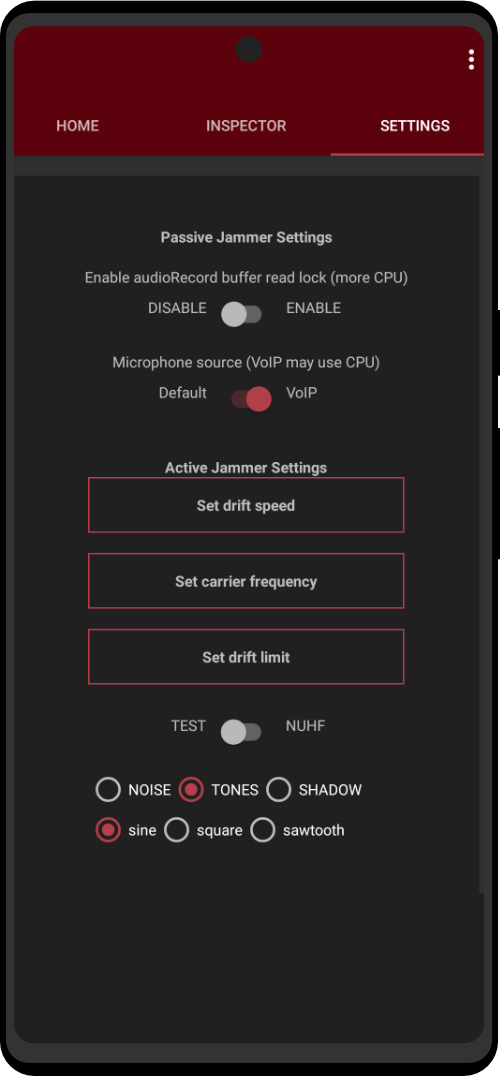
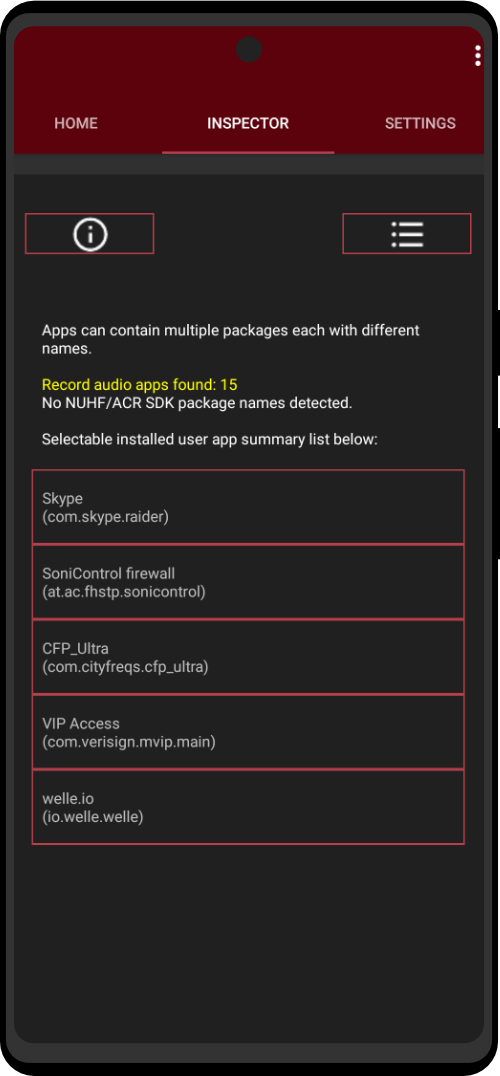
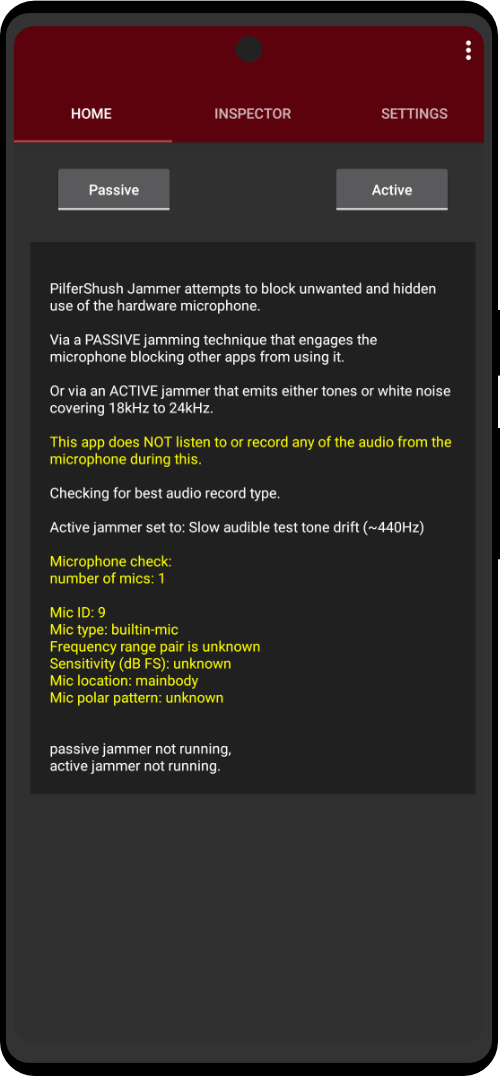
In the dystopian society we live in today, surveillance is a major part of how governments keep the common folk in line. To understand how we can use misinformation against them we first must understand how are we being tracked. Entities that track us (government agencies, tech conglomerates, and data mining companies) rely on you to leak little pieces of data which they use to profile you online and match the username to the actual user. It’s a simple matter to match content in databases if there is some sort of index to the content. The most common pieces of data used to track you on clear-net and dark net are:
- Names (both real and usernames)
- IP addresses
- Browser fingerprint
- E-mail address
- Location (exact or approximate)
- Phone numbers
- Date of birth (or any other PII)
- Stylometry
- Facial recognition
It’s important to understand that just using two elements out of all of these is enough for them to track you. So your job is to deny them from getting two pieces of real data if you wish to stay anonymous.
People who work in certain fields may have different views as to who the adversaries might be. To a cyber-security analyst, it would-be hackers. For military people, it would be enemy military forces. To a person on the darknet, it would be law enforcement. However, one of the most important things to understand about OPSEC is that anyone who does not need to be involved with what you are doing should be viewed as an adversary.
This is because people who are not your primary adversaries can still cause major problems for you if they know you are doing something that is illegal, taboo, or requires confidentiality. And nothing beneficial to you can come from others knowing that you are doing something along those lines.
Maintaining good operational security is much more complicated than simply using Tor browser and PGP to encrypt messages. It’s a long journey that requires a lot of work and really understanding all of the aspects, technical and otherwise, of doing things with the most discretion and anonymity possible.
It should be noted that government agencies around the world are always actively attempting to de-anonymize Tor users and that proper procedures need to be taken when using anonymity networks like Tor or else you risk being de-anonymized.
An example of bad OPSEC would be to download Tor browser from your home network with your laptop PC and start using the darknet or doing illegal activity on the clearnet. This is because of the following reasons:
- The government has a surveillance program known as X-keyscore. People who end up on the watch list are more likely to have their internet traffic monitored and their computers hacked and infected with malware that sends eavesdropping information back to the NSA.
- Windows is a closed-source, proprietary software that is made by Microsoft, a company that works closely with the government. It has many security issues and is blatantly more susceptible to malware and spyware than other operating systems such as Unix and Linux. Since it is closed-source, there is really no way of knowing if there are back doors built into the system or how much Microsoft is really collecting information and user data. Some say they found that all of their keystrokes were being sent to Microsoft after analyzing their traffic with Wireshark on Windows 10. All versions of Windows since 95 have NSA cryptography keys built into them, which has led to speculation that the NSA has back-door access to all Windows computers. Do not use Windows when attempting to do anything anonymously online.
- The webcam and microphone need to be disabled or preferably removed from the device. This is because if your computer is compromised, the attacker has the potential to see both you and everything you are doing on your computer at the same time. If you uninstall the drivers, the attacker can re-install them. If you put a piece of tape over your webcam, the attacker can still listen to you and your keystrokes, each of which emits a unique sound that can be deciphered using certain software in order to find out which keys you are pressing, which allows them to find out everything you are typing, somewhat like a keylogger. This is more likely if the attacker is government.
- Tor Browser was made for anonymity, NOT security. When you are browsing .onion sites on Windows and you visit one that is malicious, your PC can be infected with malware. Although the risk is reduced when you disable Javascript and set your Tor browser’s security level to “safest”.
As you can probably tell by now, using tor alone will not protect you, and you are going to have to really go out of your way to make sure that nobody, especially the government, can find out what you are doing. Some people are not concerned if the NSA is watching them, maybe it’s because they don’t consider themselves to be “big fish” and that the NSA is not a law enforcement agency, so they don’t worry. If that is what they think, they are terribly mistaken. The NSA permanently stores the data and they can tip off law enforcement agencies. They can not legally have people arrested based on evidence they obtained without a warrant, so they have to find out ways to collect the evidence legally, which is much easier for them to do if they already have hidden spyware on the target’s PC. Keep in mind that if they decide to target you, they can do it at any time.
People who were involved with the original Silk Road marketplace and other earlier markets are still being arrested. It may not have been the case that they knew who those people were and decided to wait years to arrest those people, it’s unlikely but still possible, but it’s more likely that those people did something more recently that some government agency picked up on that linked their identities to their old darknet profiles. However, what we know about the NSA is mainly from the leaks put forth by Edward Snowden in 2013, about 8 years ago. It is highly likely that their technologies and methods have advanced since then.
Back in the early days of darknet markets, people usually used encryption, which can now be cracked. And the government still has all of those messages from the markets they seized, which means they can read a lot of encrypted messages exchanged between buyers, sellers, market administrators, and a lot of other people from almost a decade ago, which means the government has a lot of evidence and maybe the most likely reason as to why those people are still being caught. This serves as an example of why you need to think ahead and make sure that nothing you do can ever be discovered regardless of the advancements in technology or what the government becomes capable of.