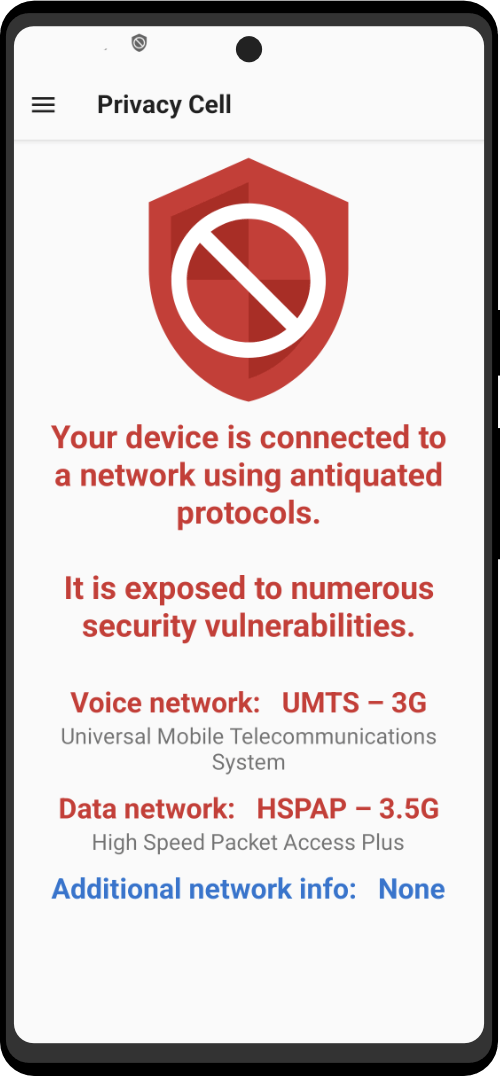
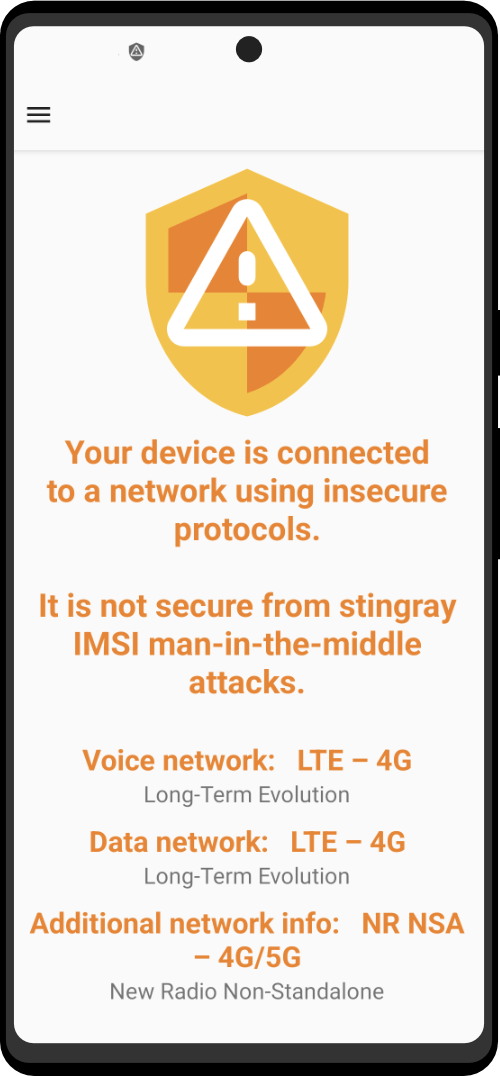
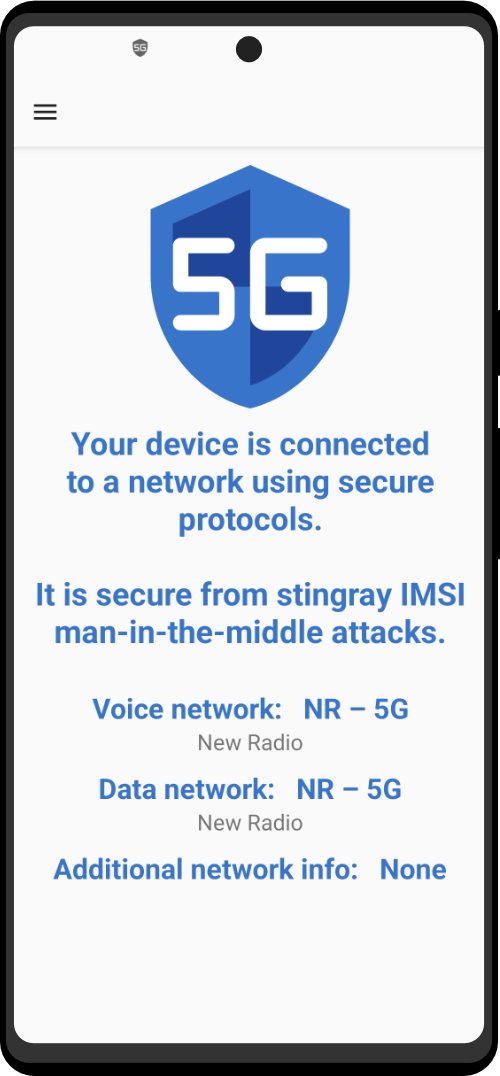
Connecting To A Network
Setting Up Network Settings on Your Zero Trace Pen: A Step-by-Step Guide
Welcome to your journey with the Zero Trace Pen Desktop, your powerful new command center dedicated to secure computing. Imagine a place where all your essential apps sit at your fingertips, ready to fuel your digital adventures with unparalleled privacy and efficiency. But before you dive into those tasks, let’s get you connected to the Internet securely.
Step 1: Access the Command Center
Begin by opening the command center, conveniently located in the upper right-hand corner of your screen. By tapping on it, you can view all the available networks around you. Once you’ve identified your network, go ahead and connect.
Important Note on Privacy
Remember, the Zero Trace Pen is engineered for maximum privacy. Each time you restart the device, it resets itself, ensuring it won’t save your Wi-Fi password or network settings. In another lesson, we’ll explore how to create encrypted storage to save these settings. However, maintaining a ‘clean slate’ is often recommended.
Step 2: Connect to Tor
As soon as you connect, the Tor wizard will appear. Here, you can choose whether to connect directly to Tor or use a bridge. Typically, bridges aren’t necessary because everything is encrypted by default. However, if you require an extra layer of anonymity for special situations, they’re available.
In the Onion Circuit window, you’ll find all the Tor nodes in use to encrypt your activities. While the Zero Trace Pen filters for vetted nodes by default, offering security, you have the freedom to customize your connections for greater transparency. Simply right-click on a node to remove it, and a new connection will take its place.
Step 3: Handling Public Networks
What if you want to use a public network with a login portal requiring agreement to terms of service? Use the Unsafe Browser. This tool helps you bypass restrictions by concealing your use of Tor, allowing the login portal to load correctly. Despite being a workaround for initial access, switch back to the Tor Browser once connected to ensure your activities remain private and secure.
Step 4: Alternative Connection Methods
Alternatively, you can connect the Zero Trace Pen to the Internet using a wired connection. Plug an Ethernet cable into your laptop or tether your phone’s cellular connection using a USB cable.
In Summary
And there you have it! We’ve walked through setting up your Wi-Fi, bypassing public hotspot screens, and exploring different ways to connect to the Internet. With these steps, your Zero Trace Pen is ready to power your secure, efficient browsing.
Create An Encrypted Storage
In this lesson, we will guide you through the process of setting up an encrypted and persistent storage on the Zero Trace Pen. This section is designed to help ensure that all files, settings, apps, and folders remain intact even after the Pen is reset. Secure storage allows you to maintain specific files and settings for easy access and enhanced security.
Setting Up Encrypted Storage
Step 1: Create a Secure Password
- For maximum security, create a password using a string of several words.
- Type your chosen password into the provided boxes and confirm it by typing it again.
- Click ‘Create’ to start the initial storage setup.
Step 2: Completing Storage Setup
- Let the first-time setup run, which will make an encrypted volume available.
- Upon completion, a screen will appear allowing you to toggle the settings for the encrypted storage.
Step 3: Default Settings
- The encrypted storage is enabled by default to ensure a persistent folder in the Files app.
- To save files, simply drag and drop them into this folder.
Configuring Additional Features
Welcome Screen
- Enable this feature to store all configured settings from your Zero Trace session.
- Useful for maintaining administrative passwords and other settings across sessions.
Printer Settings
- If you have set up a printer, ensure this option is enabled.
- This feature will automatically pair your printer each time, streamlining your workflow.
Network Connections
- Save your WiFi networks for automatic connection at startup, eliminating the need to re-enter passwords.
Tor Bridges
- Save configured Tor bridges to hide your usage and eliminate the need to fetch new bridges each time.
Tor Bookmarks
- Bookmark frequently visited sites for easy access on the Tor browser.
Additional Features
Electrum Bitcoin Wallet
- Save your wallet address and keys between sessions, eliminating restoration needs from a Seed phrase.
- Always note your keys elsewhere for security or emergency situations.
Thunderbird Email
- Save email accounts to ensure they’re logged in each time you start the application.
GnuPG (PGP)
- Store PGP keys via Kleopatra for quick encryption and message handling upon system boot-up.
Pidgin Messenger
- Save instant messaging accounts to maintain logged-in status across sessions.
Advanced Features
- SSH into remote desktops or servers (optional for advanced users).
Additional Software
- Install third-party apps that are compatible with Zero Trace Pen.
- Set them to automatically install with each session start in persistence mode.
Dot Files
- Primarily for advanced users dealing with system-specific settings.
Maintaining Security
- If needed, change your password to enhance the security of your encrypted storage.
- Erase all saved settings and files if you wish to return the Pen to its original state.
Conclusion
Through these steps, you have configured your Zero Trace Pen for secure and seamless operation. Whether connecting to WiFi, printing documents, or engaging in secure communications, the setup ensures productivity and protection. With Zero Trace, you’re not just protected—you’re empowered to explore fearlessly and safely.
Always remember to unlock your storage at the greeting screen. If you don’t, then you will not have access to your files or apps you’ve configured inside your persistence.