Zero Trace Phone®
$979.00
All-in-One Tor Network Anonymous Phone + Anti-Surveillance Toolkit
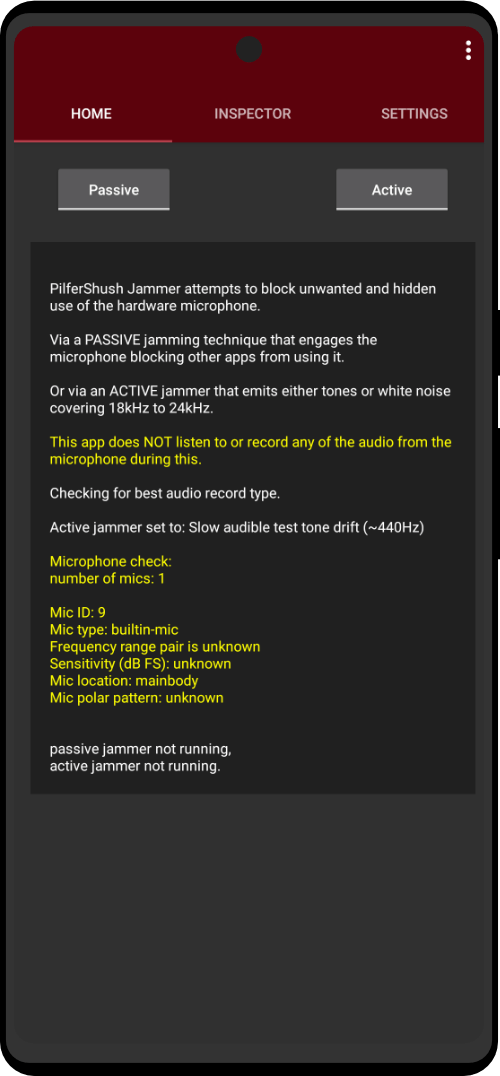
Zero Trace Phone is an all-in-one smartphone with everything you need to stay anonymous. Being completely portable, you can utilize the Tor network from anywhere, anonymously from the Zero Trace Phone. (Clearnet | Dark Web | Darknet | Deep Web Compatible)
-
- 5 Years Of Security Updates
- Pre-installed Privacy Apps
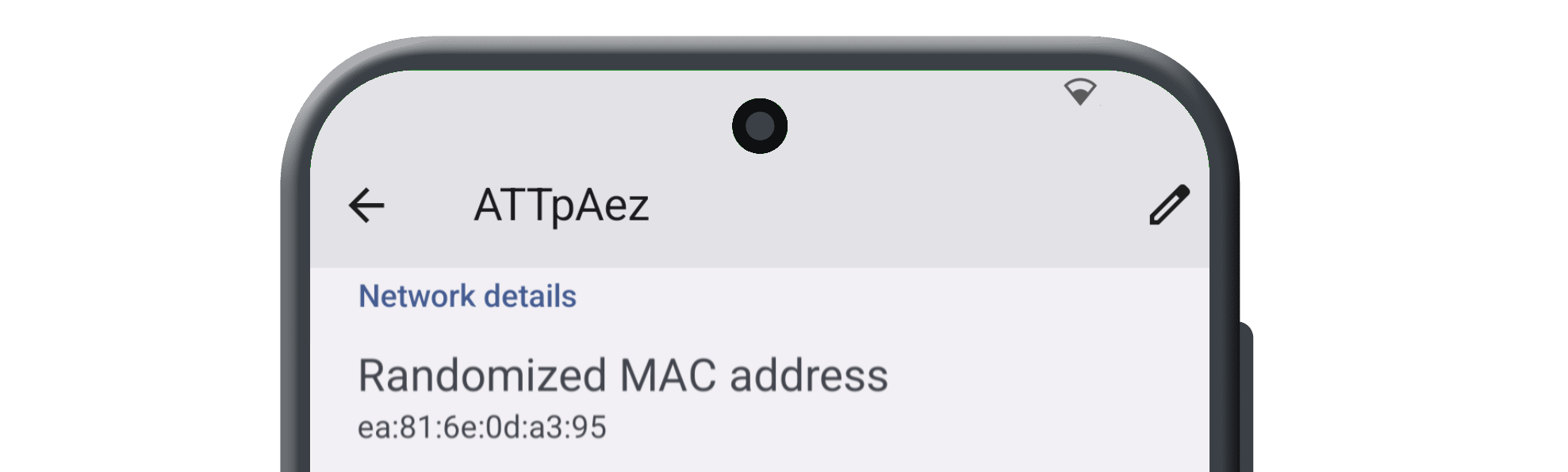
- Built-In MAC Address Spoofer
- Deadman’s Switch (Emergency Factory Reset Protocol)
- Penetration Testing Toolkit
- ZT PRO Support
NOTE: Specs, hardware, RAM, and additional features are chosen during the configuration process, so builds will vary accordingly. Select the build to match your specific needs and budget. Typically ready to ship 7–14 days, based on your build. Read our whitepaper first.
68 reviews for Zero Trace Phone®
Only logged in customers who have purchased this product may leave a review.
Specification: Zero Trace Phone®
| Dimensions | 5 cm |
|---|---|
| Compatibility | APK Extension Application Compatible |
| Update Interval | Monthly |
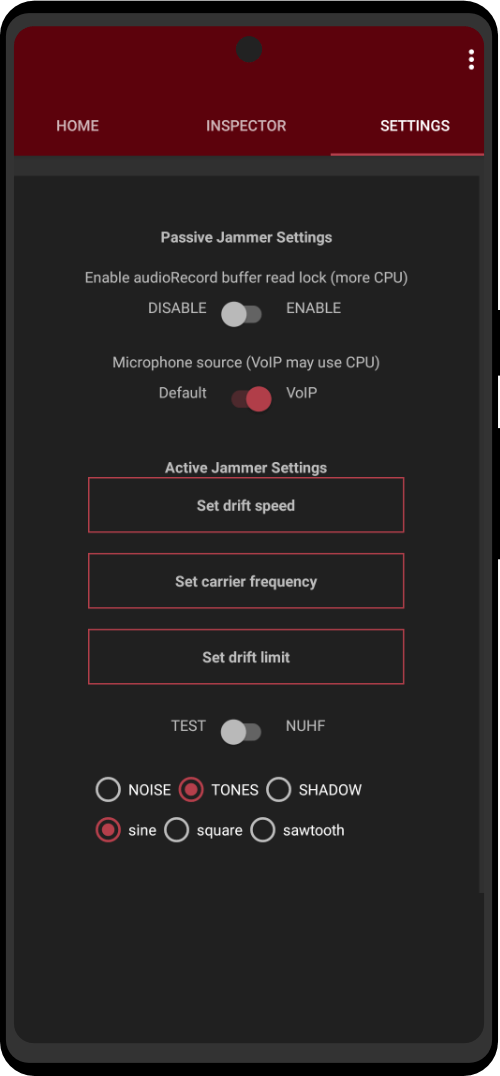
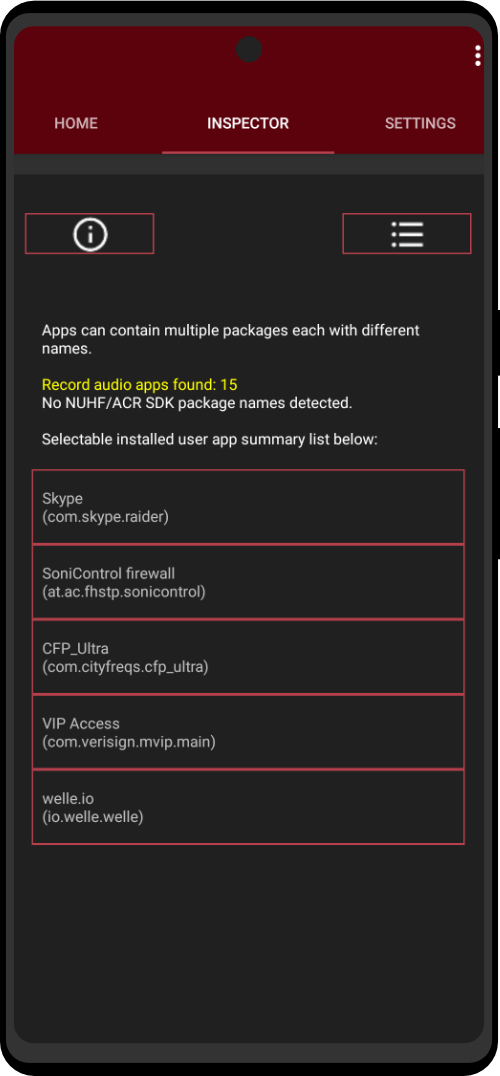
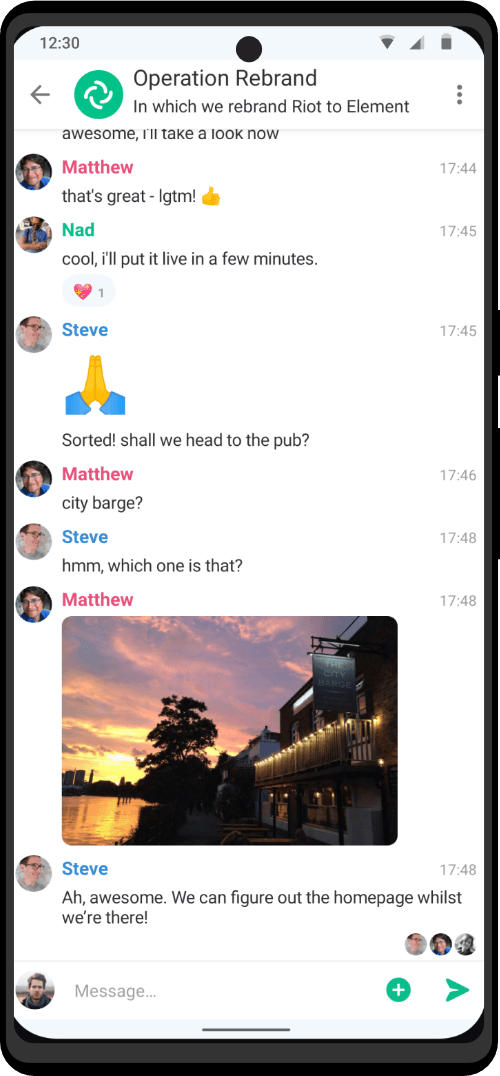
| Utility Applications & Features | KeePassDX, PGP Key, Sandbox, Storage Scopes, Secure Fingerprint, User Profile, Auditor, Element, K-9 Mail, iMessage, Tor Browser, MAC Address Spoofer, Zurf, Mic Jammer, Anti-Stingray, Scrambled Pin, Toggles, LTE-Only Mode, Collabora Office, Exif Scrubber, Private Screenshot, Anonymous Camera, AnonCamera, ZeroPlayer, Nitter, Stealth, Unstoppable Wallet, Location Alert, ZeroMaps |
| Hardware Add-Ons | Built-In MAC Address Spoofer, Deadman's Switch |
| Asset Storage | Non-Custodial Cryptocurrency Wallet |
| Support Priority | ZT PRO Support |











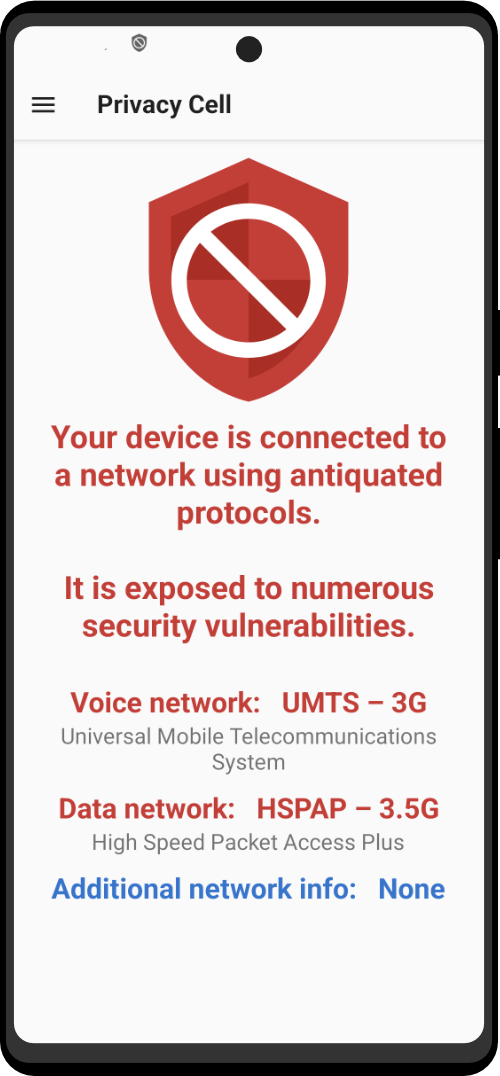
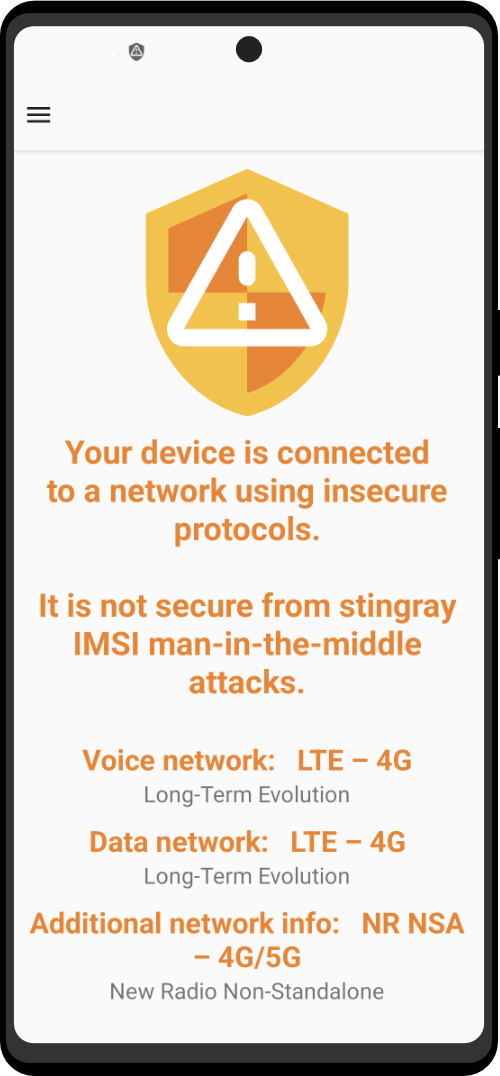
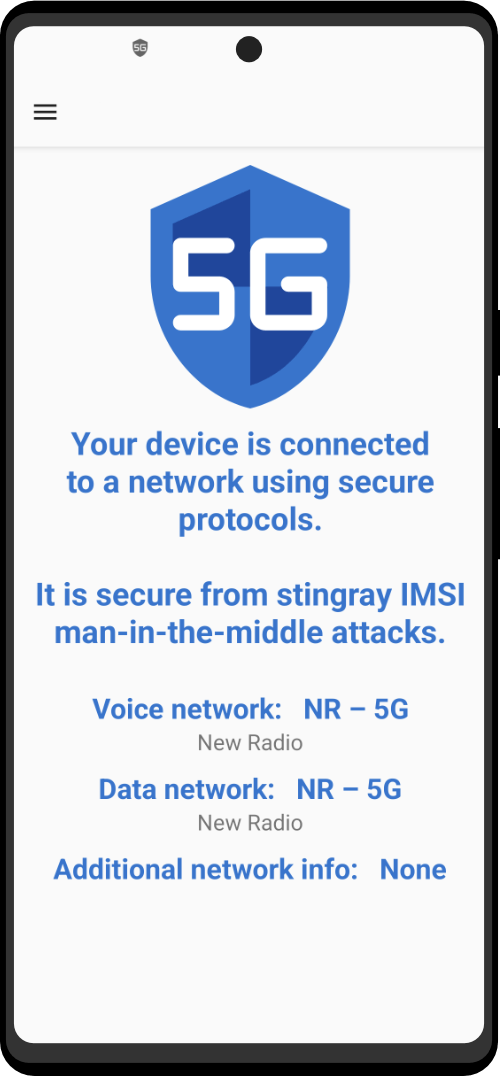
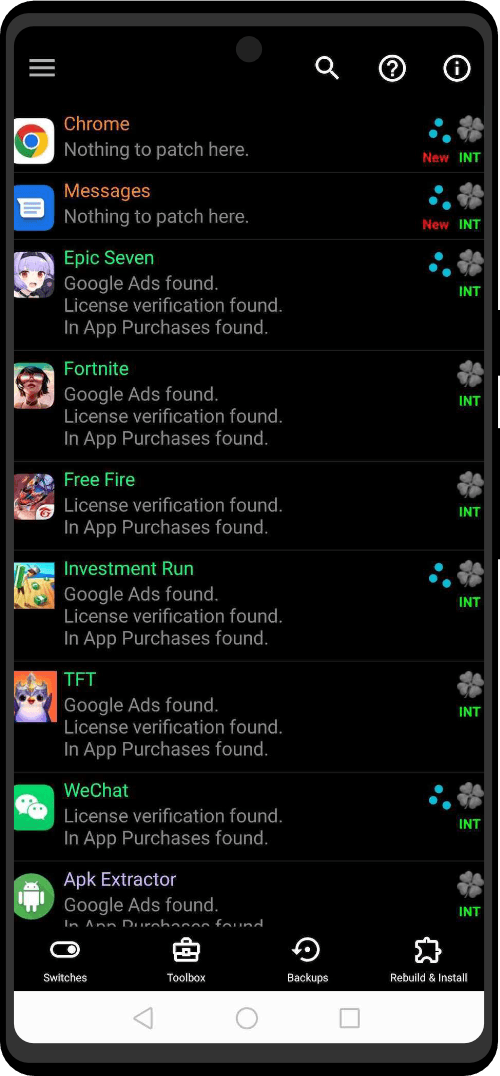
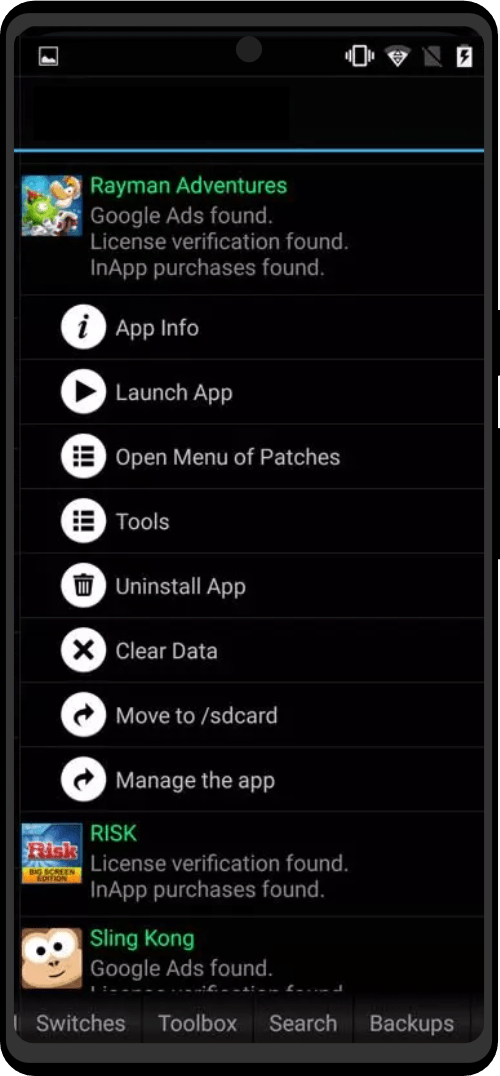


What truly impressed me is the team’s expertise and understanding of the device’s real-life use cases. They don’t hesitate to address any challenges or limitations. Unlike other companies that talk about fighting for freedom, this company actually creates devices designed for practical scenarios where privacy is not a luxury but an essential requirement for operations. The team comprehends this completely.
These devices are truly bulletproof, and I’ll definitely be returning for more Zero Trace phones for my teammates. I’m also planning to get their laptop once it’s ready.
Look, gonna keep it real I grabbed this phone mostly ’cause the whole project sounded kinda familiar and i just HAD to see what’s actually inside, you know? I’m that guy with a lil basement lab full of screwdrivers & microscopes, always breaking open gadgets to peek at teh guts. So I droped the cash, waited a bit (now i get why each unit’s pretty much hand tuned), and wow… the craftmanship blew my mind. Boards were super clean, solder joints neat, no sketchy glue blobs anywhere. I’ve tried “privacy” phones before (not naming names lol) but this one’s on a whole other level if doomsday hit tomorrow this is the burner i’d grab first. Right now the poor thing’s in peices on my workbench while I poke around, but honestly I’m probly ordering another soon to run as my daily driver. Totally worth the splurge.
Alright so I grabbed the phone thinking I’d use it for quick anonymous calls and texts, nothing major, then I started poking through the docs and wow there’s way more happening under the hood than I expected, it basically blocks a ton of everyday surveillance whether you’re walking into a store or hopping on public Wi-Fi, plus the updates roll out by themselves so you’re not forever chasing every new tracking trick, even those random apps that love snooping your gallery or grabbing your IMEI get shut down, I had no clue how many “normal” apps wanted my entire photo library until this thing told me it was blocking them
Honestly I bought it thinking eh just need a burner but it turned into this crash-course vibe in cybersecurity except all the heavy lifting is already baked in, no weird settings to tweak no command-line needed
What really stands out is using familiar apps without the constant data harvesting I've become accustomed to. They make sure to provide either privacy conscious or open source alternatives of apps you'd expect on any phone, such as the calendar, maps, notes, etc. The apps they developed really take care of all your basic needs and some. The MAC address spoofing wrks great when connecting to public network, I tested it using my home wifi's admin panel.
At first look, I was like wow, this is expensive, but now that I have it, it just makes sense how much work they put into it. It’s worth the price and investment.
What I like the most is how I can use social media without worrying they’re just scraping my data in the background. It’s honestly such a relief. Plus, the phone itself is so advanced but super easy to use. There’s no lag or glitches like you get with other phones that still feel like they’re figuring things out. This one feels like it’s already perfected.
Surpassingly, the battery life it’s way better than my iPhone. It lasts so much longer, which makes it even more worth it. On top of that, if you combine it with the anonymous SIM card provider they offer just for Zero Trace phone users, it takes privacy to another level.
If you want a phone that actually respects your privacy and still performs like a top-tier device, this is the one. Like any purchase you gotta trust the team behind it to feel safe and i trust them!
With this, I can collaborate with colleagues on encrypted data without worrying about compromising its security. It's like having a secure meeting room with me wherever I go. The Zero Trace team has also provided excellent documentation and support for implementing all kinds of protocols, making it easy for someone like me who isn't the most tech savvy to achieve a high level of privacy and security.
The Zero Trace phone has many great privacy and security features built right into the phone's system. It uses strong coding to keep things secret, has apps for secure talking, and protects you when browsing the web. This makes it easy for users to stay private and anonymous. It also has special hardware, like a MAC address spoofer, which adds another layer of protection against bad things.
The Zero Trace phone is really well made from a technical view. It works very fast and has lots of storage space. The screen and buttons are easy to use, even for people who aren't great with technology. The battery also lasts a long time, so users can count on the phone to work for a while without making their security worse.
We think the Zero Trace phone is an excellent pick for people and companies who really care about keeping their mobile talks private and secure. The Zero Trace team has shown they will keep working hard to make the phone better over time. This makes us feel good about suggesting the phone for the future.
We highly recommend the Zero Trace phone to anyone who wants a secure, reliable, and feature-packed mobile device. It's clear that the Zero Trace team has worked extra hard to make a phone that sets a new bar in the industry.
If your a serious 'entrepreneur" who values a phone that prioritizes your privacy and won't compromise your location, then you should definitely consider this phone. While it may cost a bit more than your average smartphone, I believe the peace of mind it offers is well worth the investment.