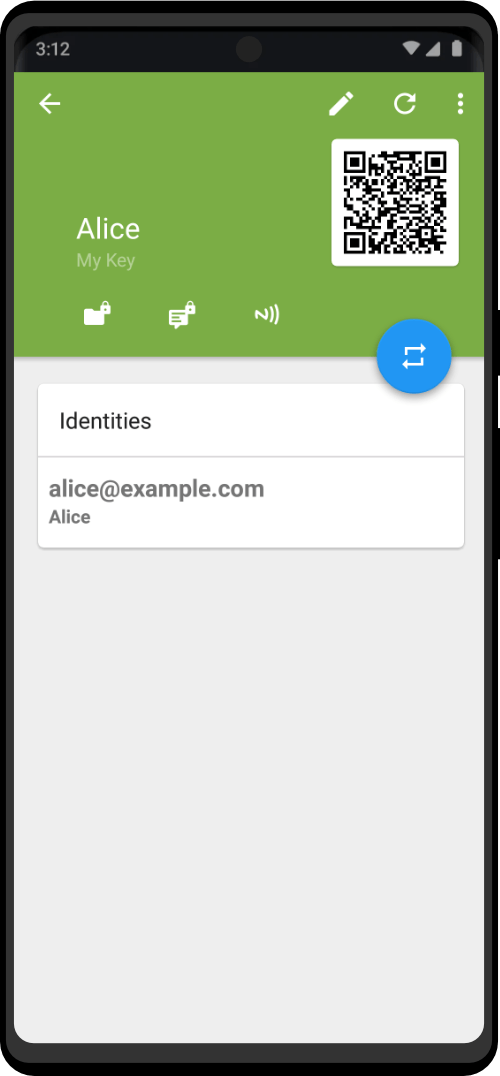
Encrypt sensitive information with PGP Key, a powerful encryption solution compatible with popular apps like K-9 Mail and other Zero Trace apps. Based on the OpenPGP standard, PGP Key provides reliable protection for your messages, ensuring they can only be read by the intended recipients. Manage all your keys easily with just one app.
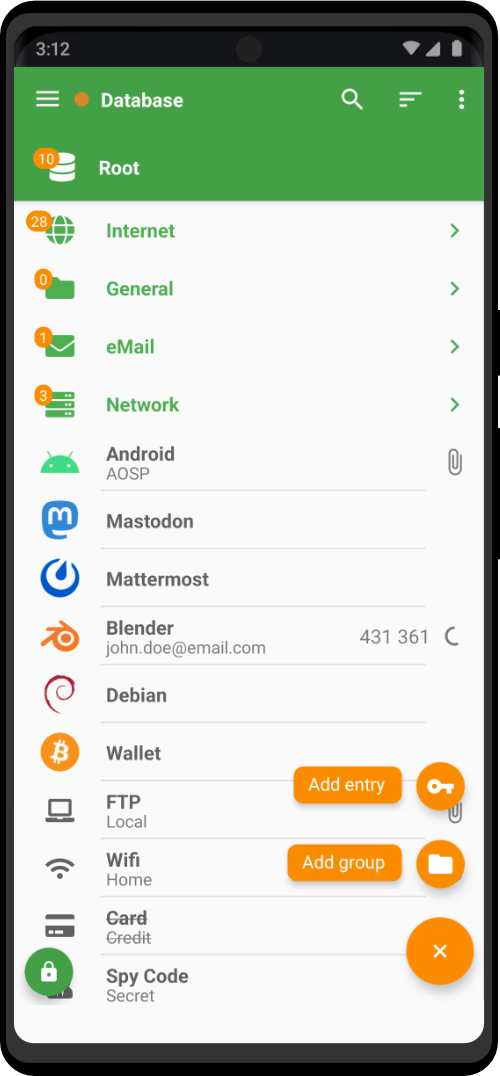
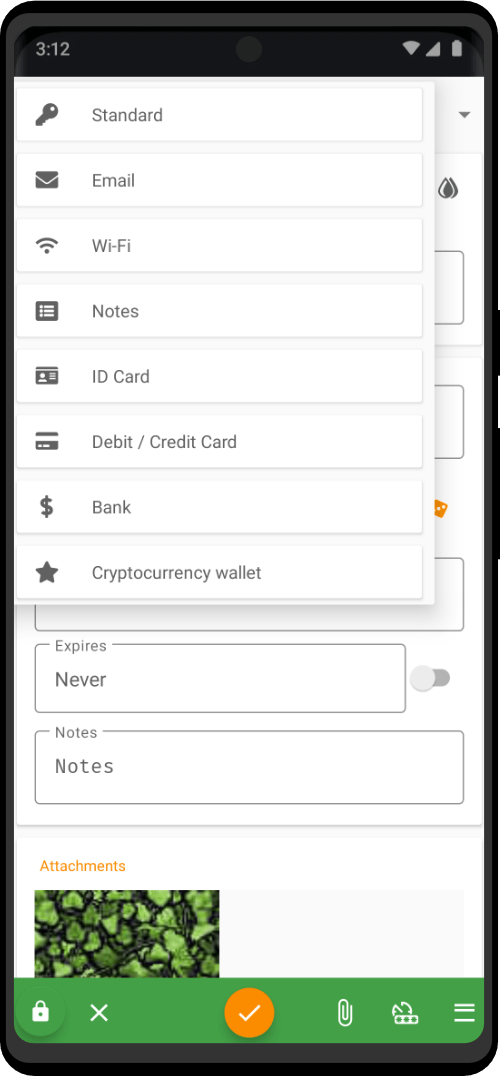
Create and manage database files, entries, and groups, with seamless compatibility and advanced encryption. Fully supporting biometric recognition, one-time password management, and Auto-Fill integration. Equipped with digital security tools like our built-in password generator. Remember all of your passwords to all of your different accounts and logins, without having to go through the time-wasting password reset process again.
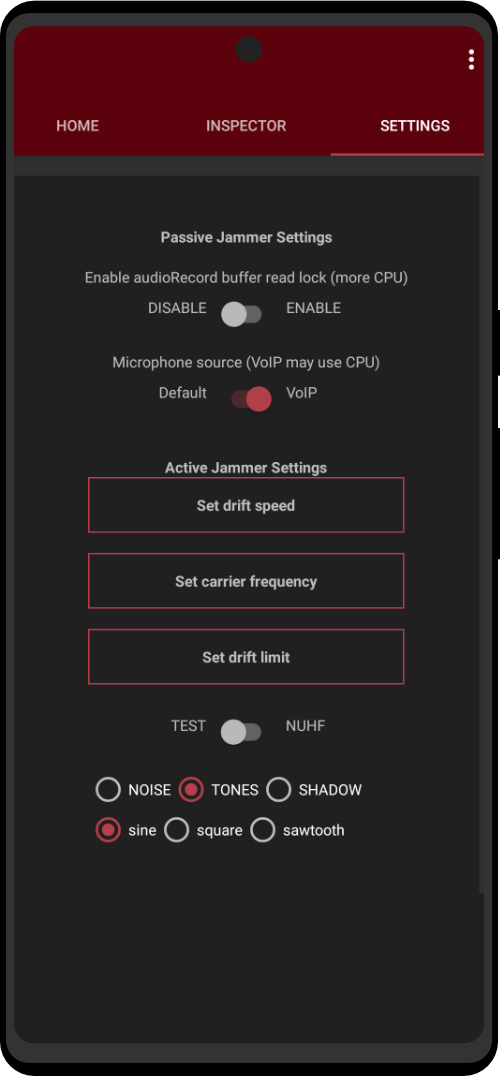
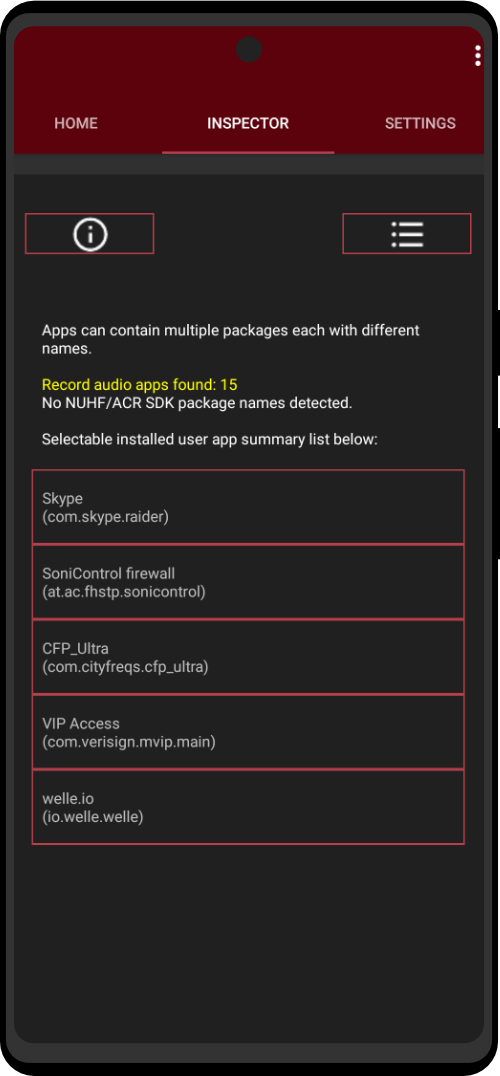
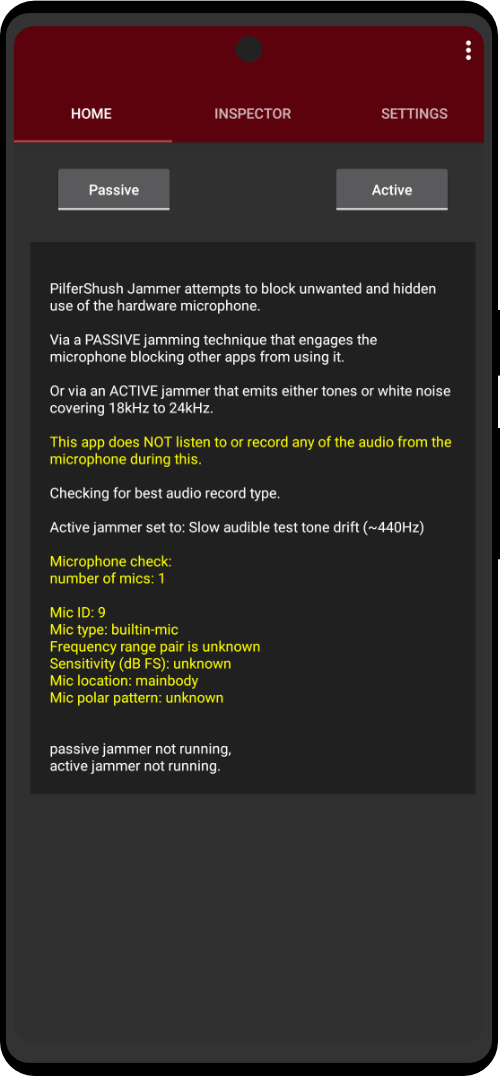
Effectively protect your phone from hidden apps attempting to access your microphone for audio tracking. This lightweight, exclusive app uses an innovative jamming technique to lock up your microphone, ensuring your conversations stay private. With minimal impact on device resources, discreet notifications, and a built-in scanner to check for NUHF and ACR SDKs, Mic Jammer provides the peace of mind you need in today’s connected world.
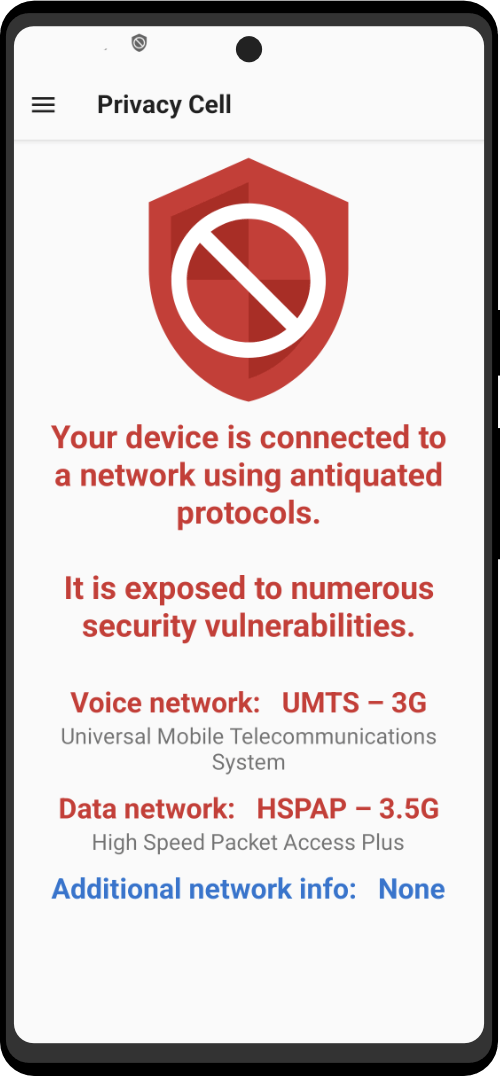
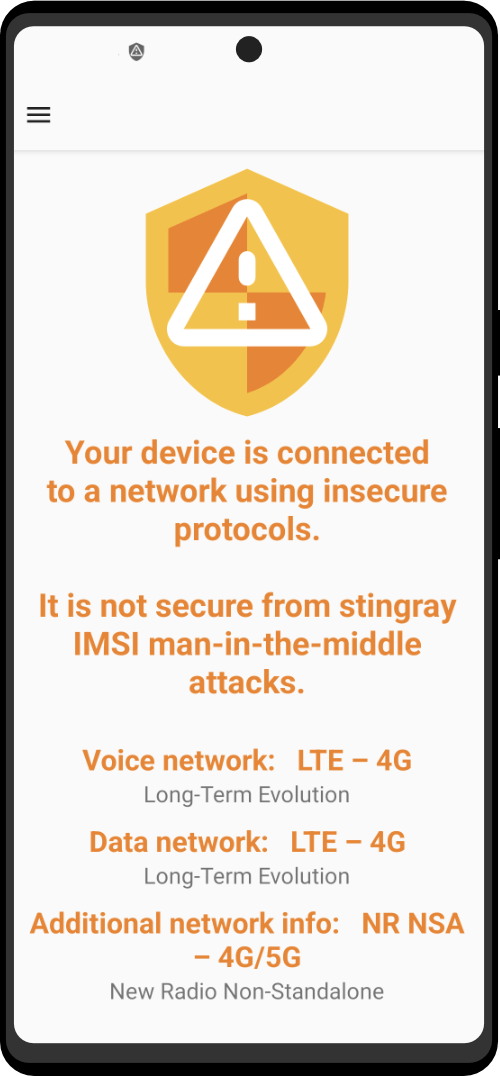
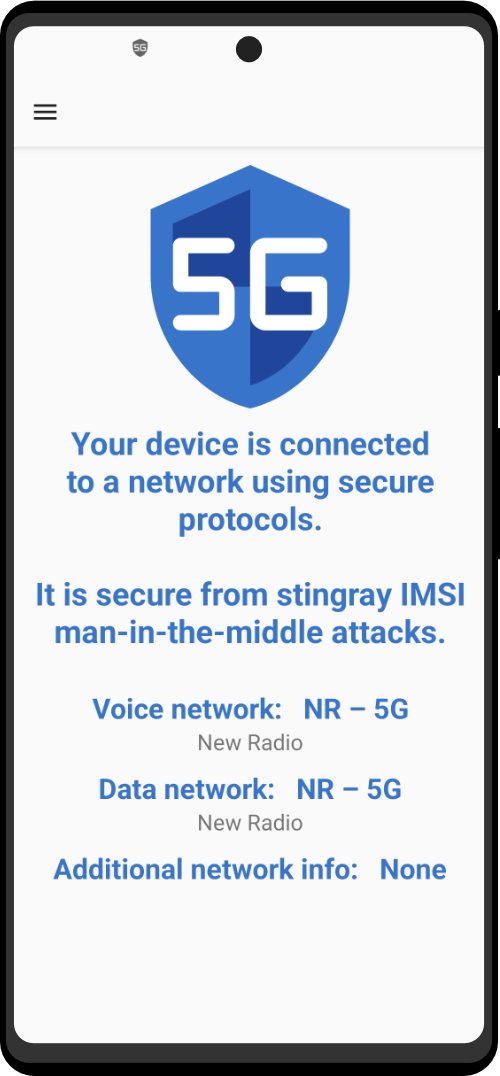
A cutting-edge counter-surveillance application that ensures your phone’s security and privacy in the rapidly evolving world of communication. While eagerly awaiting the full protection of 5G technology, this vital app provides essential information about your connection and safeguards against stingrays, electronic surveillance tools that compromise your device. Finally get peace of mind with Anti-Stingray, as it monitors your connection, even warning you when connected to vulnerable 2G and 3G networks.
Utilities+ App Bundle
Connect with friends and family, participate in group chats, and share multimedia content through Apple’s iMessaging. Access a seamless messaging experience, bridging the gap between privacy and still using iMessage. Requires access to a Mac computer.
The ultimate offline navigation app. Navigate without an internet connection, enjoy privacy-first data protection, and detailed maps with powerful features like AI DashCam, real-time traffic info, and comprehensive public transport maps. ZeroMaps offers the perfect blend of cutting-edge technology and user-friendly functionality, making it the best privacy-oriented travel companion for every journey.
Every Model Includes:
8801 W Atlantic Blvd #770784
Coral Springs, Florida 33077
USA
support@zerotrace.org
+1 (954) 982-6661
Internet freedom is one of our core values. So we decided to put our money where our mouth is and got working on numerous digital rights projects. We help people fight surveillance and censorship, giving emergency privacy access to freedom fighters and journalists who work in dangerous conditions. We support other non-profit organizations and conferences focused on human and digital rights. And we work hard to educate the public about the importance of cybersecurity every single day.