Zero Trace Pen®
Price range: $99.00 through $147.00
All-in-One Tor Network Anonymous Flash Drive + Cold Storage Cryptocurrency Wallet
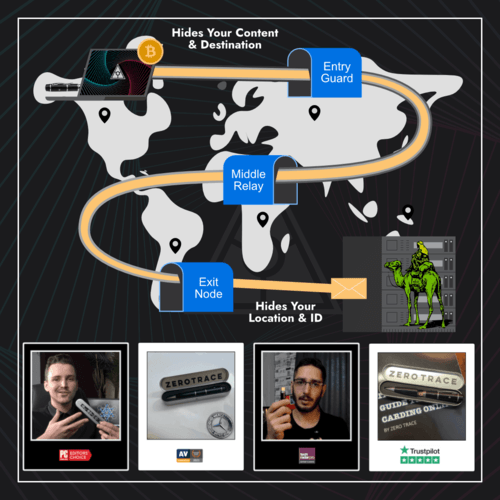
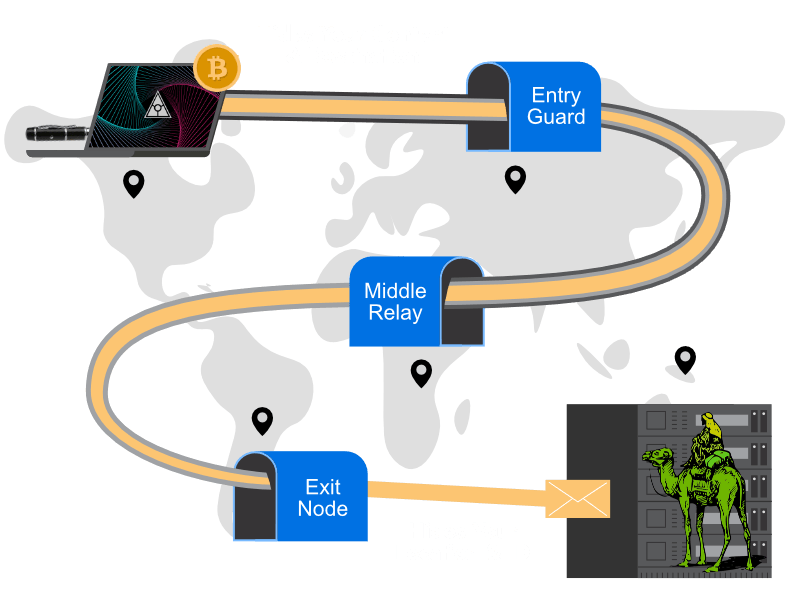
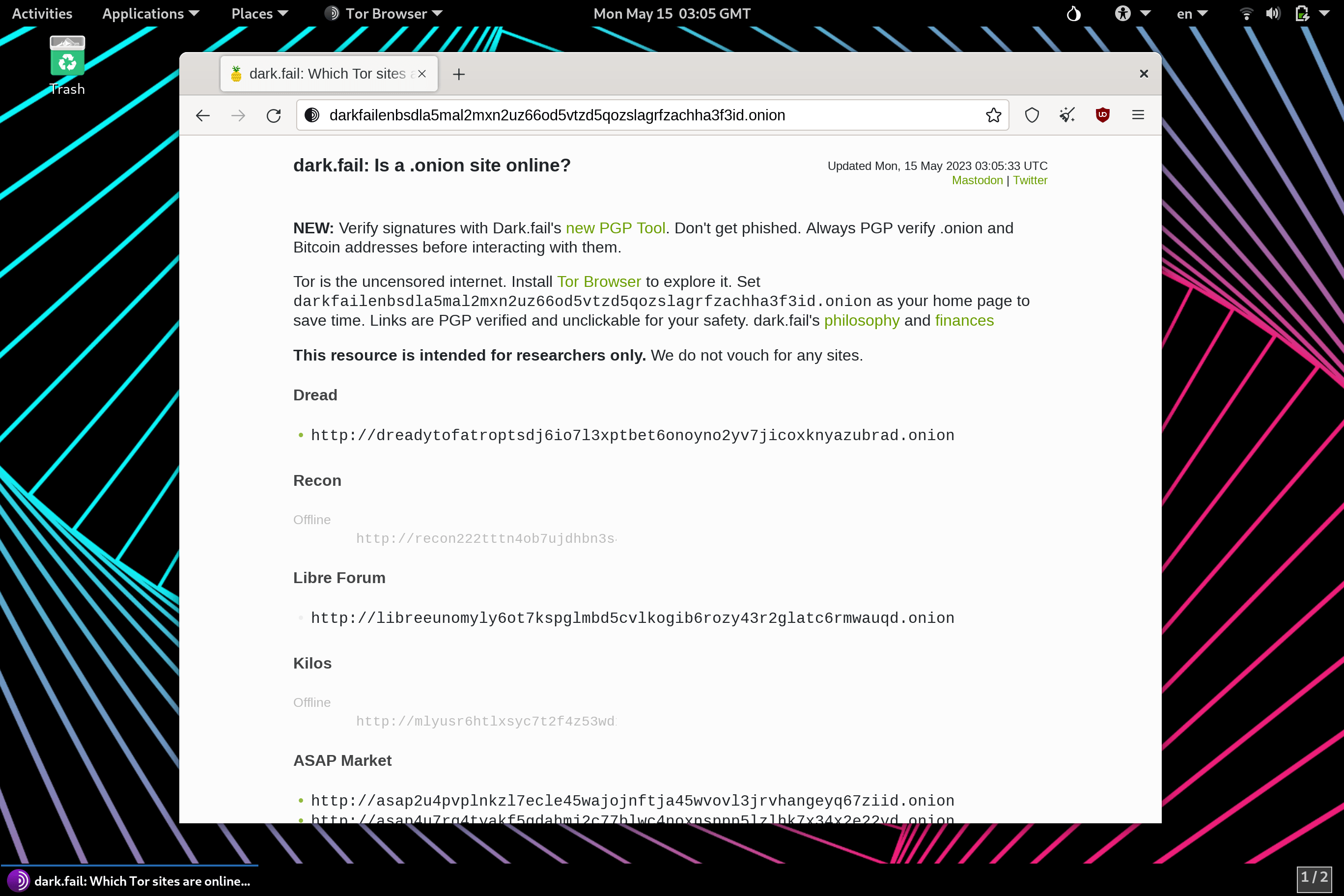
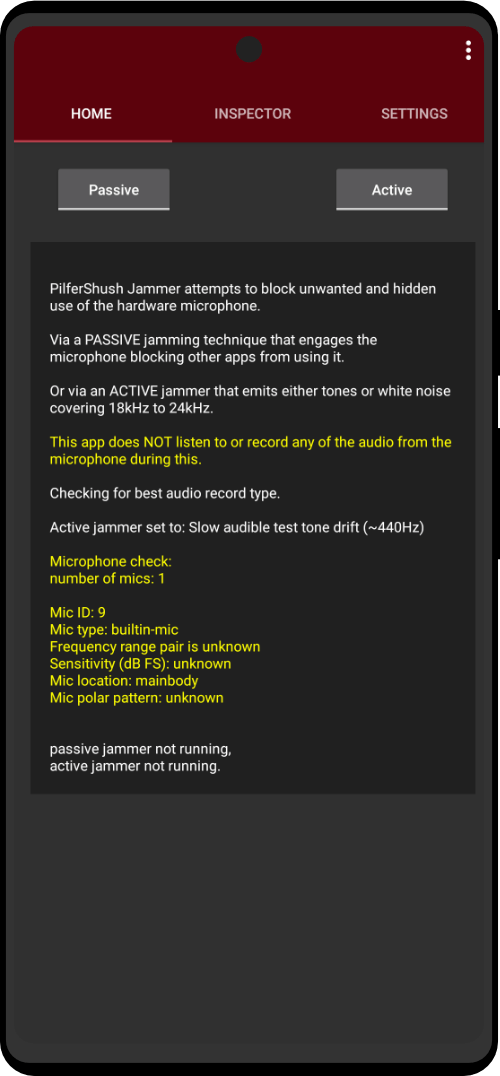
Zero Trace is a hardware modified flash drive with everything you need to stay anonymous. Being completely portable, you can access the Tor network on any computer from the USB port, anonymously from the Zero Trace Pen. (Clearnet | Dark Web | Darknet | Deep Web Compatible)
-
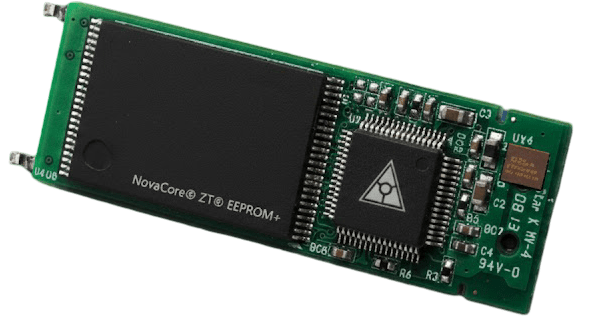
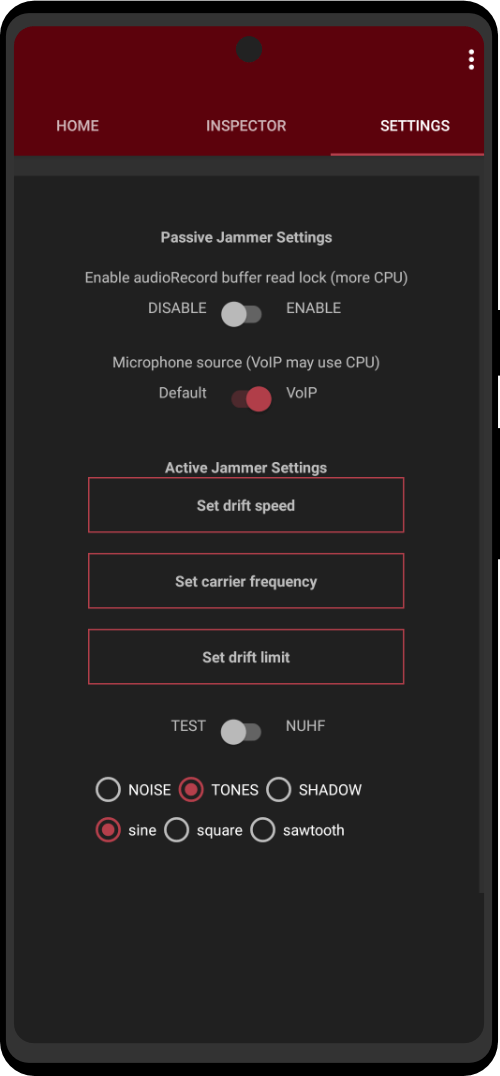
- NovaCore® ZT® EEPROM+ Processor
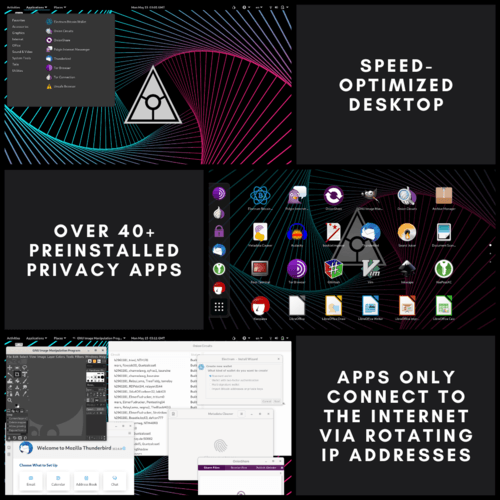
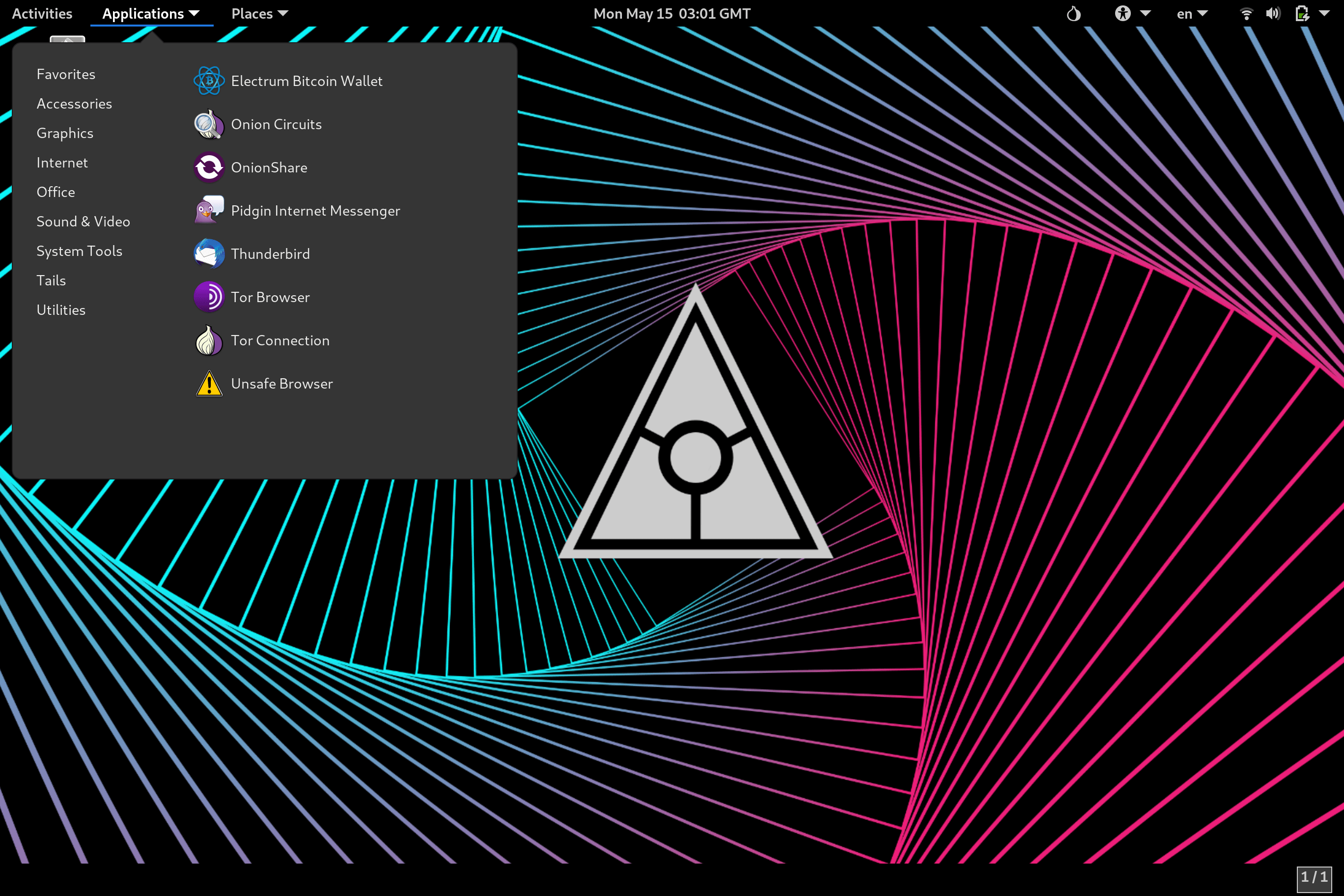
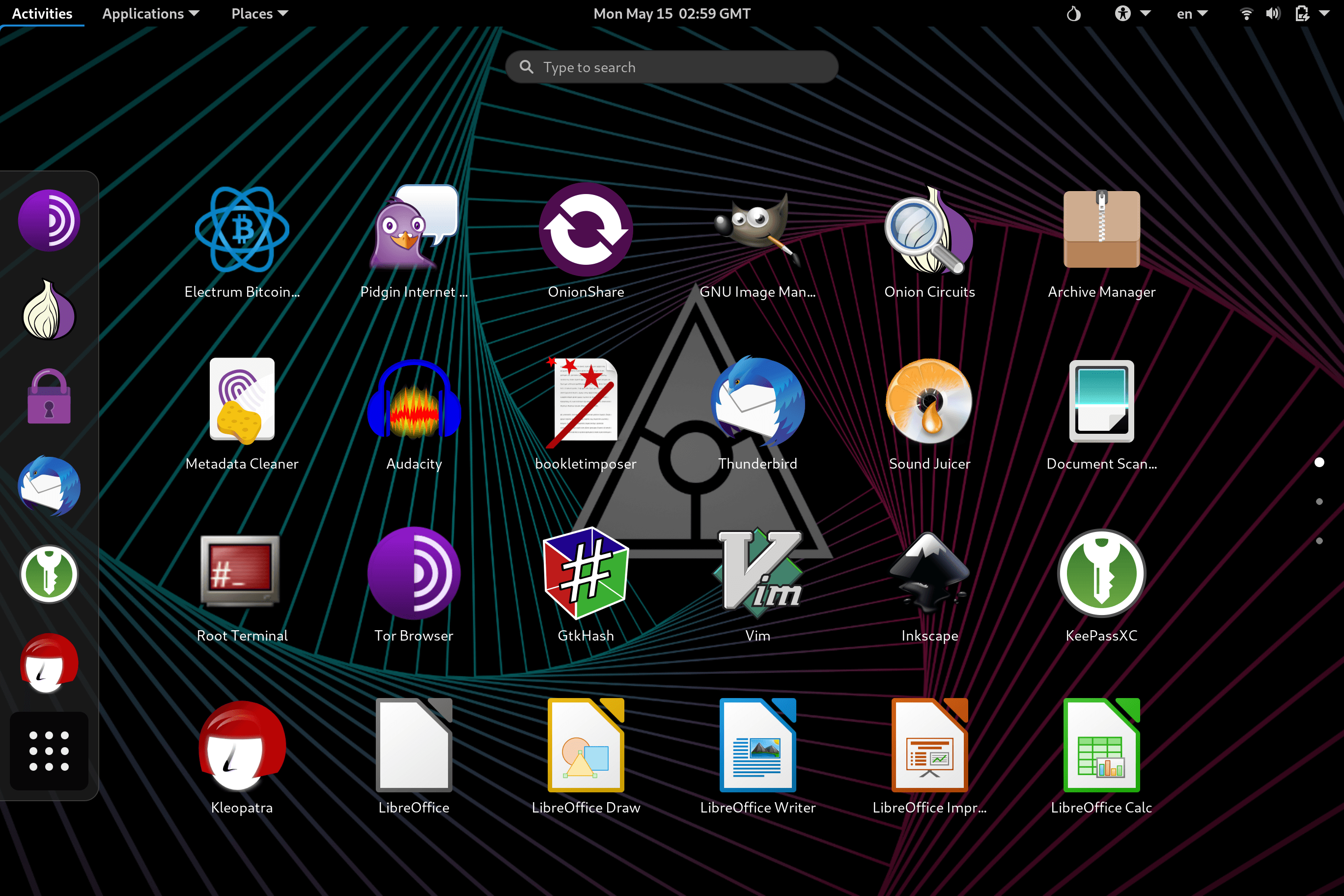
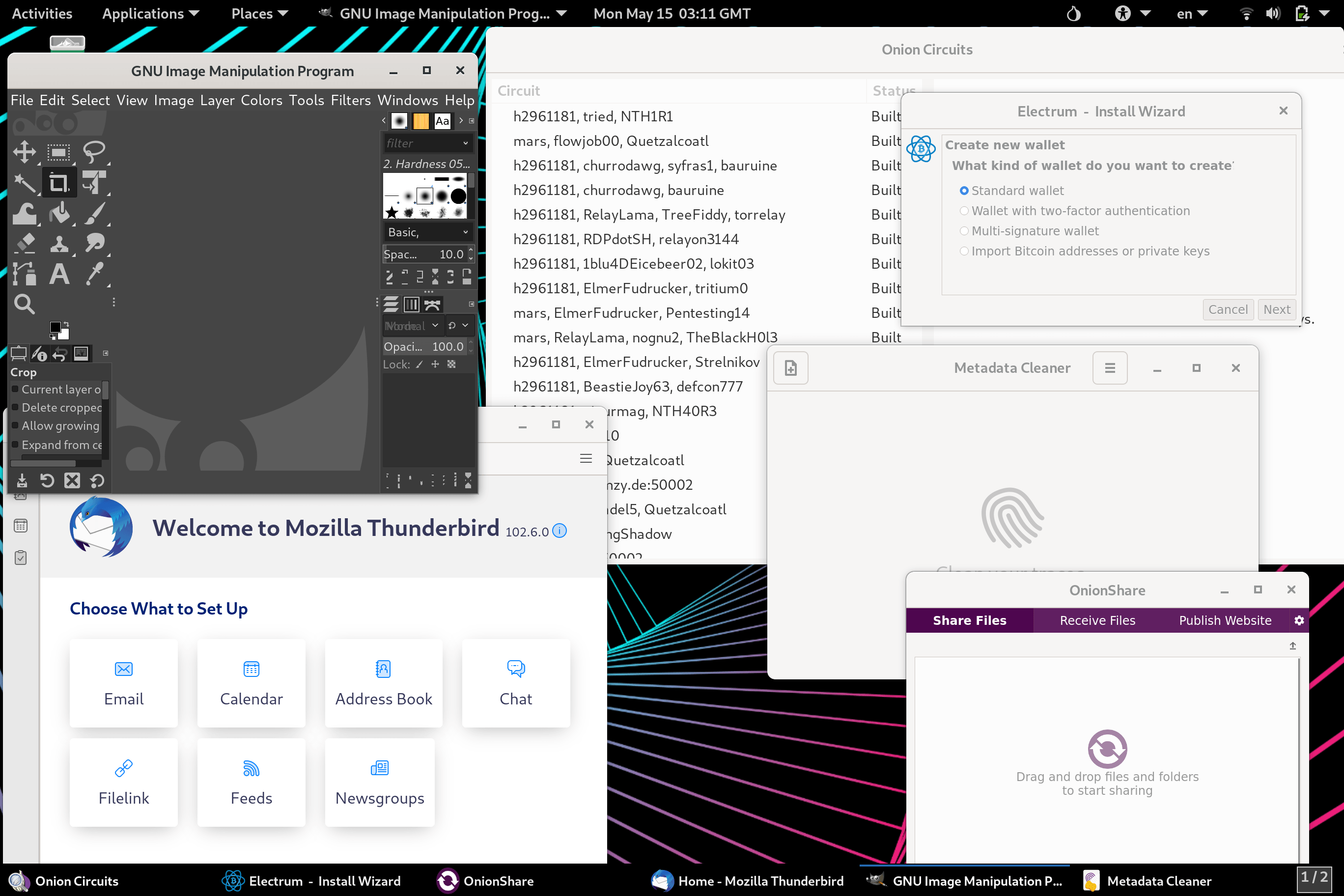
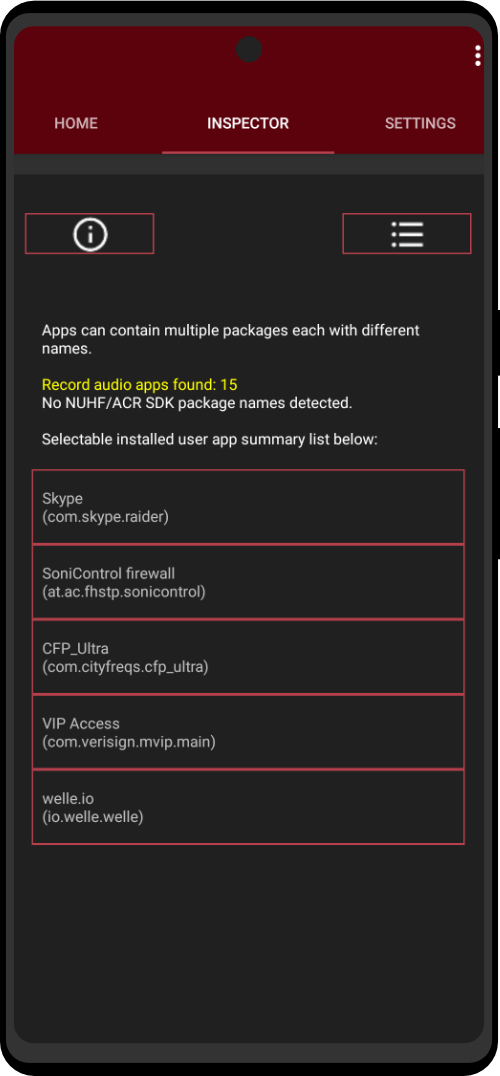
- 40+ Pre-installed Privacy Apps
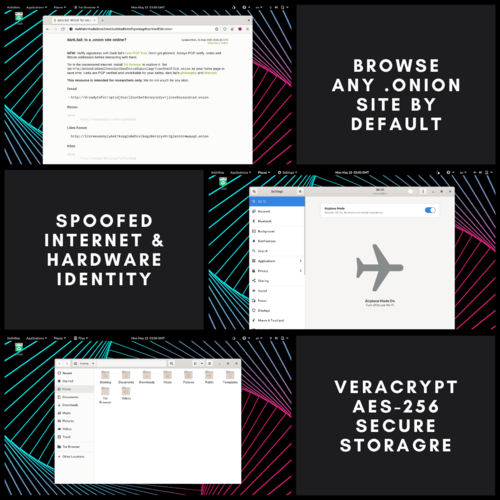
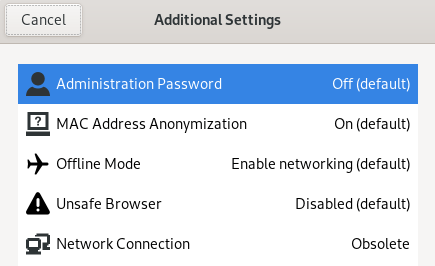
- Built-In Hardware MAC Address Spoofer
- Double Kill Switch (WiFi & RAM)
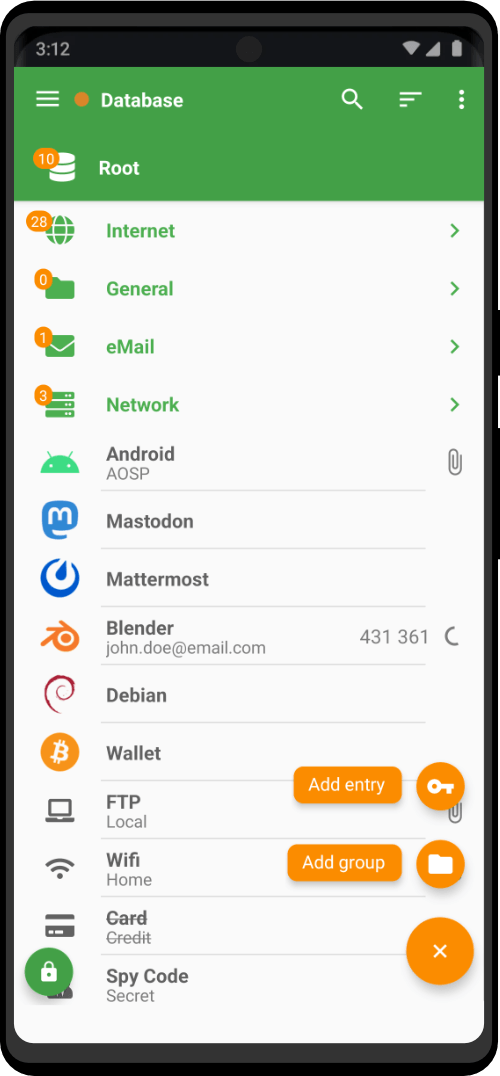
- Cold Storage Cryptocurrency Wallet
126 reviews for Zero Trace Pen®
Only logged in customers who have purchased this product may leave a review.
Specification: Zero Trace Pen®
| Compatibility | Windows, macOS, Linux |
|---|---|
| Update Interval | Monthly |
| Utility Applications | Aircrack-ng, Archive Manager, Audacity, Bookletimposer, Brasero, Calculator, Dasher, Disks, Document Viewer, Electrum Bitcoin Wallet, File Manager, GNU Image Manipulation Program, GtkHash, Help, Image Viewer, Inkscape, KeyPassX, LibreOffice, LibreOffice Calc, LibreOffice Draw, LibreOffice Impress, LibreOffice Writer, MAT (Metadata Anonymization Toolkit), Onion Circuits, OnionShare, Passwords and Keys, Pidgin IM Client, Poedit, Power Statistics, Root Terminal, Screenshot, Screenshot, Search For Files, Settings, Simple Scan, Sound Juicer, Sound Recorder, Synaptic Package Manager, System Monitor, Documentation, Terminal, Text Editor, Thunderbird E-mail Client, Tor Browser, Unlock VeraCrypt Volmues, Unsafe Browser, Videos, WhisperBack |
| Hardware Add-Ons | Built-In MAC Address Spoofer, Double Kill Switch (WiFi & RAM) |
| Asset Storage | Cold Storage Cryptocurrency Wallet |
| Type | USB Type A, USB Type C |
















There are no reviews yet.