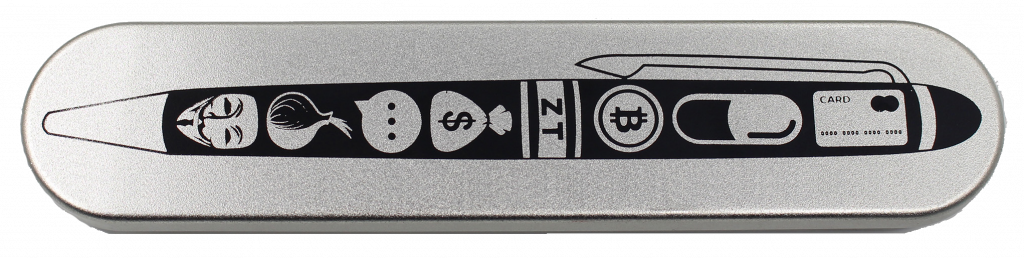
ztPen
Invisibility
Made for the builders.
The most secure build of any portable PC. Ever.

ztPen
Release 5.15a-ZT1
Zero Trace is an all-in-one hardened drive with everything you need to stay anonymous. Being completely portable, you can access the Tor network on any computer from the USB port, anonymously from the Zero Trace Pen.
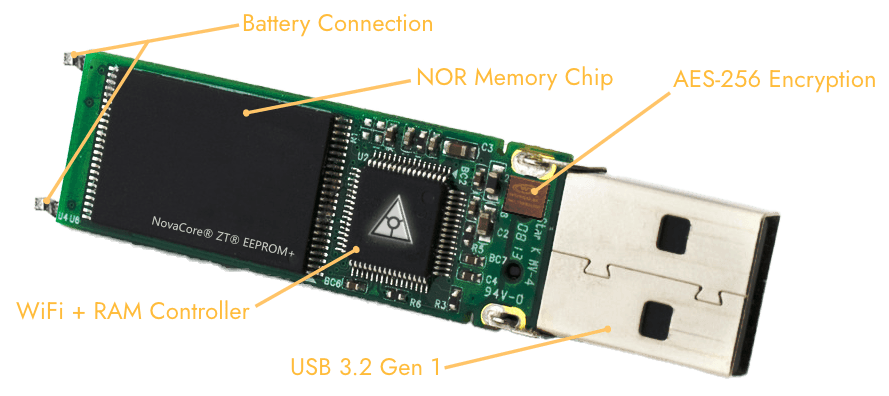
NovaCore® ZT® EEPROM+ Chip
Serious protection inside and out
Everything you do from within the Zero Trace Pen is encrypted. This means if you communicate or transact with any of the 40+ privacy apps included – you will be completely safe and anonymized.
30 Day Guarantee With Free Returns
How Is Zero Trace Any Safer?
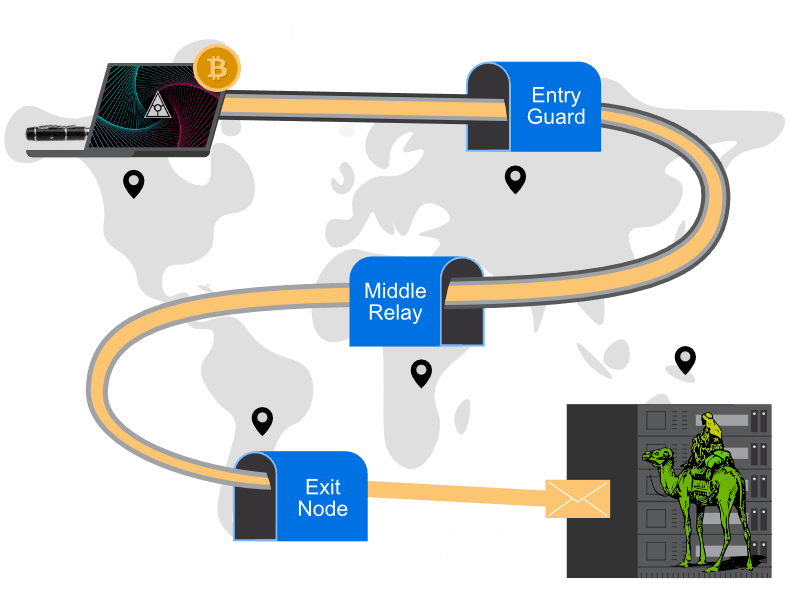
Right now, everything you do on the Internet goes through your ISP (aka Internet Service Provider), this includes anything you do inside your VPN as well. Our Zero Trace Pen encrypts and anonymizes your entire connection by passing it through 3 different relays just like the Tor Browser. However, encryption happens at the operating system and hardware level . This means, you can browse applications and the internet completely anonymous without worrying about being tracked – digitally nor physically.
Q – Why not just use a VPN on a Windows or macOS PC and be extra careful?
A – They can easily track MAC addresses with a click of an NSA button.
How Do They Do It?
In order to find a laptop by the MAC address of the network adapter, they need to contact the law enforcement authorities. They will be able to search for it after they sign a release allowing your laptop to be traced via their honeypot WiFi networks.
MAC Address
A MAC address is a hardware identification number that uniquely identifies each device on a network.
Honeypot
A honeypot is a security mechanism that creates a virtual trap to lure activists. An intentionally compromised network system allows them to identify you.
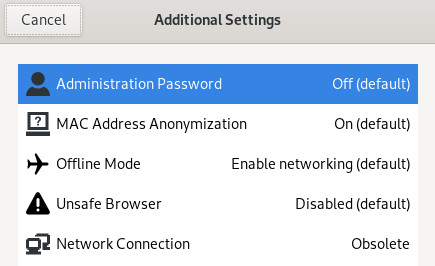
Introducing MAC Randomization
Connect to any network, completely anonymous.
The Zero Trace Pen randomly assigns your computer a new MAC address every time you use it. The OS does this at a software level, the Zero Trace Pen reinforces this at a hardware level. Organizations running honeypot networks will not be able to identify you.
The Zero Trace Pen is an innovative device that enhances user privacy by randomizing your MAC address at the hardware level. This is achieved through its built-in MAC address changer NovaCore® ZT® EEPROM+ ROM Chip, which is strategically placed inside the pen adjacent to the batteries. By forcing your network connection to pass through this advanced chip, the Zero Trace Pen effectively alters your MAC address, ensuring that the physical identifier of your device remains concealed from prying eyes. This hardware-based solution offers superior protection, as it directly modifies the MAC address, rather than relying on software-based randomization techniques.
Prevent IP Leaks
Without The Pen You Are Exposed
Here are some ways that using a VPN on Windows or macOS might not be as safe as you think:
External applications: When you open an external application or document while using the Tor Browser, it is not routing its traffic through the Tor network. As a result, your IP address and other identifying information will be exposed, compromising your anonymity.
Browser fingerprinting: Despite Tor Browser’s efforts to minimize browser fingerprinting, adversaries may still be able to use advanced techniques to uniquely identify your browser based on the Windows or macOS environment, such as screen resolution, installed apps, and font settings. This can lead to tracking and identification.
Malware and malicious websites: Tor Browser does not protect you from malware or malicious websites. If you unknowingly download or interact with malware, your system could be compromised, and your identity exposed
Activities outside the Tor Browser can potentially expose your identity, as the browser’s protection is limited to its own environment. The Zero Trace Pen prevents the possibility of this happening by encrypting the entire computer.
30 Day Guarantee With Free Returns
Mask Your Identity
Prevent others from spying on you
The Zero Trace Pen prevents others from spying on your internet activities and learning what you are doing online. By using the Zero Trace Pen you prevent any website you visit, from learning where and who you are.
Absolutely everything you do from within the Zero Trace Pen is FORCED via the Tor network. This includes all pre-installed applications as well.
You will be able to manage a social media account entirely through the Zero Trace Pen. If you only access them from the pen, they cannot be traced to you. You will also be able to store documents and images related to your different identities all via the preinstalled applications. Keep your passwords in KeePassXC and have a dedicated email account in Thunderbird, etc.

“I didn’t realize how much location data was stored in my photos.”
Mask Your Identity
Prevent others from spying on you
The Zero Trace Pen prevents others from spying on your internet activities and learning what you are doing online. By using the Zero Trace Pen you prevent any website you visit, from learning where and who you are.
Absolutely everything you do from within the Zero Trace Pen is FORCED via the Tor network. This includes all pre-installed applications as well.
You will be able to manage a social media account entirely through the Zero Trace Pen. If you only access them from the pen, they cannot be traced to you. You will also be able to store documents and images related to your different identities all via the preinstalled applications. Keep your passwords in KeePassXC and have a dedicated email account in Thunderbird, etc.
“I didn’t realize how much location data was stored in my photos.”
Emergency Protocols
Automatic File Purging
The Zero Trace Pen always boots up from the same clean state and everything you do disappears automatically the second you shut it down. We have also implemented emergency purging protocols at a hardware level that activate by removing the pen from your computer. This means, regardless of what you’re doing, you can easily just pull out the flash drive and your PC will automatically start erasing all your activities and make them completely inaccessible. Regular flash drives execute their purging protocols while connected to your PC, this leaves you vulnerable to cyber attacks.
- The Zero Trace Pen doesn’t have this issue. Equipped with a battery powered double kill switch – you can be sure your Internet connection and RAM data has been cleared, even after you disconnect.
- The same battery also powers a neat laser pointer – allowing you to check it’s power level and disguise the pen’s primary use when passing through metal detectors and TSA.
Need To Save A Few Files?
Optionally, you can save some of your files and configuration on a secure storage folder on the USB stick: your documents, your browser bookmarks, your emails, and even some additional software. Everything will be double encrypted through the NovaCore® ZT® EEPROM+ using VERACRYPT technology.
Malware Proof
Utilize From Anywhere
To use the Zero Trace Pen, we recommend you shut down any computer and boot up the Zero Trace Pen instead of starting Windows or macOS. You can turn any computer into a secure anonymous machine before you start handling business matters.
Finished using the Zero Trace Pen? Unplug it and use the computer like normal, there won’t be any evidence of whatever you were researching prior.
Best of all, you don’t have to worry about catching viruses, because the Zero Trace Pen runs independently from your regular operating system and never uses the hard drive. In fact, you can use the Zero Trace Pen on a computer that has it’s hard drive completely removed!
30 Day Guarantee With Free Returns
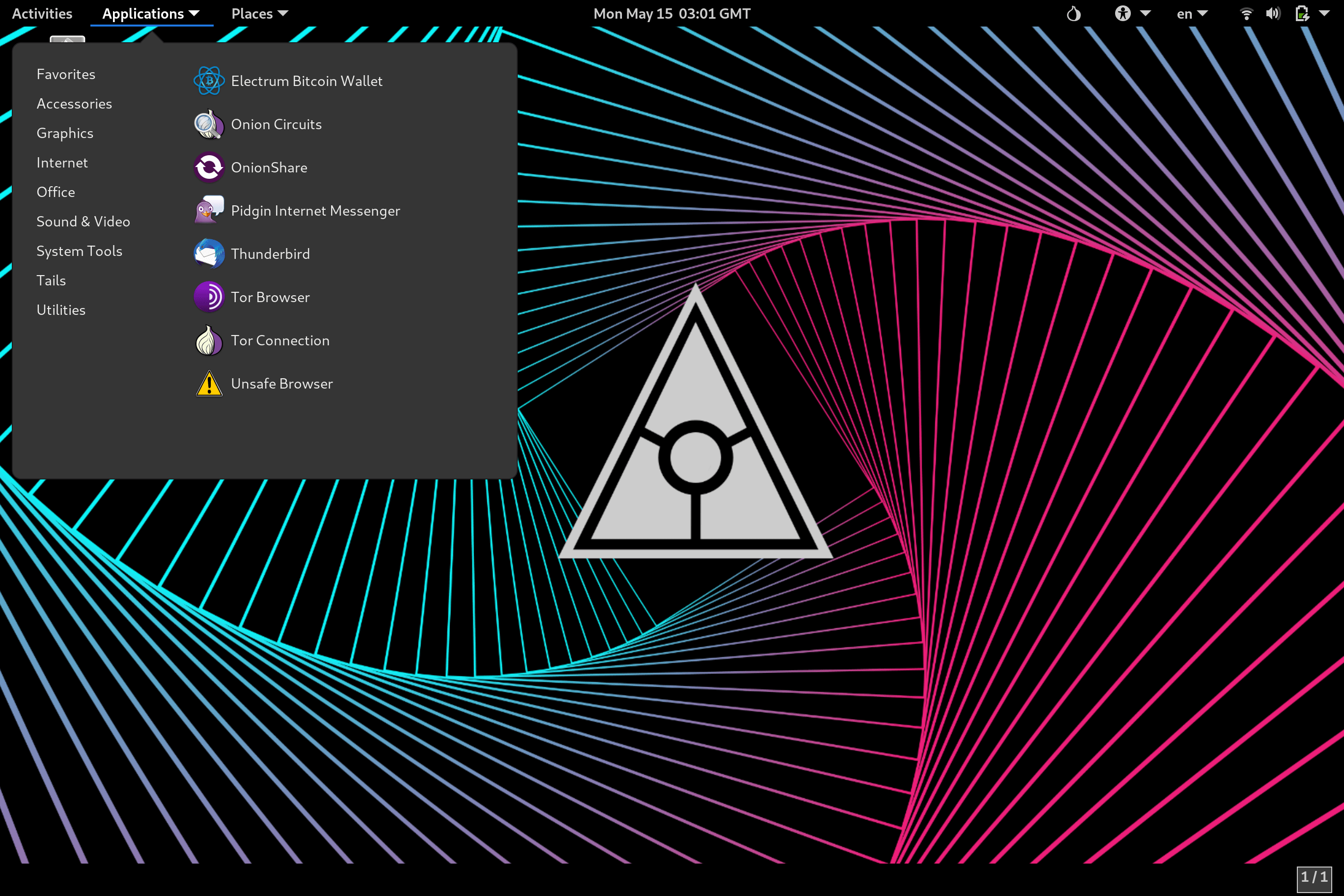
Digital Security Suite
The Zero Trace Pen includes 40+ premium applications to open sensitive documents,
communicate securely & perform penetration testing.




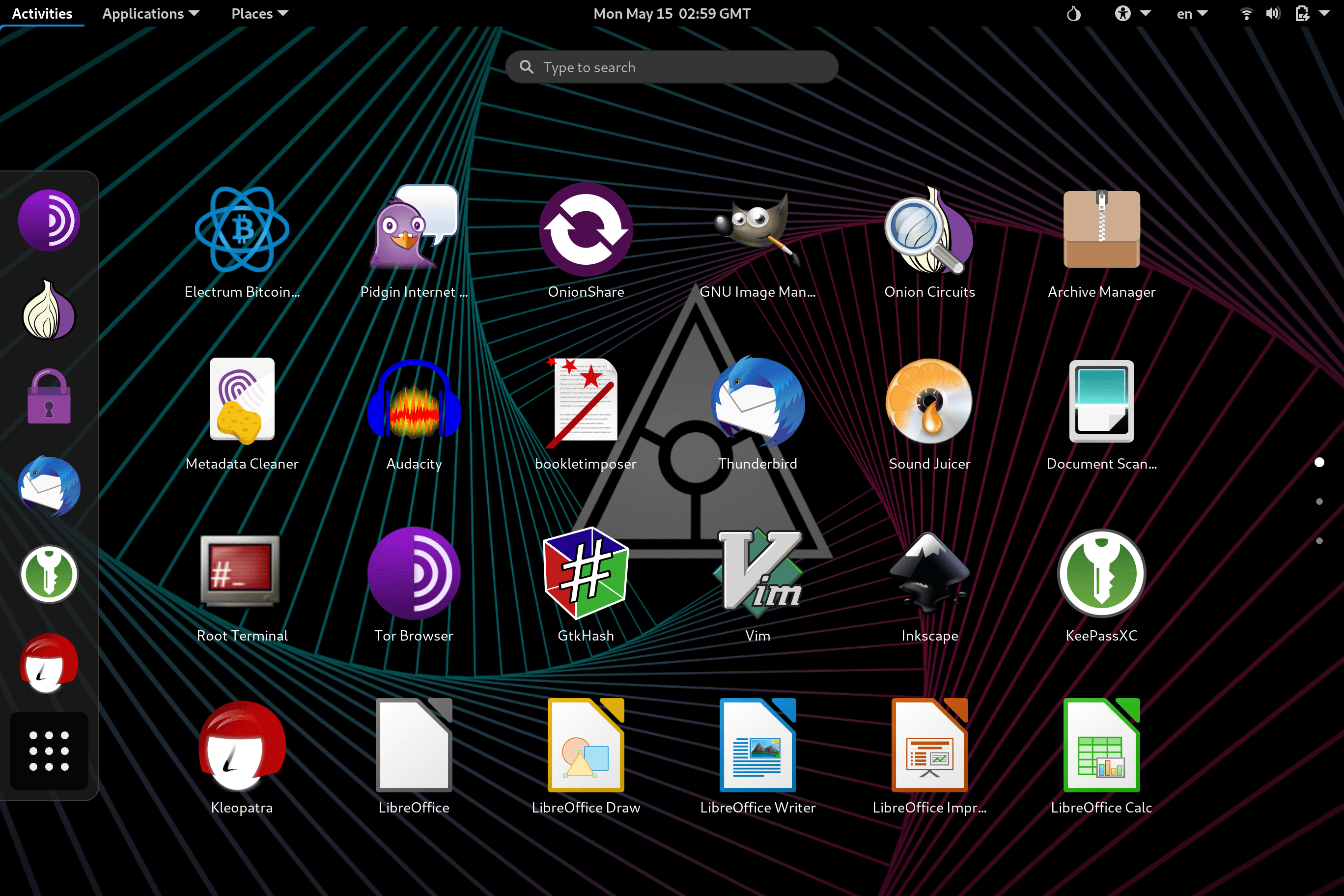
Tor Browser
Electrum
Thunderbird
LibreOffice
Pidgin
Tor Browser
Tor is a special browser that hides your IP Address and location every time you visit a website. This is extremely important if you need your browsing to remain anonymous
Electrum
The Electrum wallet will come incredibly handy when conducting business with cryptocurrency. Due to the fact that Electrum is running on the Zero Trace drive, it means all connections are sent via the Tor Network. This means your transactions will remain private.
Thunderbird
Thunderbird is a program that offers a range of privacy options for all of your email needs. You can use it to login to almost any of the popular email providers with complete anonymity. Thanks to Zero Trace, all of Thunderbird’s activity will be sent through the Tor Network.
LibreOffice
LibreOffice is a Microsoft Office compatible suite of apps for creating and opening text documents, spreadsheets, and presentations. This is a great tool if you plan on downloading and viewing eBooks, guides, tutorials, and other sensitive documents.
Pidgin
Pidgin is a program that lets you log in to your accounts from multiple chat apps. Due to the fact that many Fortune 500 companies, activists, and military personnel prefer to communicate via ICQ, IRC, and XMPP, this app will help you chat with whomever you need to privately and anonymously.

Aircrack-ng
Test Any WiFi Password
We have incorporated one of the most popular network auditing tools into the Zero Trace Pen . With this tool you will be able to crack any WiFi password with ease. Need to test the security of public/private WiFi networks - on the road? We got you covered.
Security Protocols
- Applications are blocked automatically if they try to connect to the Internet without Tor.
- Everything saved in the secure storage folder is stored on the encrypted NovaCore® ZT® EEPROM+ ROM Chip.
- Zero Trace does not write anything to the hard drive. All the memory is deleted digitally and physically the second you shut down.
“I created a darknet market using the Zero Trace Pen in about 5 minutes.”
VeraCrypt® AES-256 Encryption
Cold Storage
Cryptocurrency Wallet
We created an ecosystem that lets you simply manage, secure and control your crypto assets.
When you own crypto, what you really own is a private key – this key gives you access to your coins. You should be the only one in control of this key & you also need to secure it. The Zero Trace Pen offers the best level of protection and control: our hardware wallet is the best way to secure your funds while giving you the freedom to manage everything on your own.
Your private key always remains protected in the hardware wallet – in a certified secure chip. Nobody can access it except you. Combined with Electrum, everything about crypto is made simple and secure: buy, send, receive digital assets with one-single app.

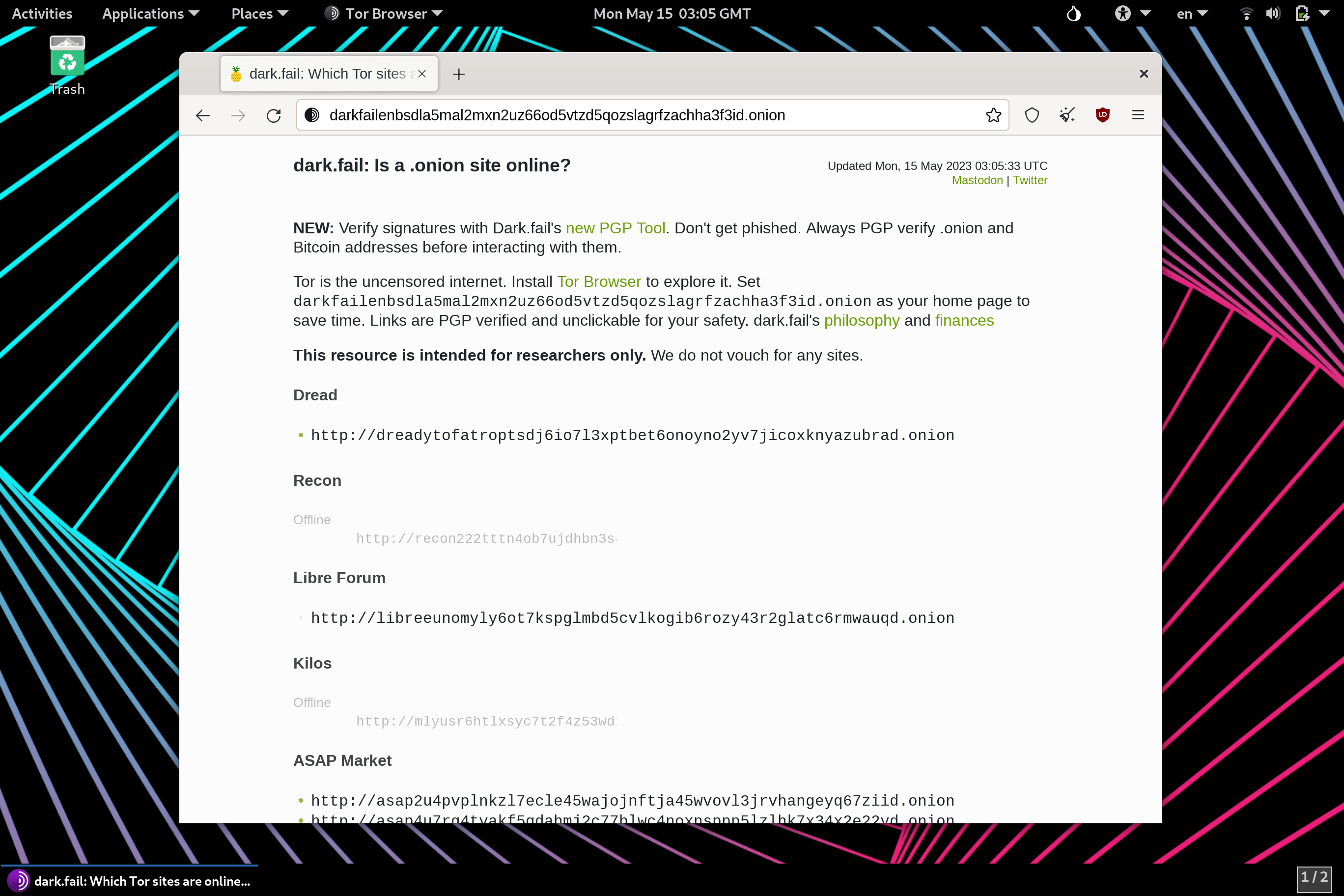
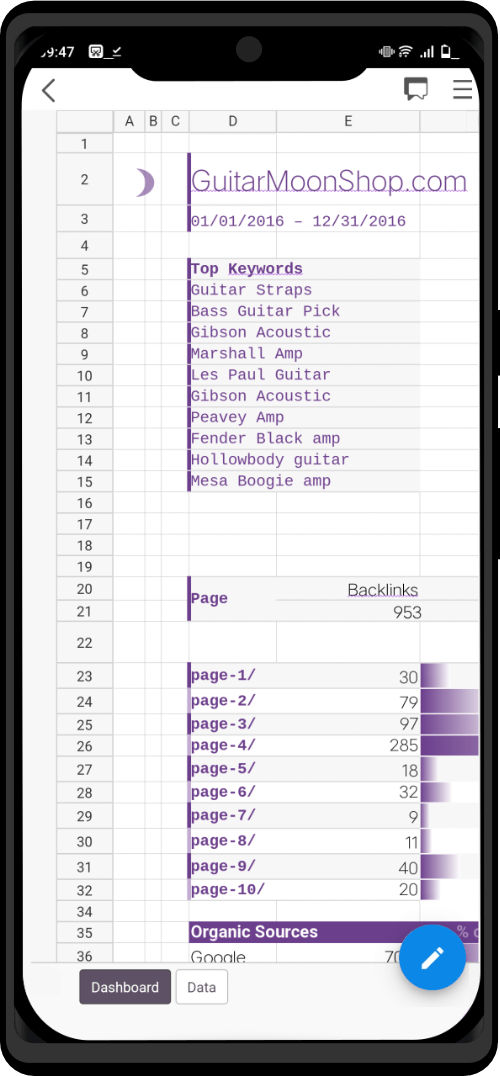
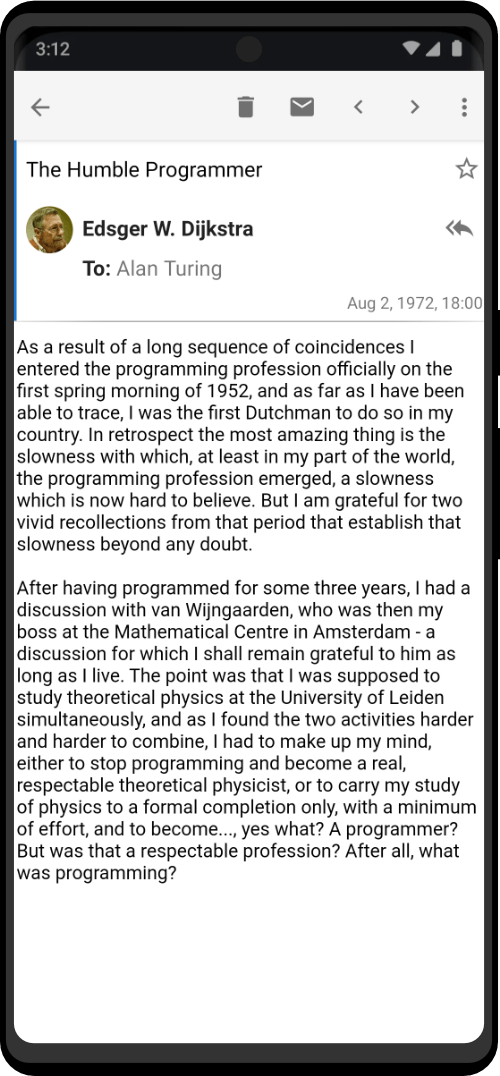
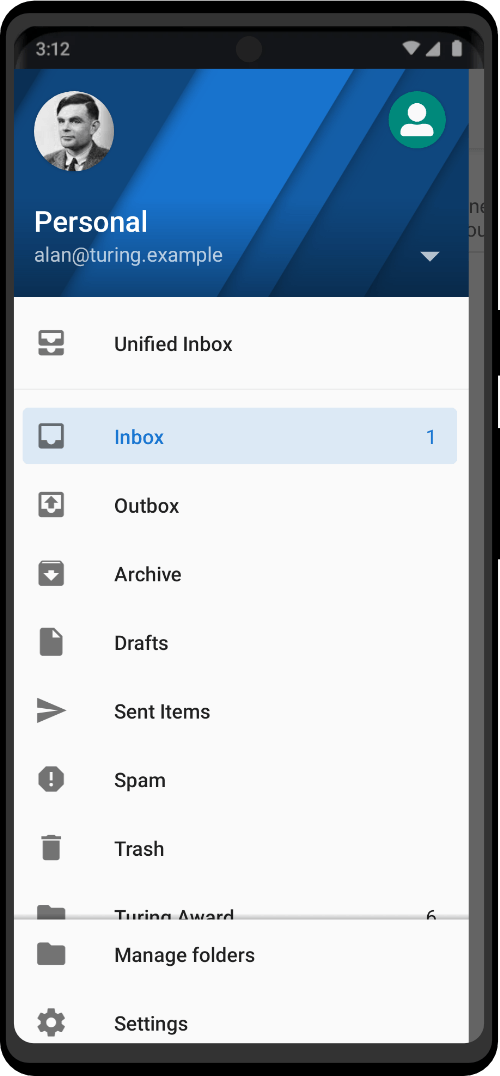
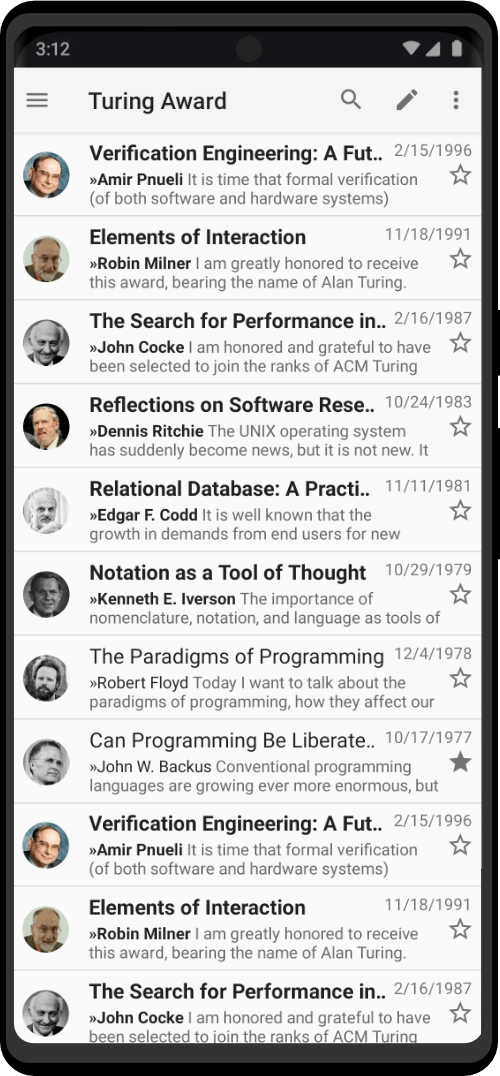
Screenshots
The Zero Trace Pen gets it’s competitive edge from the hardware and modified dev configuration we provide. We keep it light and fast, with no bloatware and remove outdated code routinely.
Want the custom desktop background used above? Download here.
30 Day Guarantee With Free Returns
Bonuses for today’s world
Multilingual Support
Arabic – Azerbaijani – Catalan – Czech – Welsh – Danish – German – Greek – English – Spanish – Persian – Italian – Japanese – Khmer – Korean -Latvian – Bokmal – Dutch – Polish – Portuguese – Russian – Slovak – Slovene – Albanian – Serbian – Swedish – Turkish – Ukrainian – Chinese
Additionally, each language setting comes with it’s own corresponding layout
Automatic Updates
Receive all future security updates for the life of your device – directly on your pen. These updates are made possible:
- Regular updates
- Security patches
- Hardware Modifications
- Zero Trace Support Line
- Ability To Upgrade & Subscribe
Feeling Technical?
Unlock the full potential of your Zero Trace Pen by joining our exclusive VIP membership! As a VIP member, you’ll gain access to cutting-edge tutorials and courses, empowering you to customize your device with advanced configurations and programming. Stay ahead of the curve and make the most out of your privacy-focused device experience.
Real Life Users.
Real Life-Changing Solutions.

- Technology YouTuber @ TechLotto
Lionel spoofed his desktop's IP address & hardware...
“Every website that I am going into is giving me a different IP address…It’s not juts masquerading my IP but it is encrypting it via three different relays. Also, you don’t have to worry about shutting down – once you pull out the pen, everything shut’s down and goes back to normal.”
Rated 5 out of 5
Lionel Odelana
- Technology YouTuber @ MDM4
Michele achieved complete anonymity...
“Dark.fail works just fine on the Zero Trace Pen…it’s one of my favorite places to get the dark web links…the Zero Trace Pen keeps be completely anonymous (tested on Whoer.net)…Protonmail is very compatible with the Pen.”
Rated 5 out of 5
Michele De Martino
- Product Tester @ Shopping W/ Amy
Amy secured her Bitcoin in an encrypted wallet...
“Looks like your normal everyday pen…but’s so much more than a pen…when you plug it in to your computer you achieve ultimate privacy…if you are doing things on the dark web and don’t want to be tracked then this is what you need.”
Rated 5 out of 5
Amy Polack
- Backend Engineer @ Tony Magiar
Tony surfed the dark web without leaving a trace...
“This product is amazing for remaining secure when browsing the internet…the Zero Trace Pen does not run from your regular operating system…I browsed the internet and dark web completely secure.”
Rated 5 out of 5
Tony Magiar
30 Day Guarantee With Free Returns