Zero Trace Phone®
$979.00
All-in-One Tor Network Anonymous Phone + Anti-Surveillance Toolkit
Zero Trace Phone is an all-in-one smartphone with everything you need to stay anonymous. Being completely portable, you can utilize the Tor network from anywhere, anonymously from the Zero Trace Phone. (Clearnet | Dark Web | Darknet | Deep Web Compatible)
-
- 5 Years Of Security Updates
- Pre-installed Privacy Apps
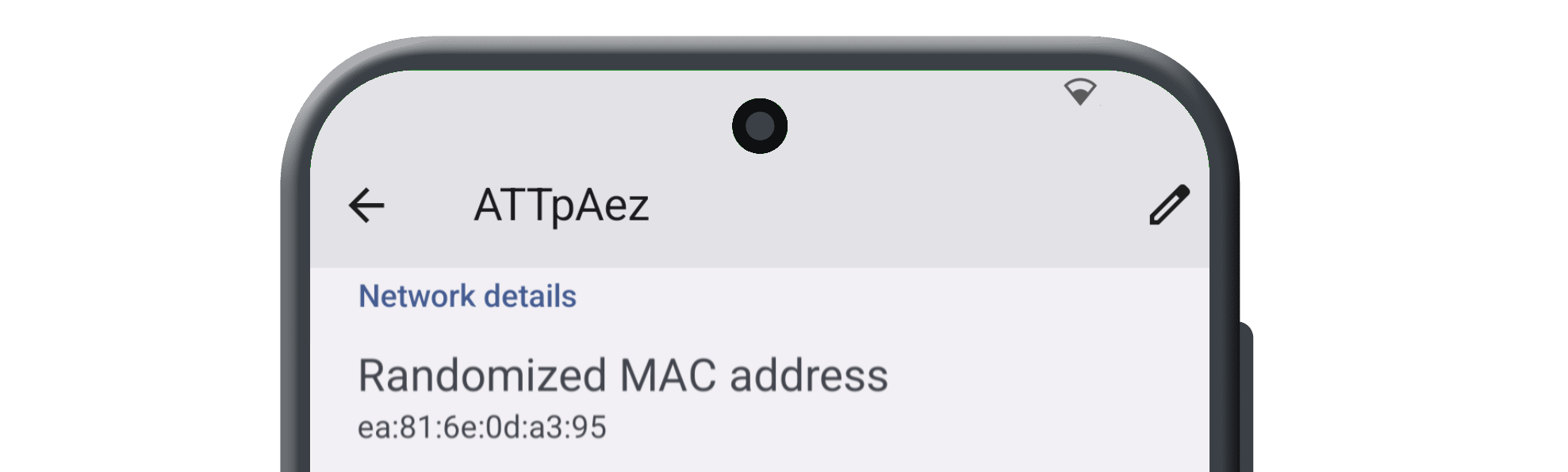
- Built-In MAC Address Spoofer
- Deadman’s Switch (Emergency Factory Reset Protocol)
- Penetration Testing Toolkit
- ZT PRO Support
NOTE: Specs, hardware, RAM, and additional features are chosen during the configuration process, so builds will vary accordingly. Select the build to match your specific needs and budget. Typically ready to ship 7–14 days, based on your build. Read our whitepaper first.
65 reviews for Zero Trace Phone®
Only logged in customers who have purchased this product may leave a review.
Specification: Zero Trace Phone®
| Dimensions | 5 cm |
|---|---|
| Compatibility | APK Extension Application Compatible |
| Update Interval | Monthly |
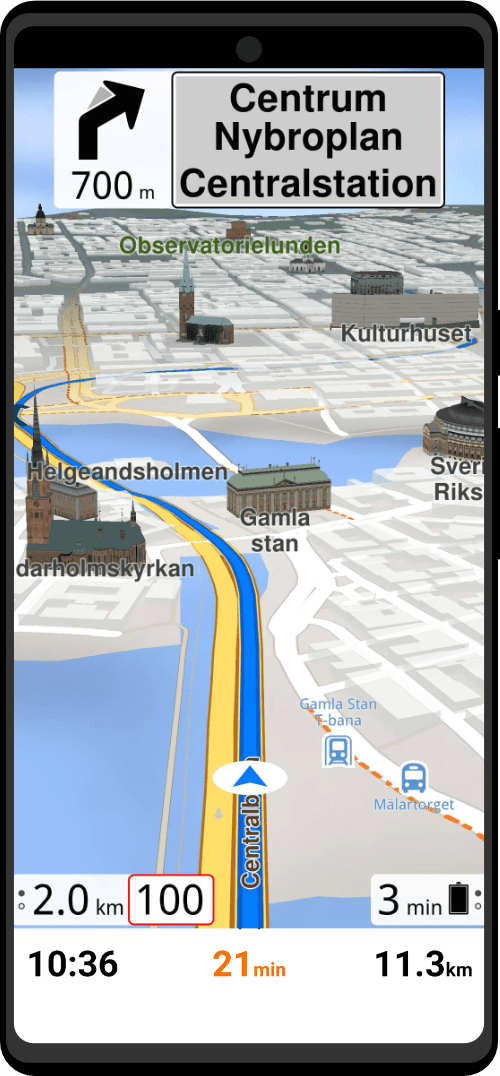
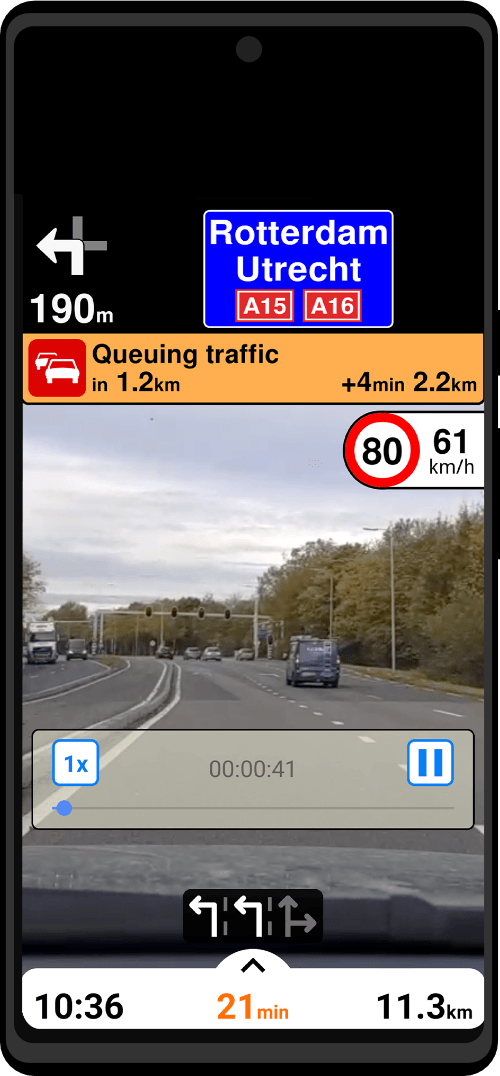
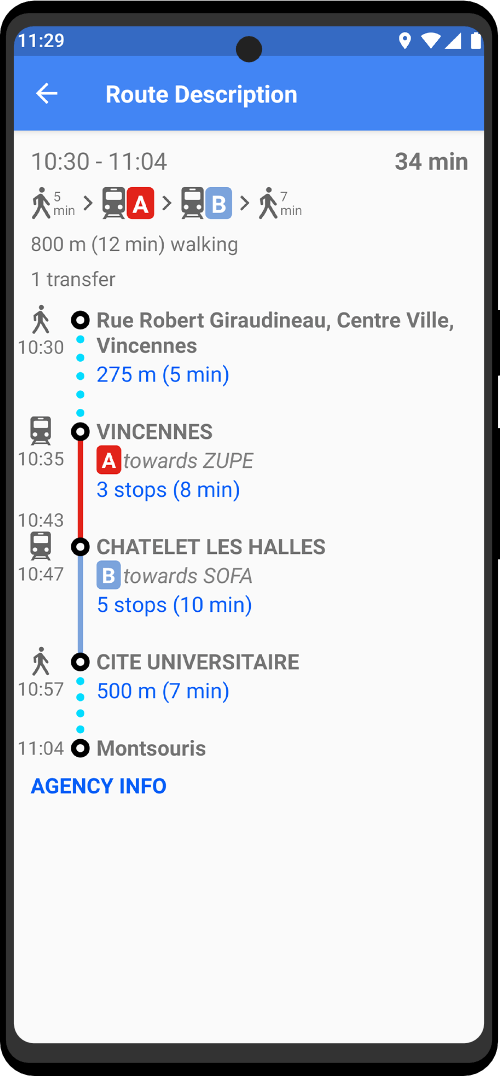
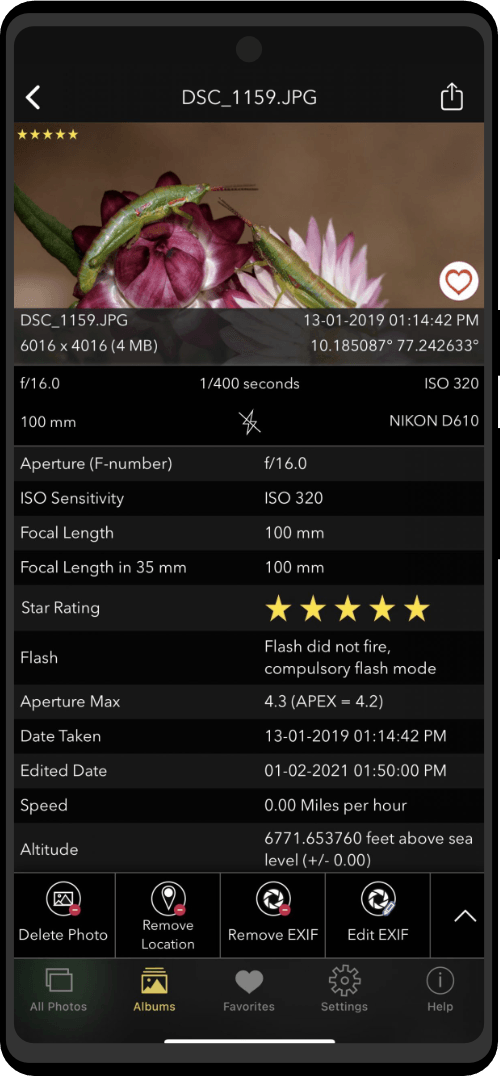
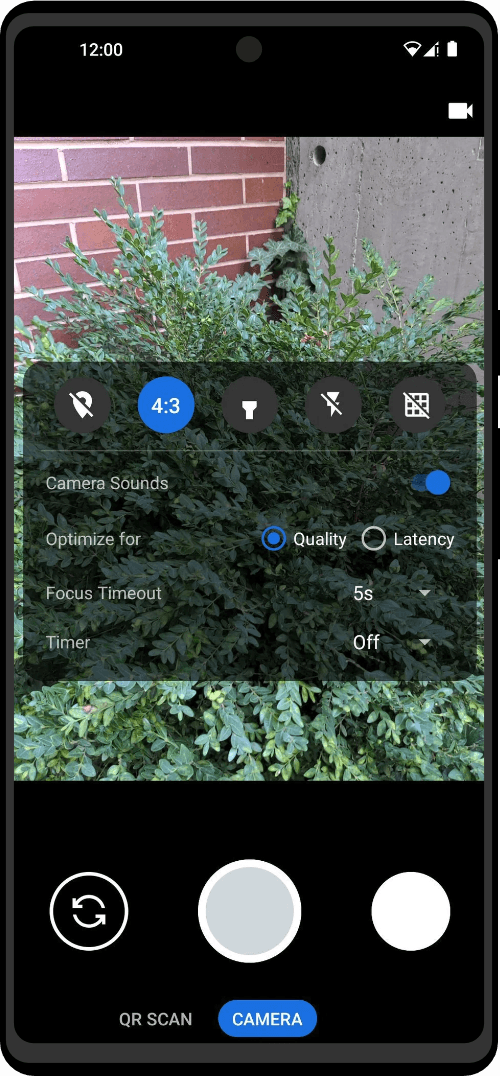
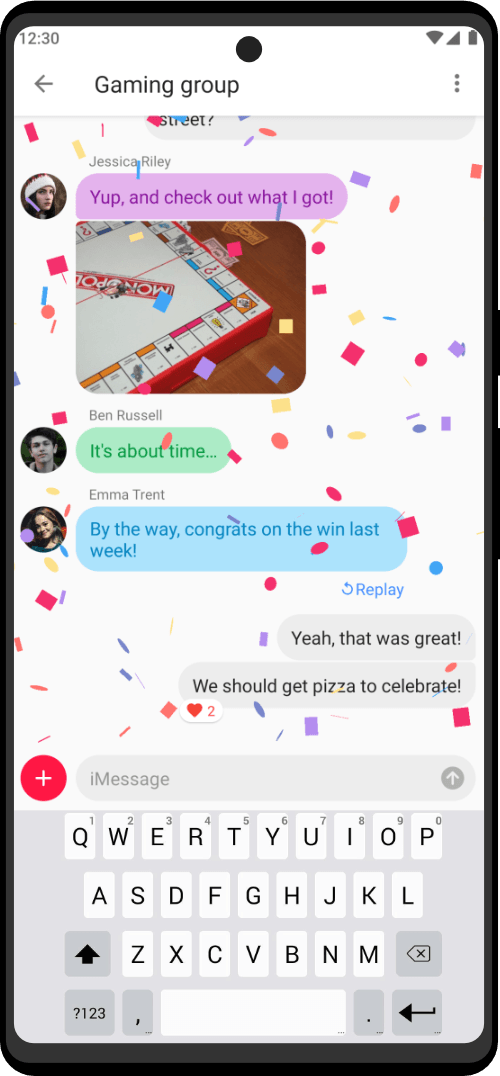
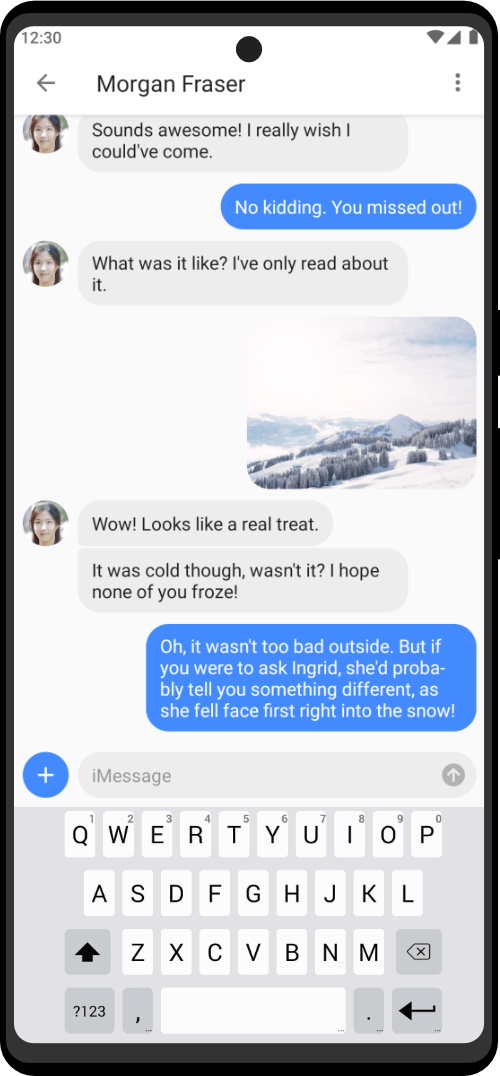
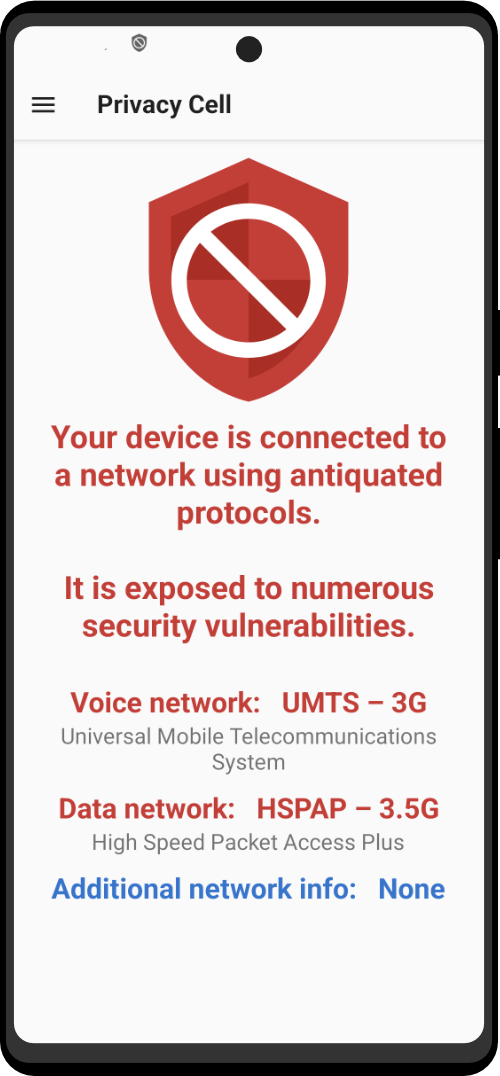
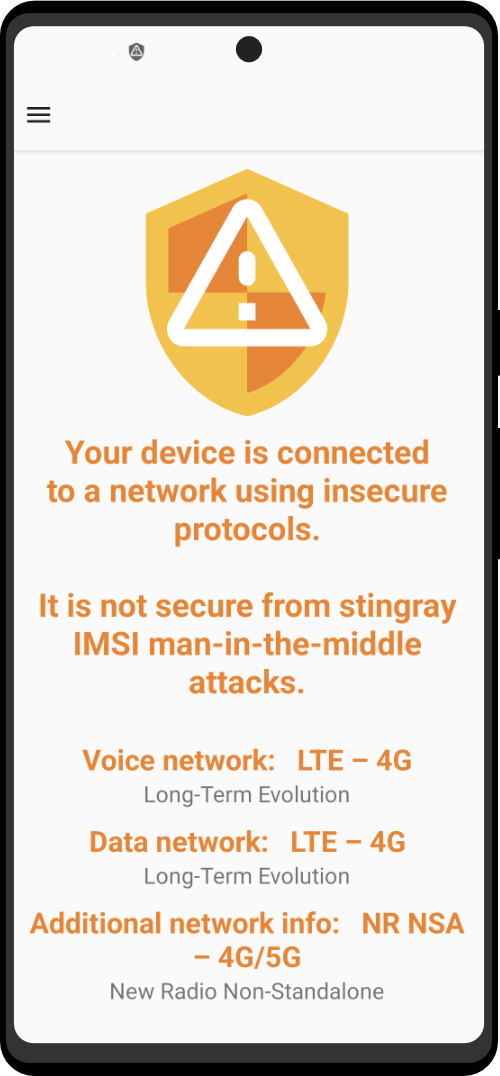
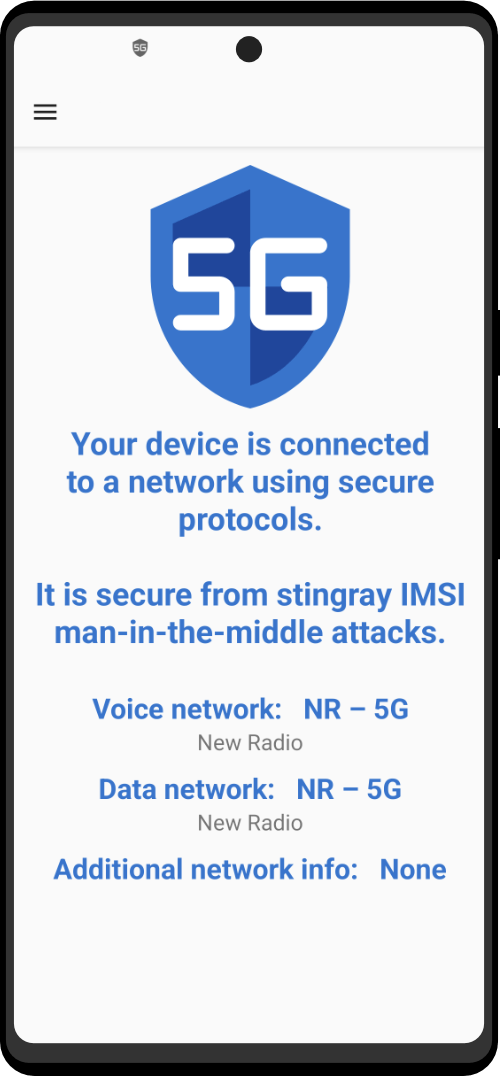
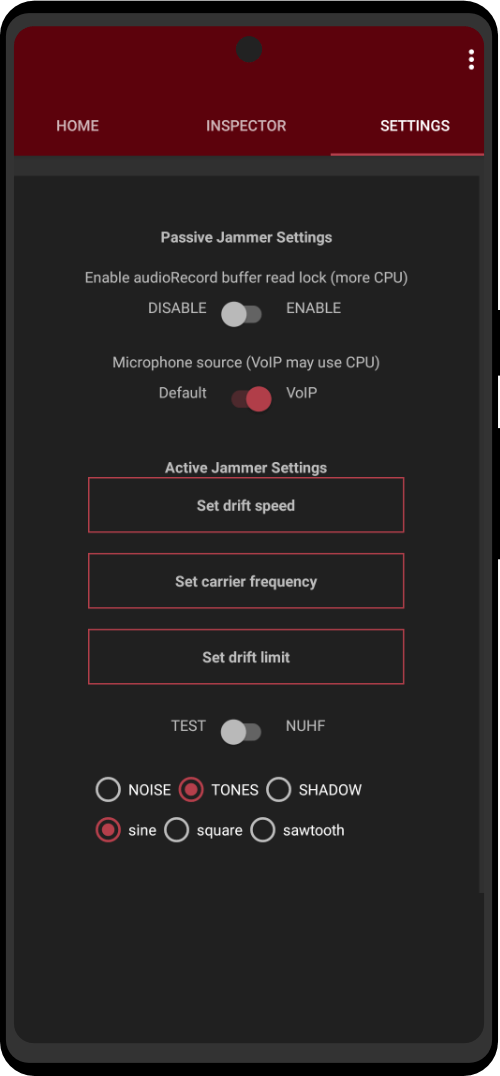
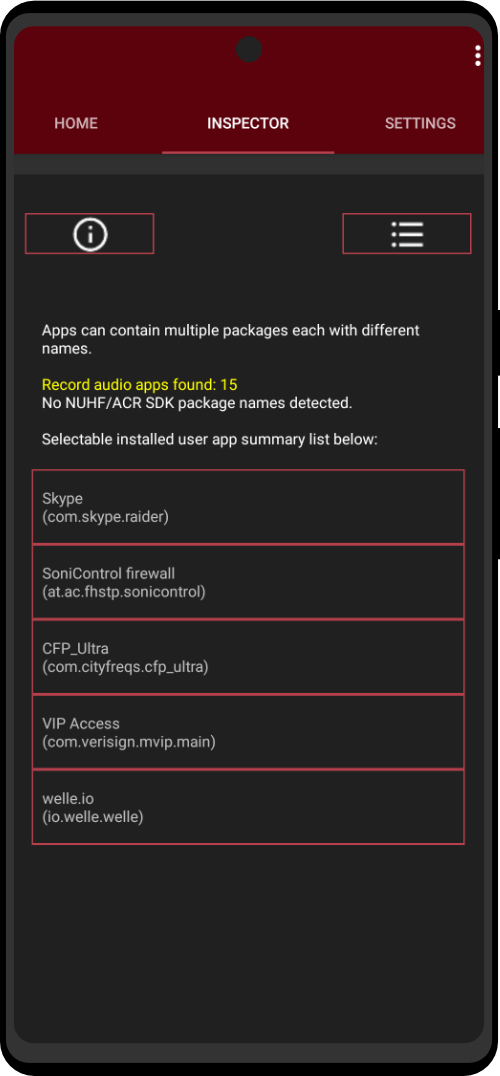
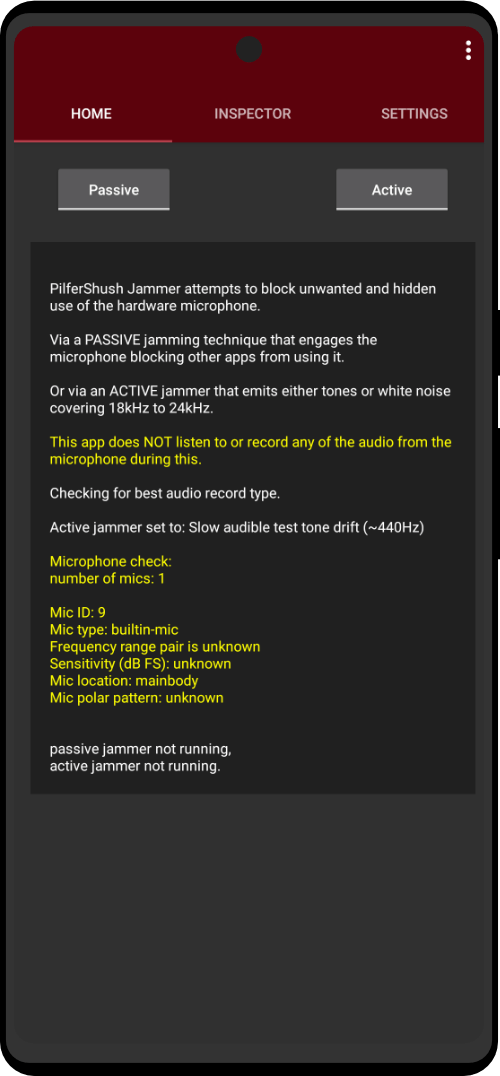
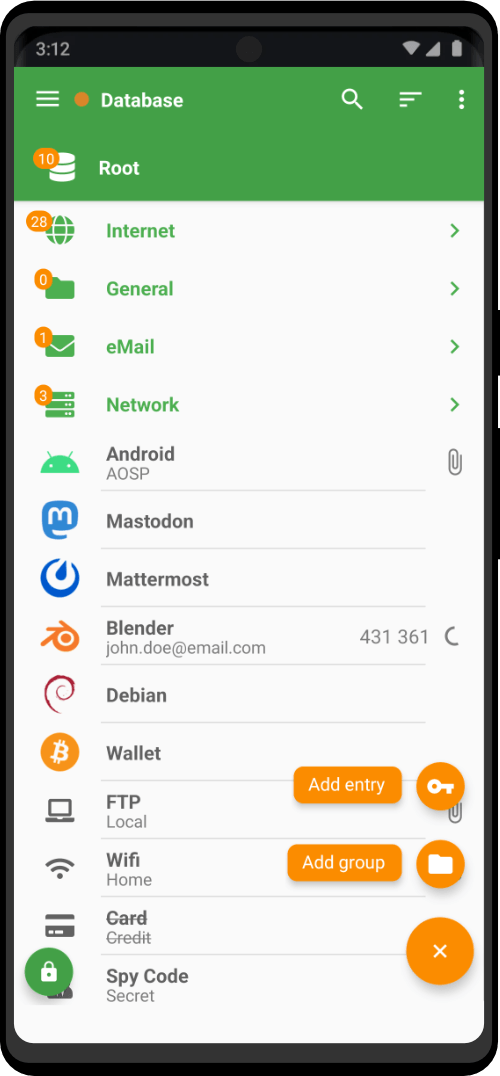
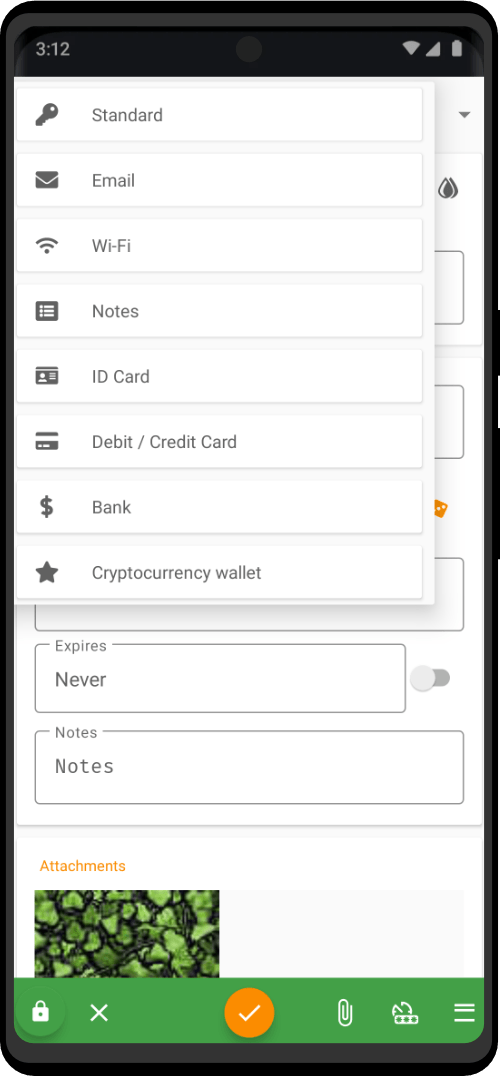
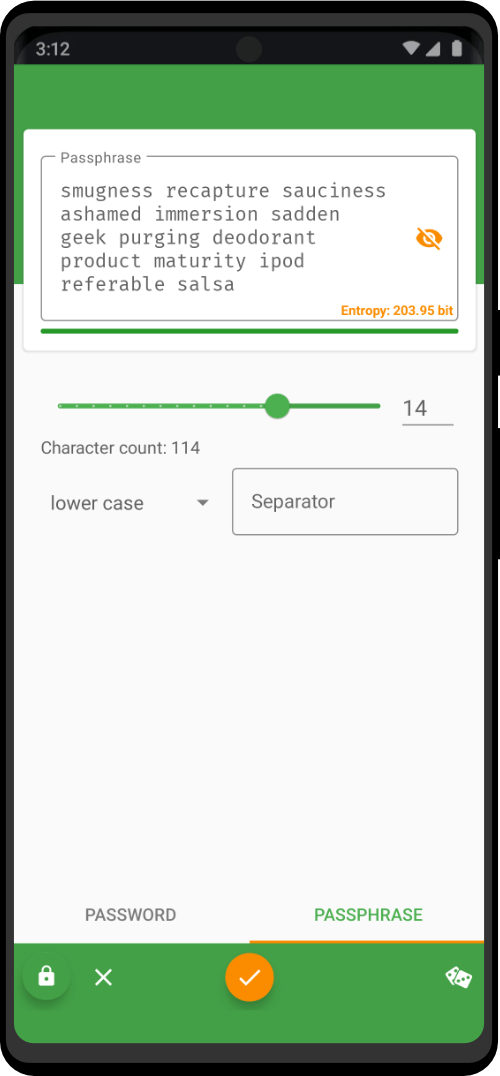
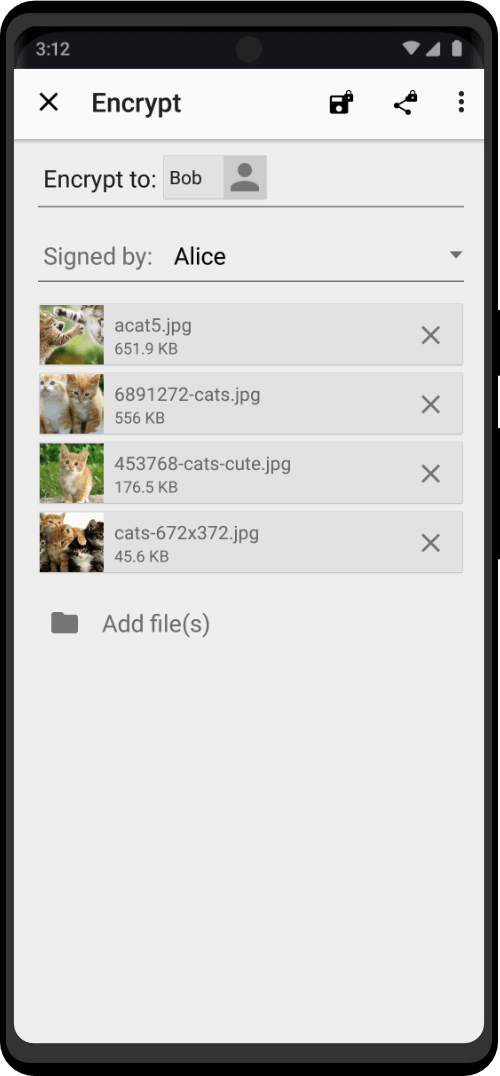
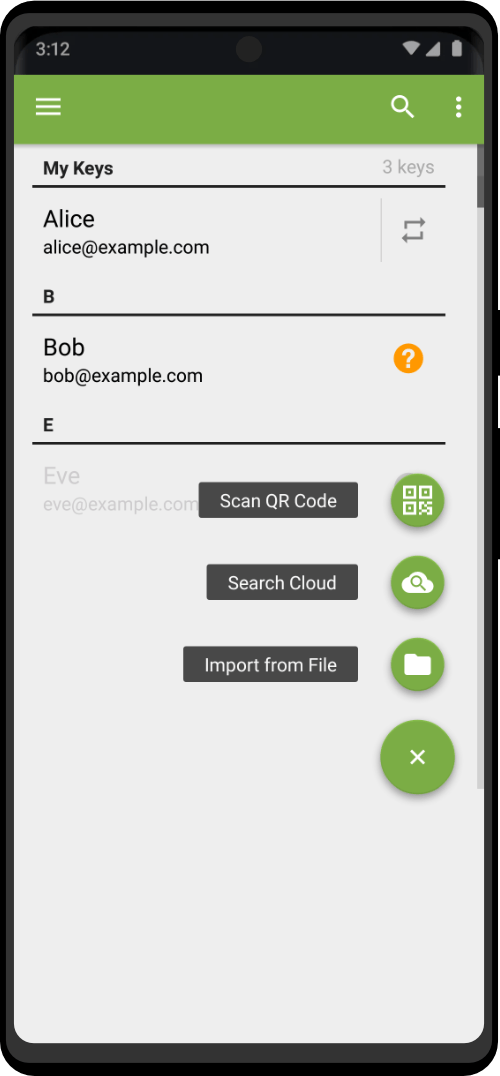
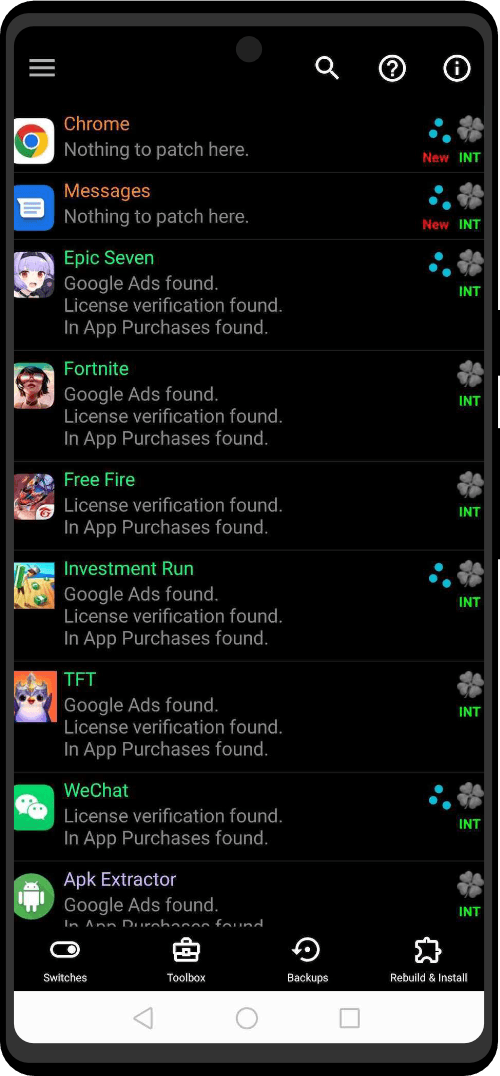
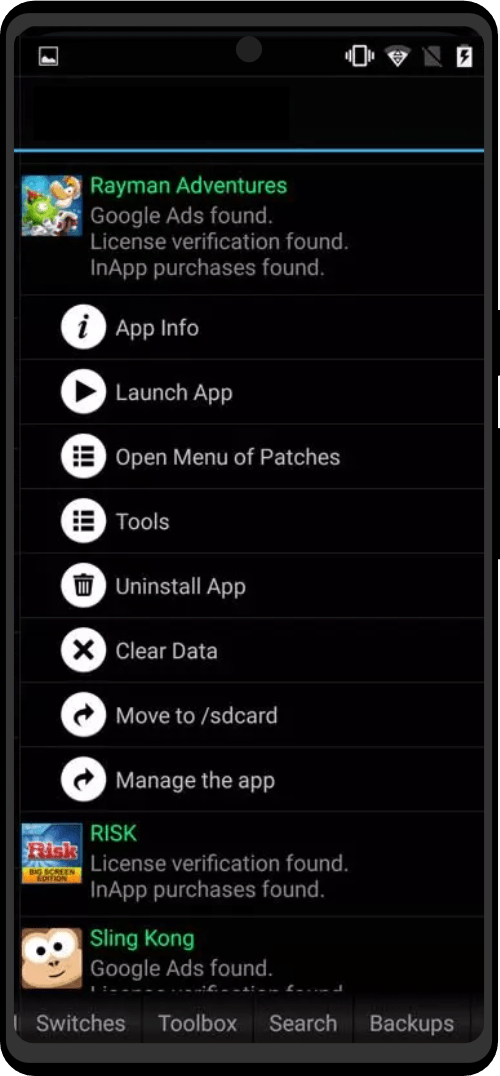
| Utility Applications & Features | KeePassDX, PGP Key, Sandbox, Storage Scopes, Secure Fingerprint, User Profile, Auditor, Element, K-9 Mail, iMessage, Tor Browser, MAC Address Spoofer, Zurf, Mic Jammer, Anti-Stingray, Scrambled Pin, Toggles, LTE-Only Mode, Collabora Office, Exif Scrubber, Private Screenshot, Anonymous Camera, AnonCamera, ZeroPlayer, Nitter, Stealth, Unstoppable Wallet, Location Alert, ZeroMaps |
| Hardware Add-Ons | Built-In MAC Address Spoofer, Deadman's Switch |
| Asset Storage | Non-Custodial Cryptocurrency Wallet |
| Support Priority | ZT PRO Support |













There are no reviews yet.