Zero Trace Phone®
Original price was: $1,495.05.$979.00Current price is: $979.00.
All-in-One Tor Network Anonymous Phone + Anti-Surveillance Toolkit
Zero Trace Phone is an all-in-one smartphone with everything you need to stay anonymous. Being completely portable, you can utilize the Tor network from anywhere, anonymously from the Zero Trace Phone. (Clearnet | Dark Web | Darknet | Deep Web Compatible)
-
- 5 Years Of Security Updates
- Pre-installed Privacy Apps
- Built-In MAC Address Spoofer
- Deadman’s Switch (Emergency Factory Reset Protocol)
- Penetration Testing Toolkit
- ZT PRO Support
26 reviews for Zero Trace Phone®
Only logged in customers who have purchased this product may leave a review.
Specification: Zero Trace Phone®
|
||||||||||||
| Dimensions | ||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
||||||||||||

Original price was: $1,495.05.$979.00Current price is: $979.00.



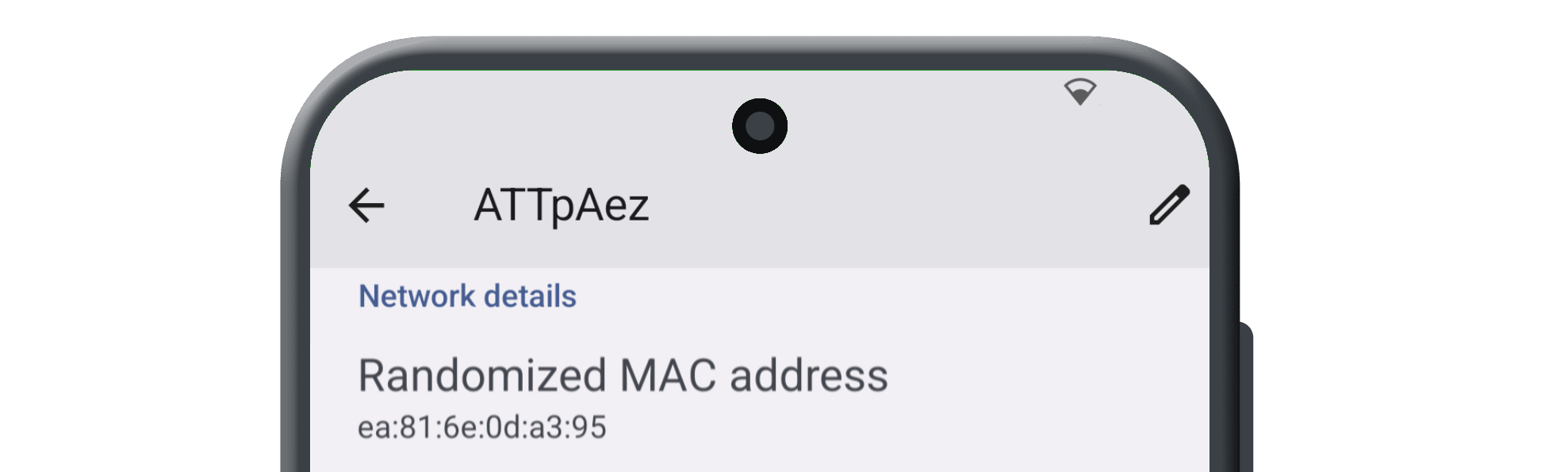









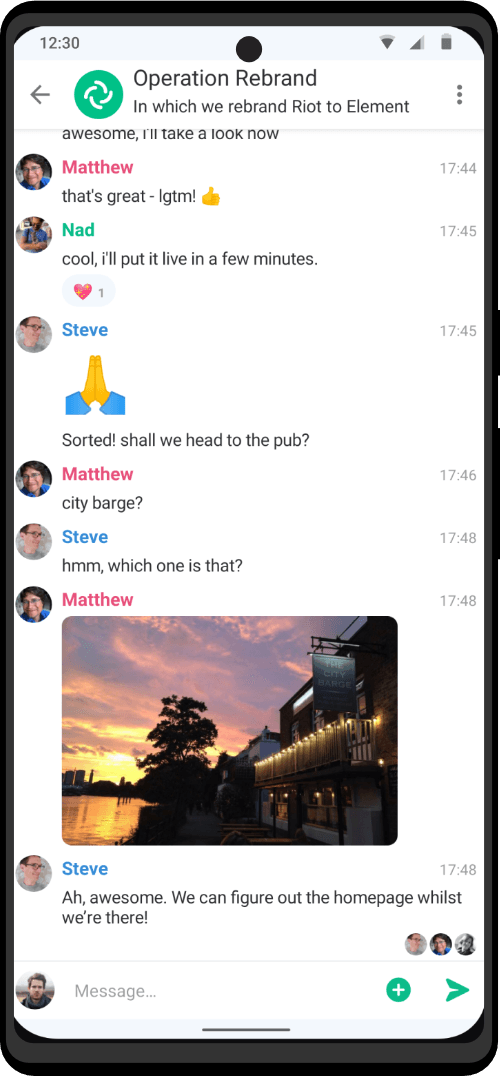
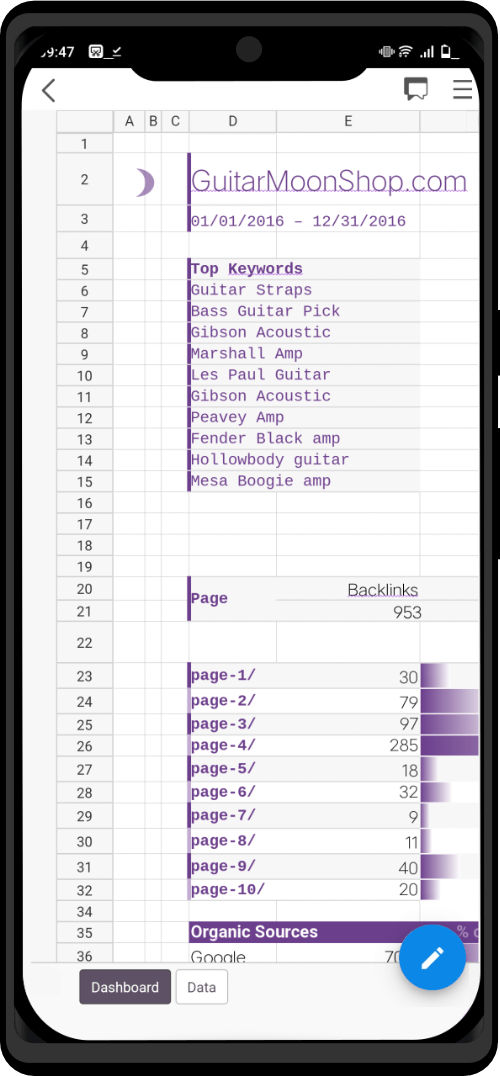

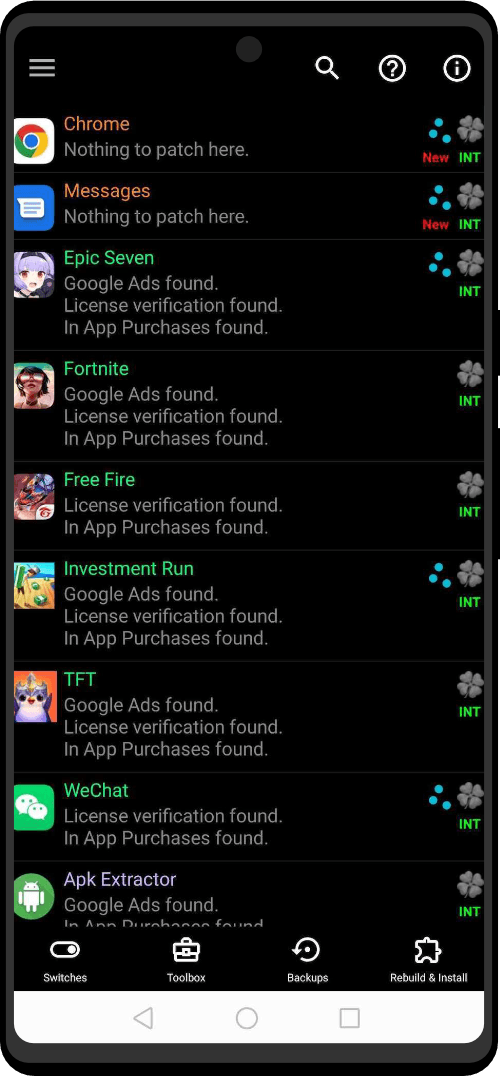
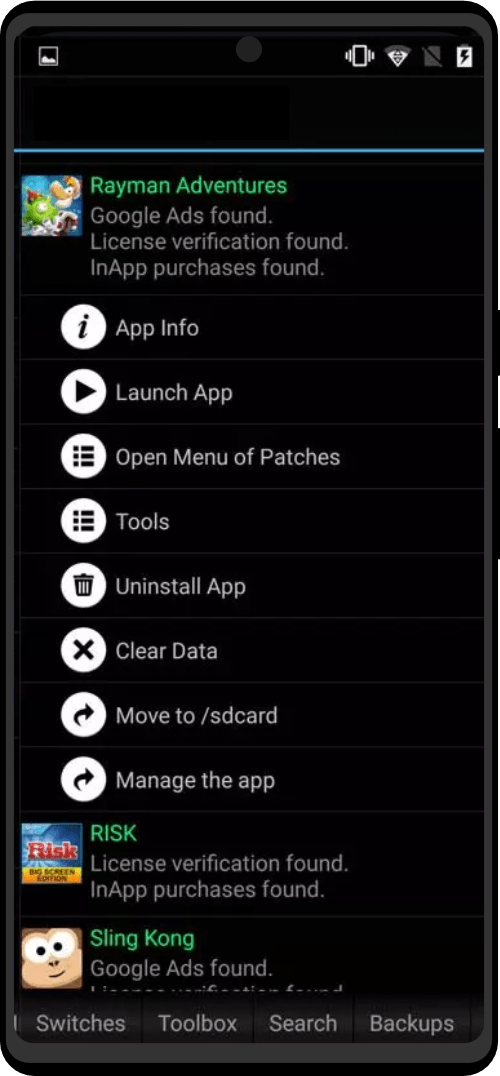

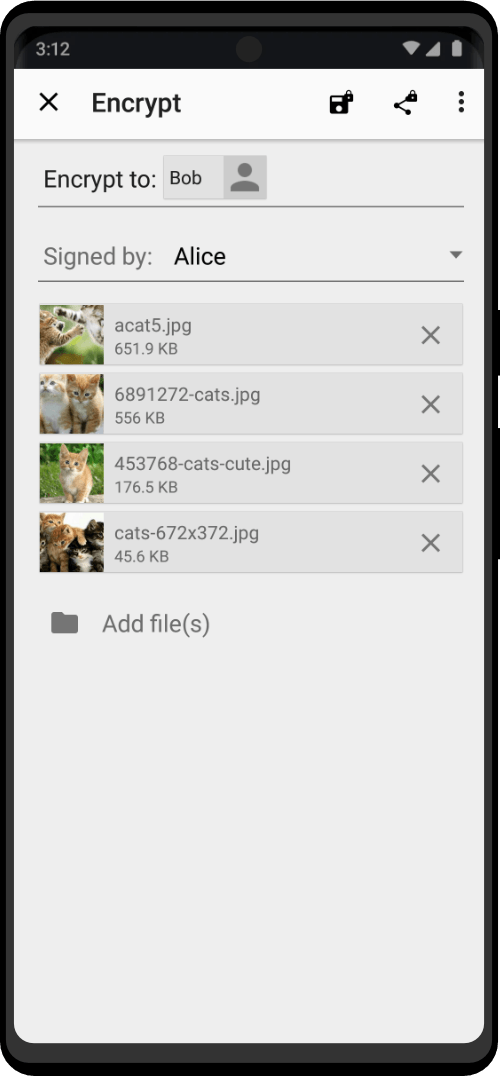
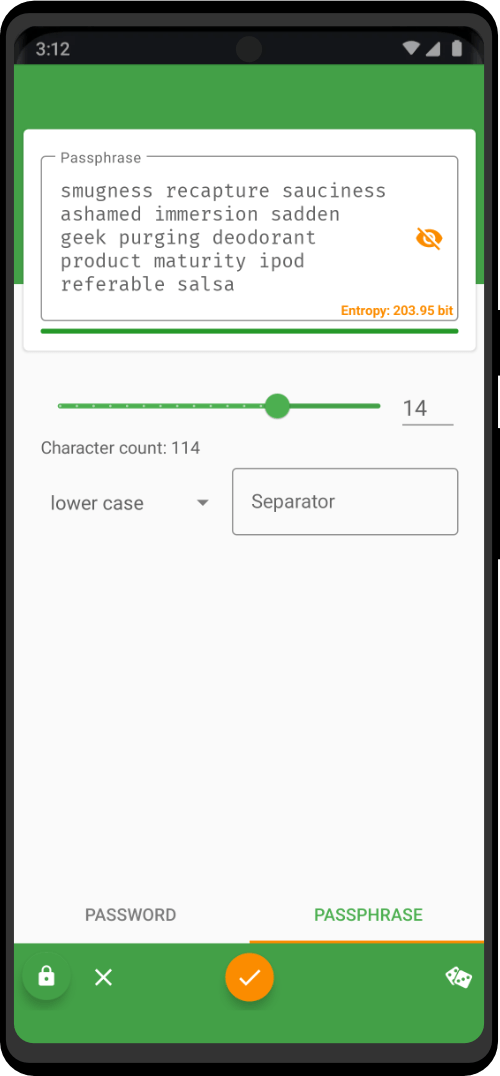
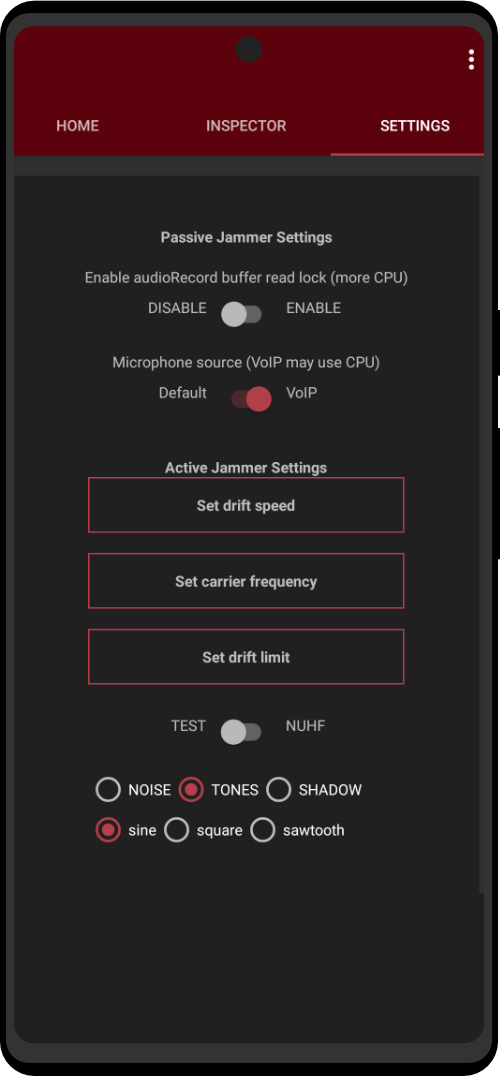
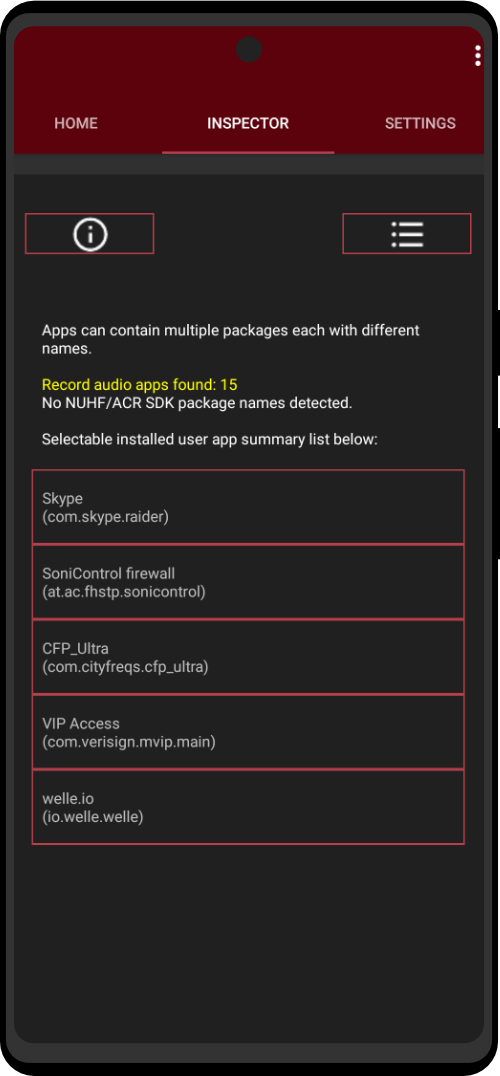
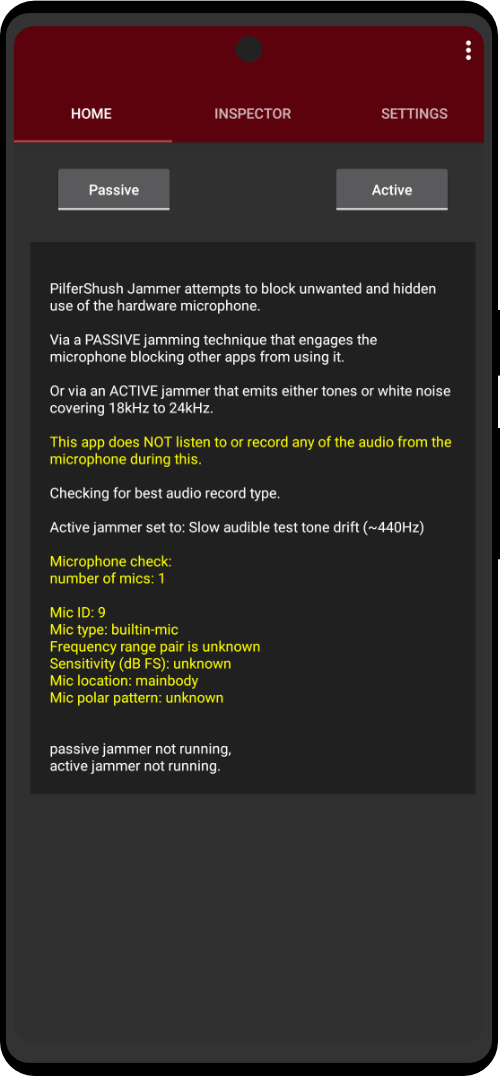
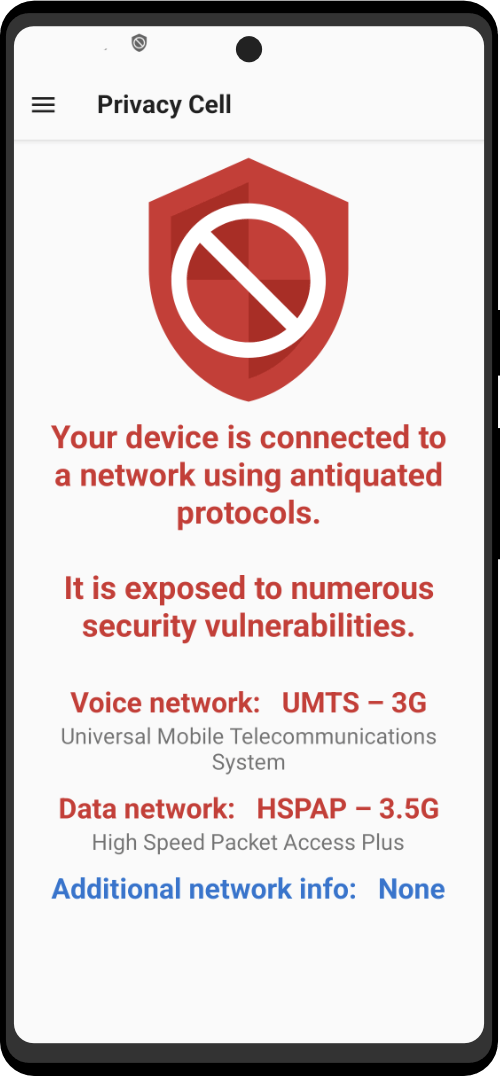
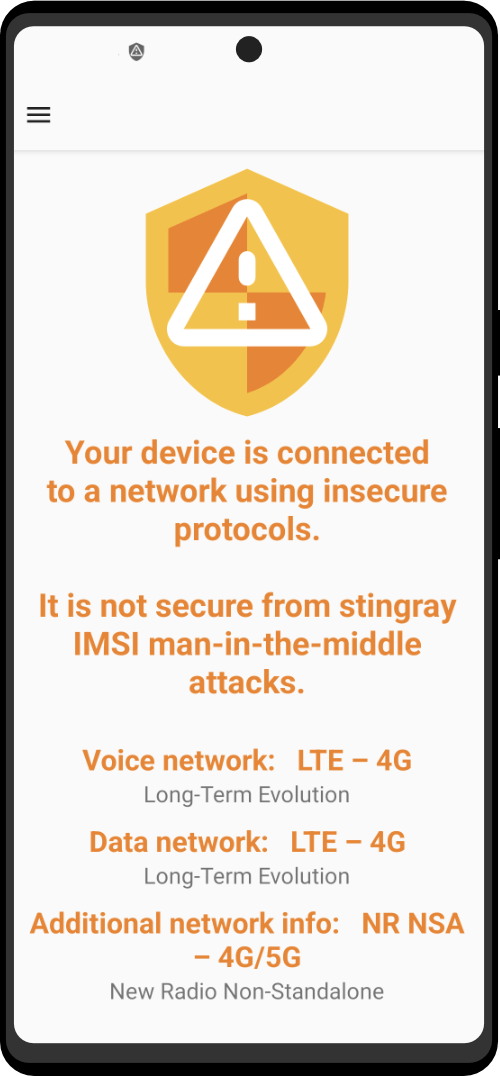
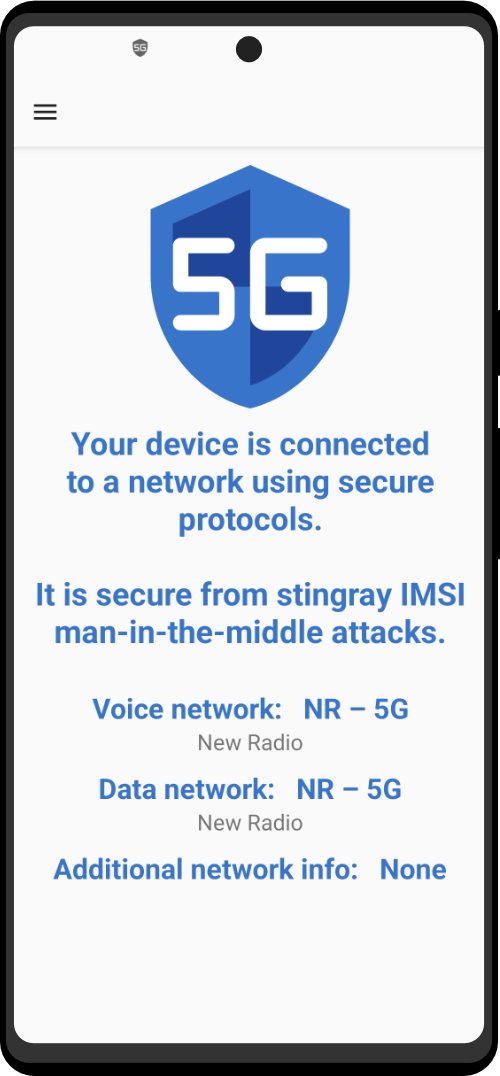

The Zero Trace phone has many great privacy and security features built right into the phone's system. It uses strong coding to keep things secret, has apps for secure talking, and protects you when browsing the web. This makes it easy for users to stay private and anonymous. It also has special hardware, like a MAC address spoofer, which adds another layer of protection against bad things.
The Zero Trace phone is really well made from a technical view. It works very fast and has lots of storage space. The screen and buttons are easy to use, even for people who aren't great with technology. The battery also lasts a long time, so users can count on the phone to work for a while without making their security worse.
We think the Zero Trace phone is an excellent pick for people and companies who really care about keeping their mobile talks private and secure. The Zero Trace team has shown they will keep working hard to make the phone better over time. This makes us feel good about suggesting the phone for the future.
We highly recommend the Zero Trace phone to anyone who wants a secure, reliable, and feature-packed mobile device. It's clear that the Zero Trace team has worked extra hard to make a phone that sets a new bar in the industry.
If your a serious 'entrepreneur" who values a phone that prioritizes your privacy and won't compromise your location, then you should definitely consider this phone. While it may cost a bit more than your average smartphone, I believe the peace of mind it offers is well worth the investment.